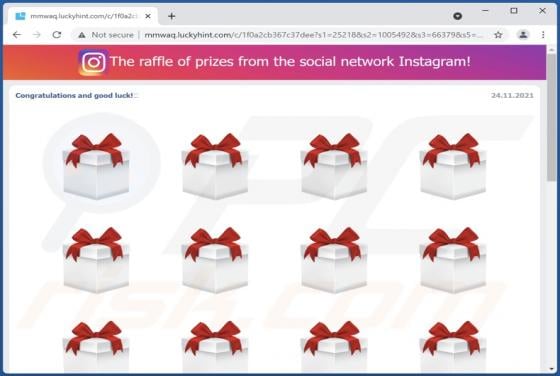
The Raffle Of Prizes POP-UP Scam
"The raffle of prizes" is a scam promoted on various rogue sites. This scheme is presented as a prize raffle from Instagram. It must be emphasized that this giveaway is fake, and it is in no way associated with the Instagram social media platform. Deceptive websites are typically accessed through