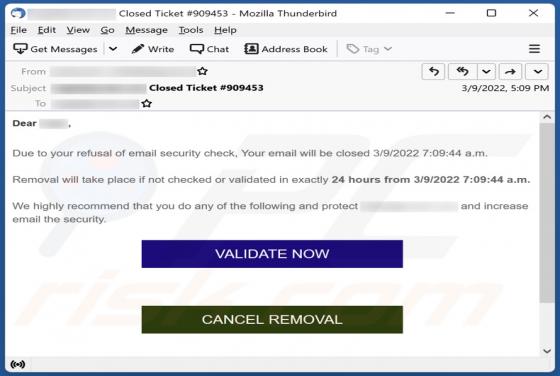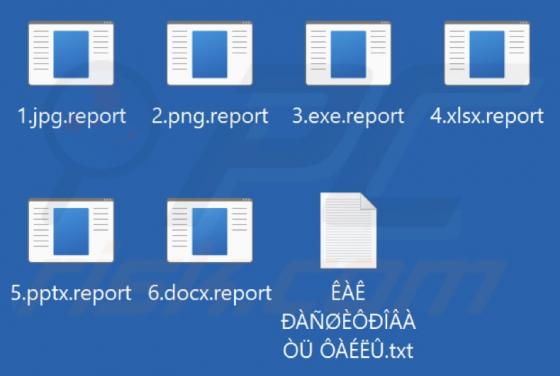
Report Ransomware
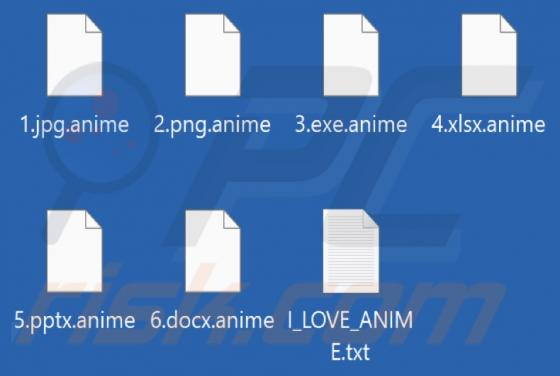
Our team has discovered a ransomware variant called Report while inspecting the malware samples submitted to VirusTotal. It was found that Report is of the ransomware variants that belong to the Xorist family. Once executed, it encrypts files and appends the ".report" extension to filenames. Repo