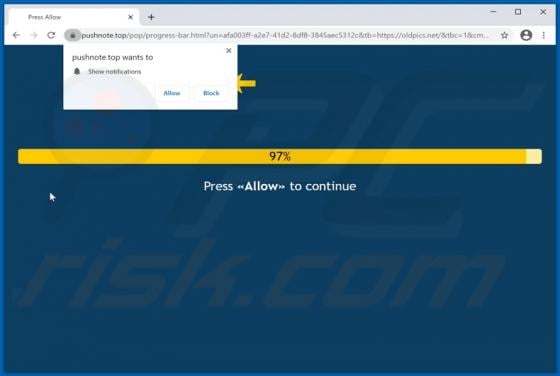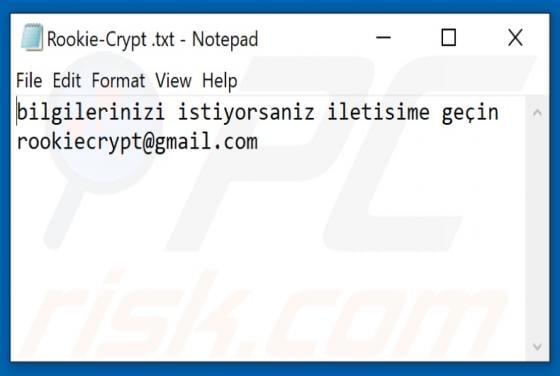
Rookie Crypt Ransomware
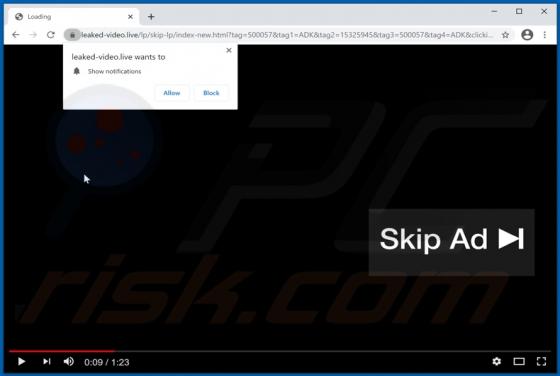
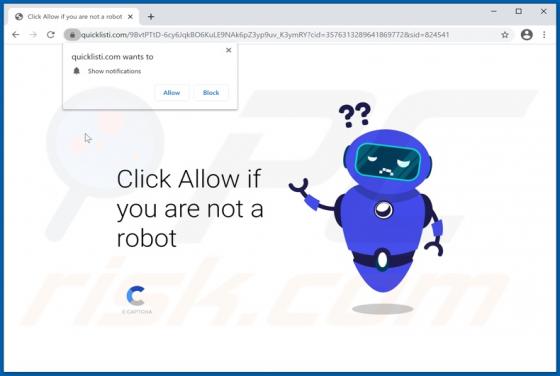
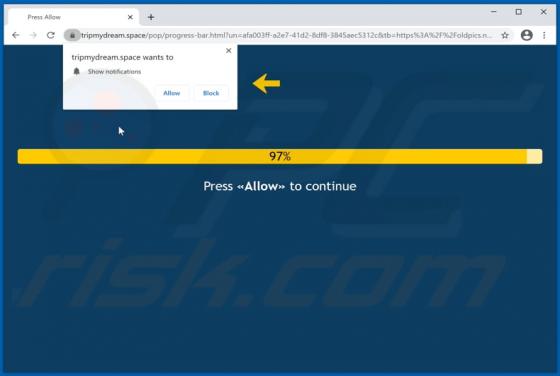
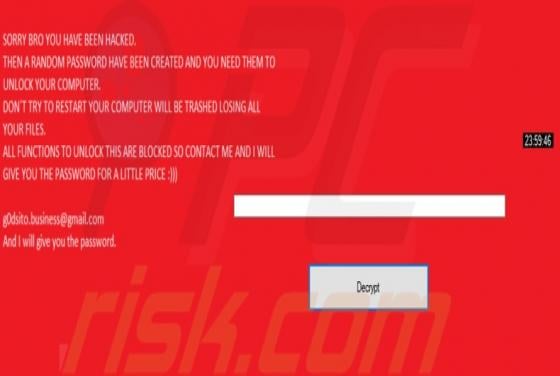
Rookie Crypt (also known as RookieCrypt) is a ransomware-type program. This malware operates by encrypting data and demands payment for the decryption. In other words, victims are unable to use the files affected by Rookie Crypt, and they are asked to pay - to recover access to their data. During