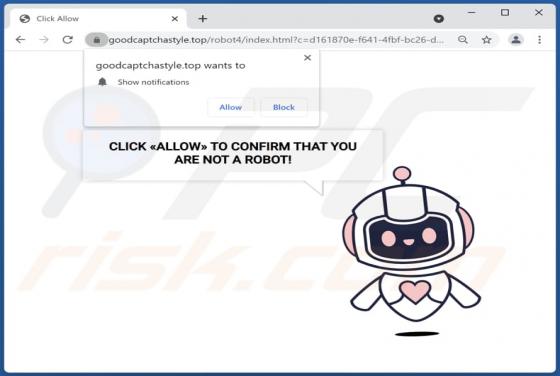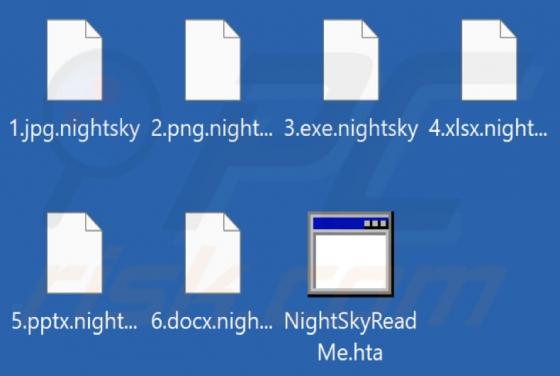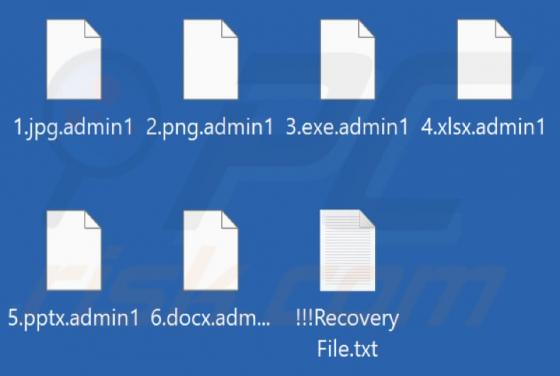
Admin Locker Ransomware
Admin Locker is ransomware designed to encrypt files (make them inaccessible), change extensions of all encrypted files and create the "!!!Recovery File.txt" file (a ransom note). The extension that Admin Locker appends to filenames depends on the ransomware variant. It can append ".admin1", ".adm