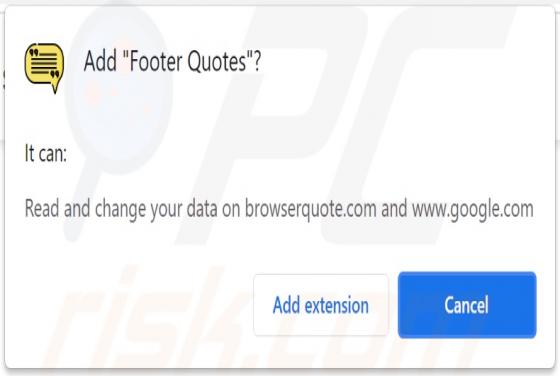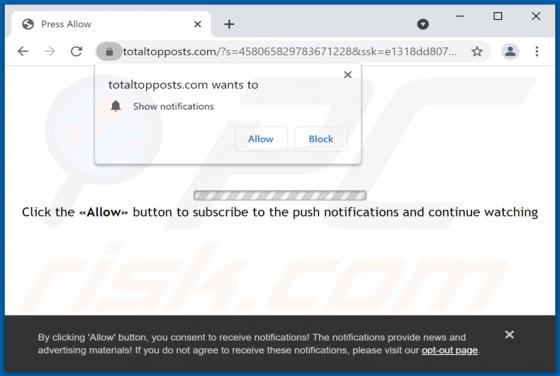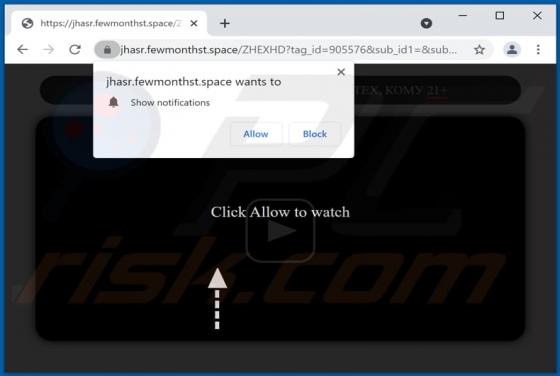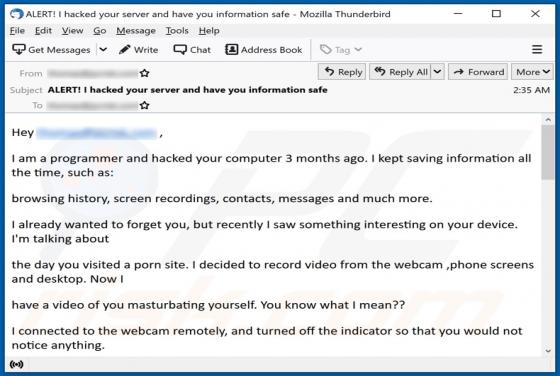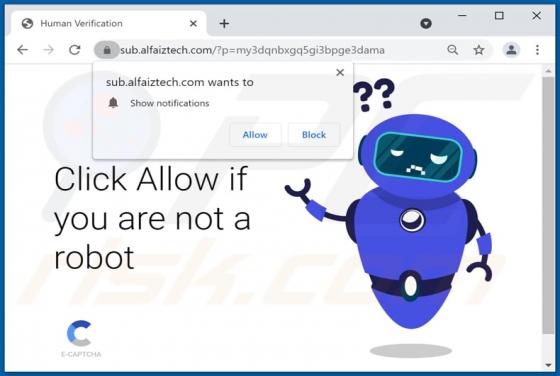
Alfaiztech.com Ads
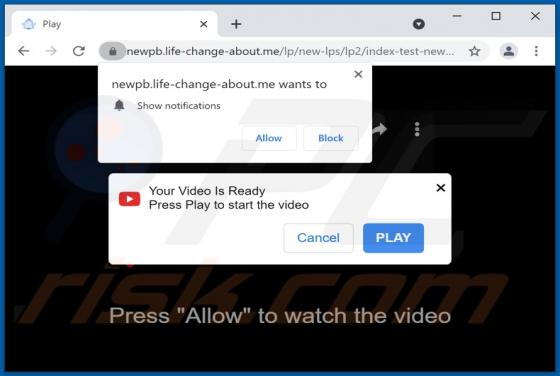
Alfaiztech[.]com promotes questionable pages and uses a clickbait technique to trick visitors into allowing it to show notifications. This site is similar to life-change-about[.]me, fewmonthst[.]space, news-keheza[.]cc, and hundreds of other pages. Alfaiztech[.]com is promoted via deceptiv