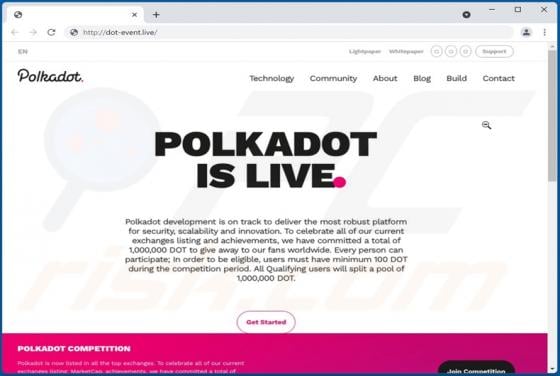
Polkadot Giveaway Scam
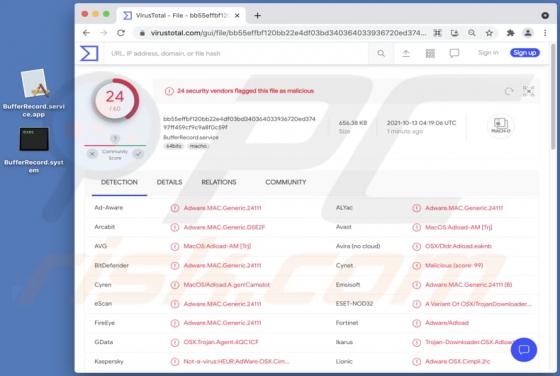
"Polkadot giveaway" is the name of a scam promoted on various untrustworthy sites. The scheme promises to triple the DOT (Polkadot) cryptocurrency users submit to the "competition". However, any amount users transfer to the digital wallet address provided by this scam - will be simply lost, as it