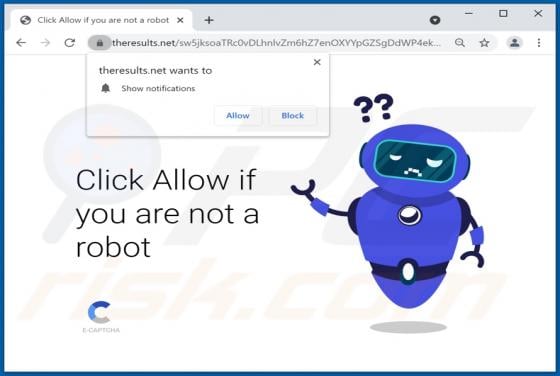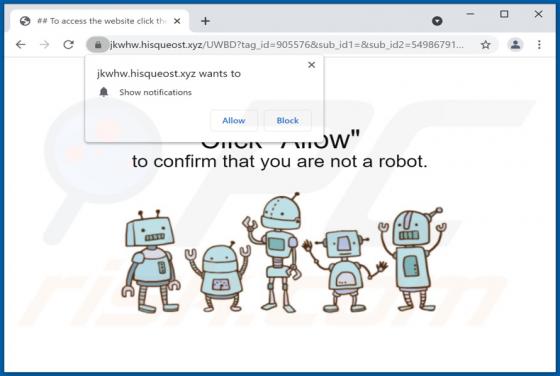
Hisqueost.xyz Ads
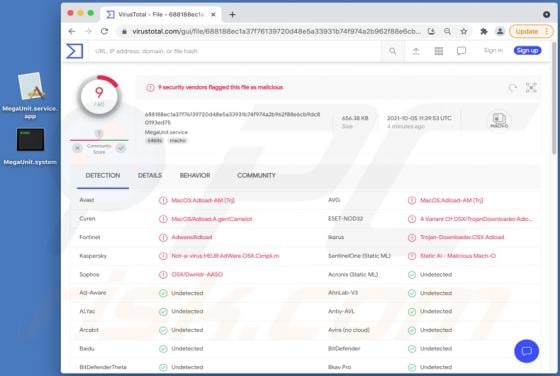
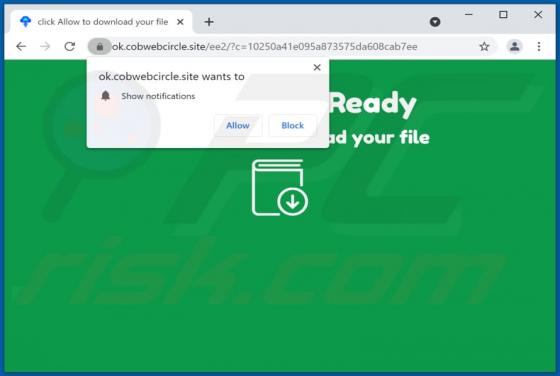
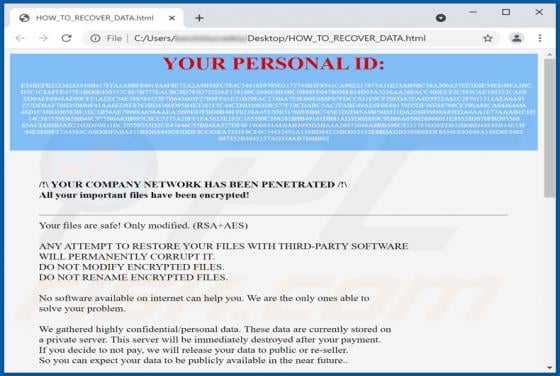
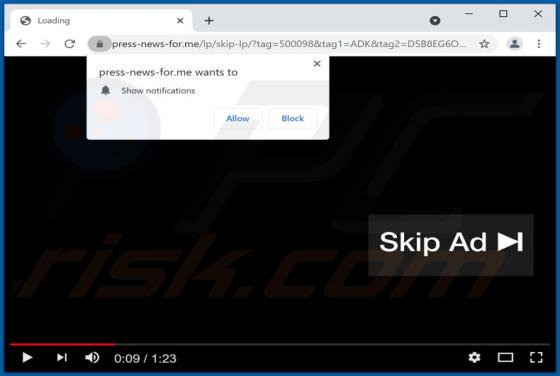
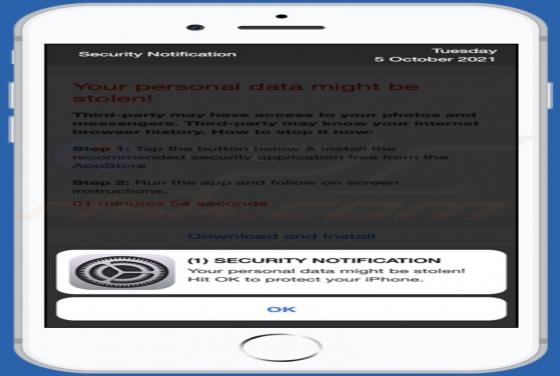
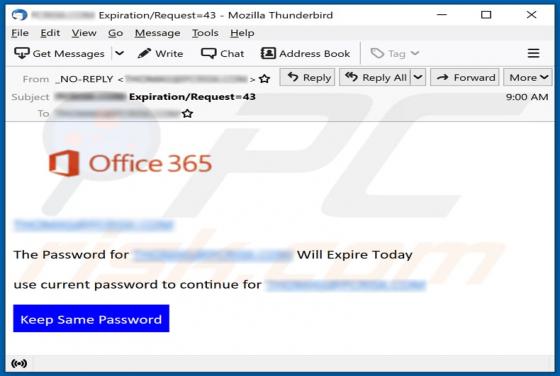
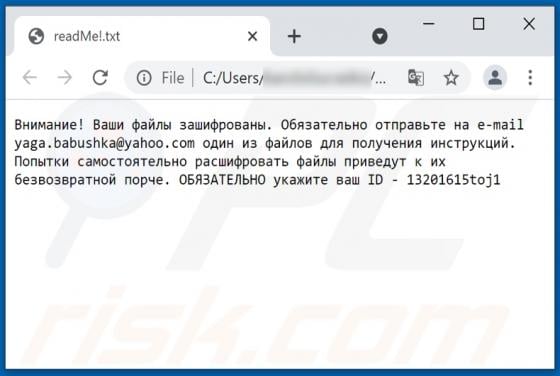
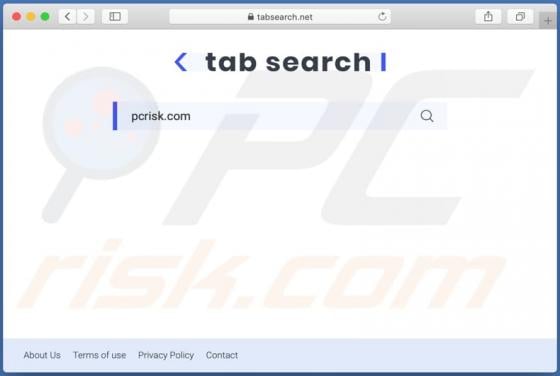
Akin to theresults.net, more*.biz, liffsandupa.xyz, goodsurvey.site, and countless others, hisqueost[.]xyz is a rogue site. This page is designed to load questionable material and/or redirect visitors to different (likely unreliable or malicious) websites. Most users enter such webpages through r