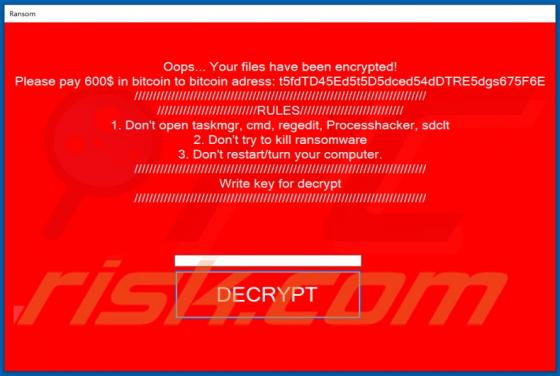
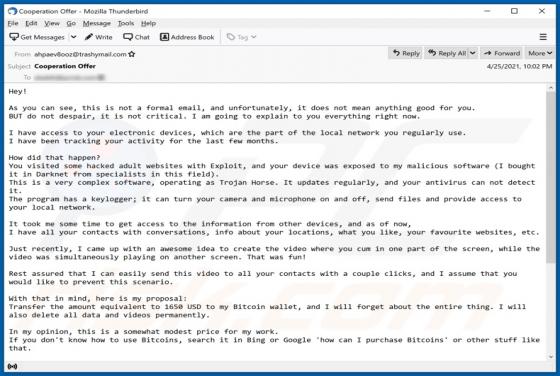
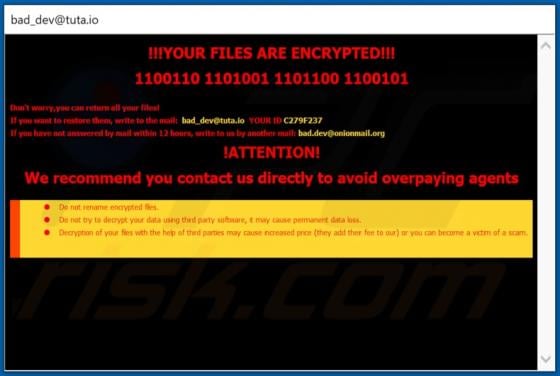
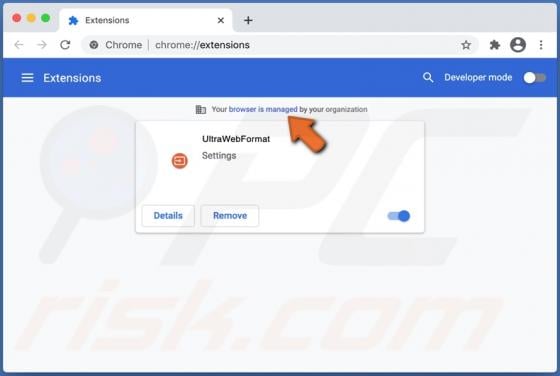
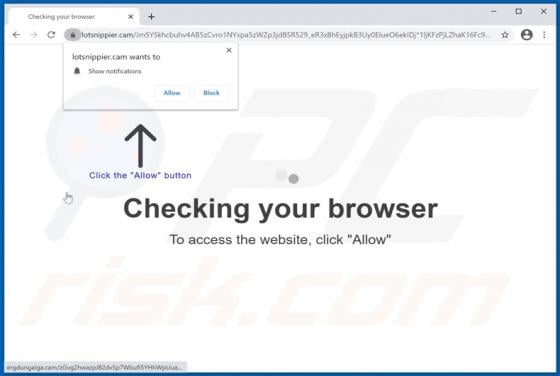
MailEx Scam
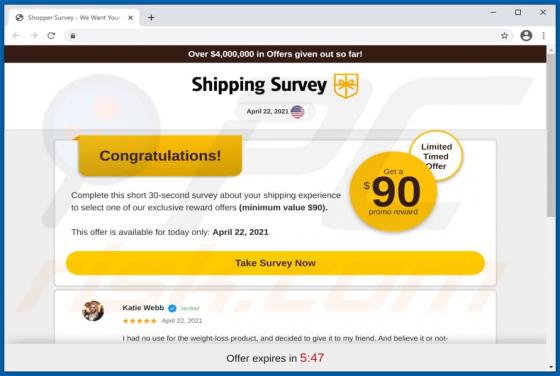
Scammers behind this phishing campaign use email to trick users into providing personal information. They send emails offering users to participate in a fake survey and get a certain prize in return. After completing a survey, visitors are asked to enter personal information to claim their "rewar