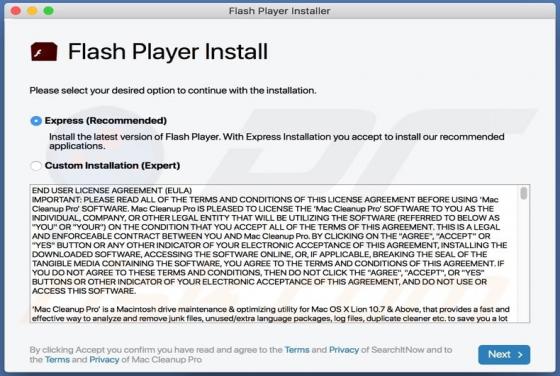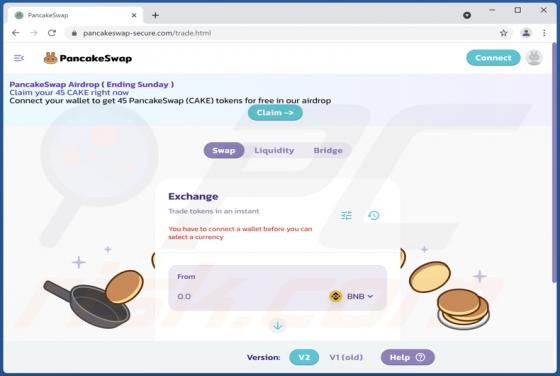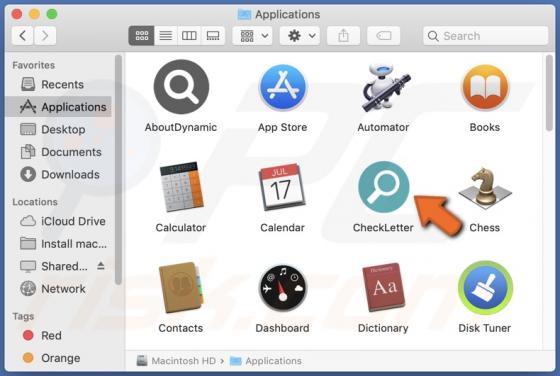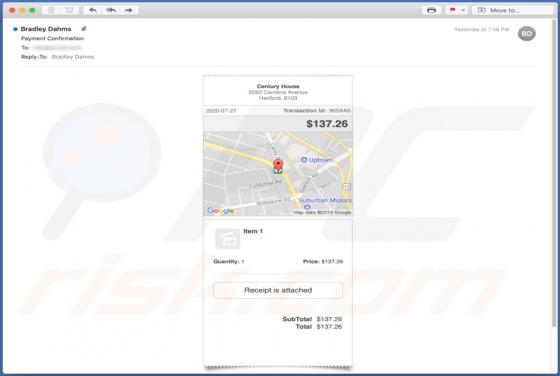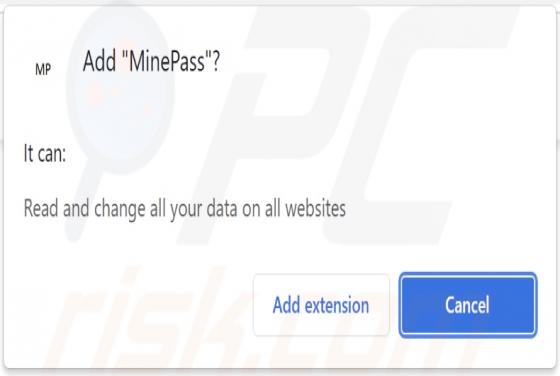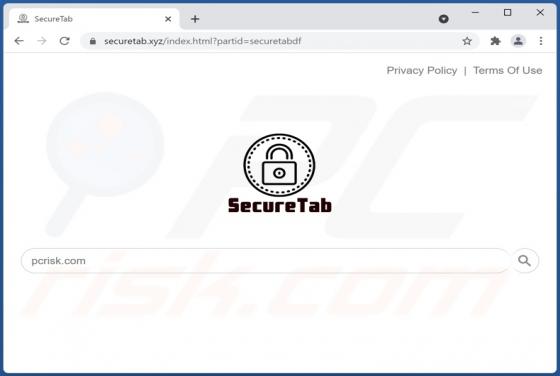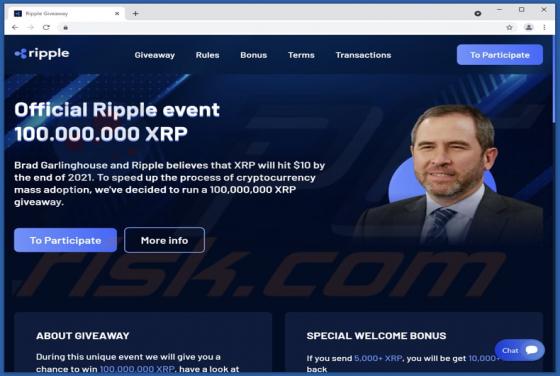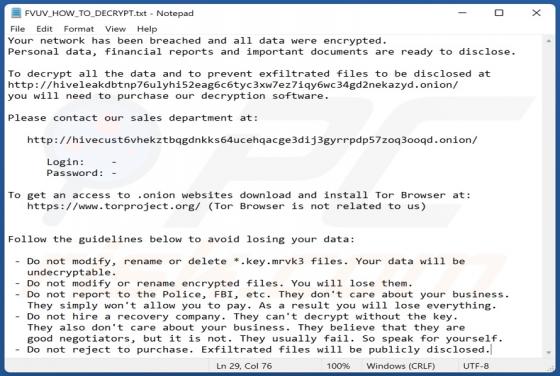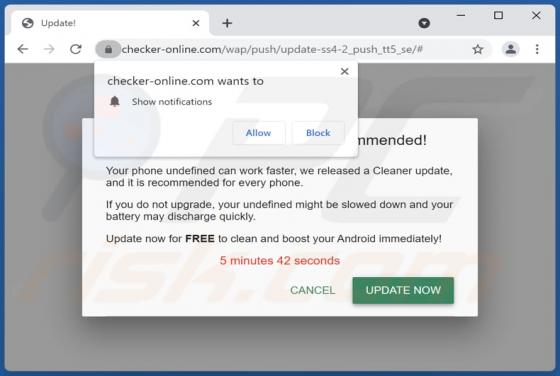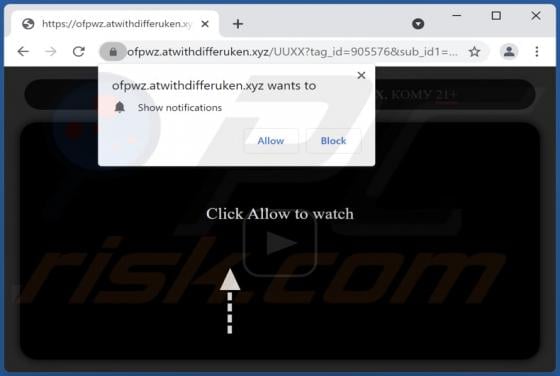
Atwithdifferuken.xyz Ads
Atwithdifferuken[.]xyz is an untrustworthy page designed to trick visitors into agreeing to receive notifications from it and redirect them to potentially malicious pages. It is pretty similar to checker-online[.]com, myfreshspot[.]com, brainychoose-captcha[.]top, and many other sites that users d