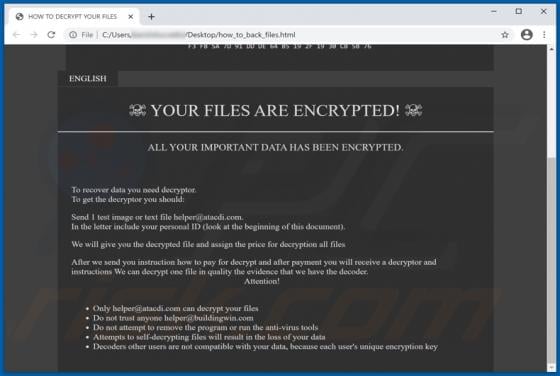
Ielock Ransomware
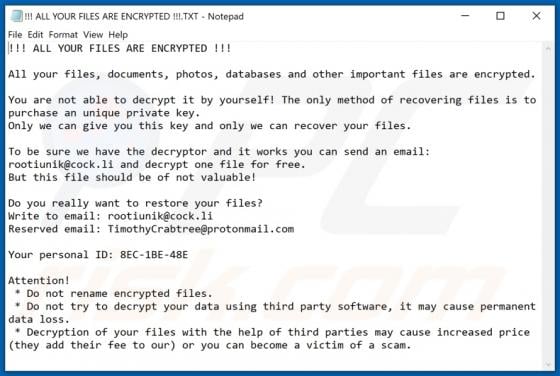
Ielock is a malicious program, which is part of the GlobeImposter ransomware family. This malware is designed to encrypt data and demand payment for the decryption. In other words, victims are unable to access the files affected by Ielock, and they are asked to pay - to recover access/use of thei