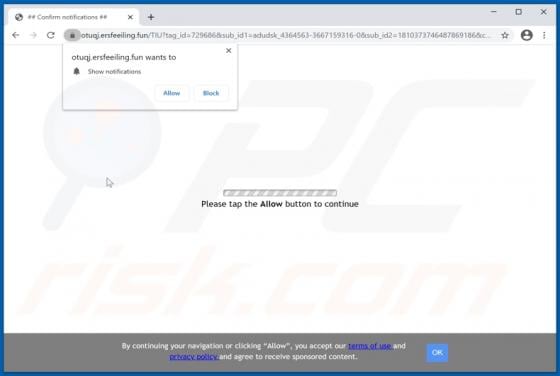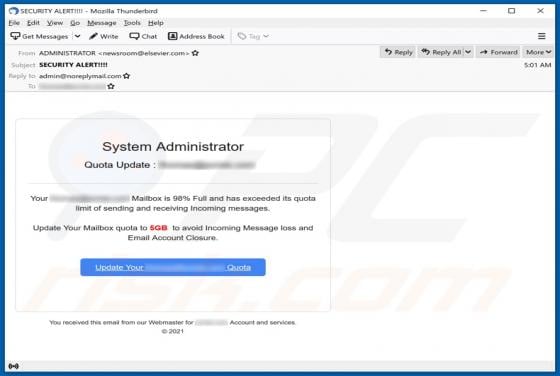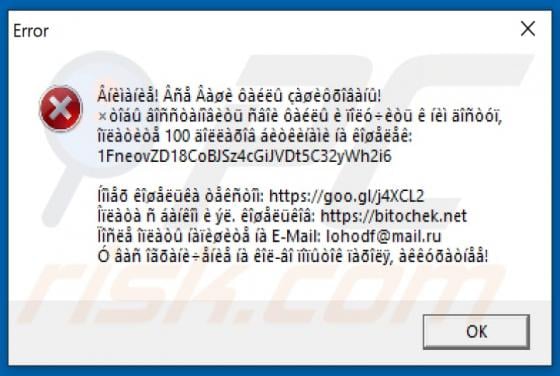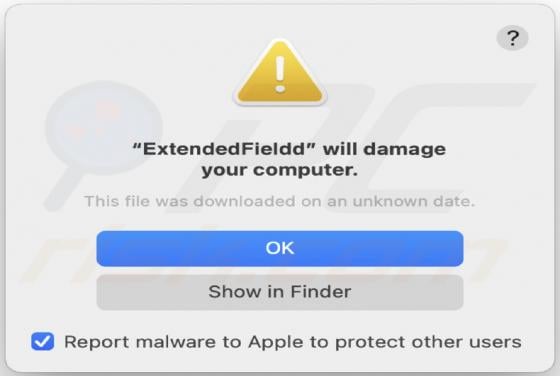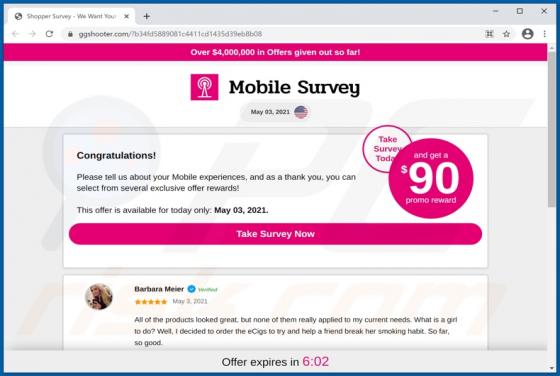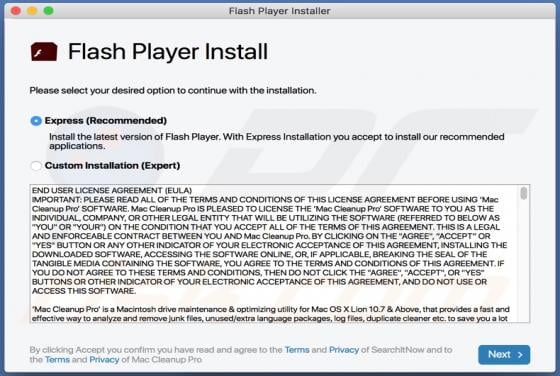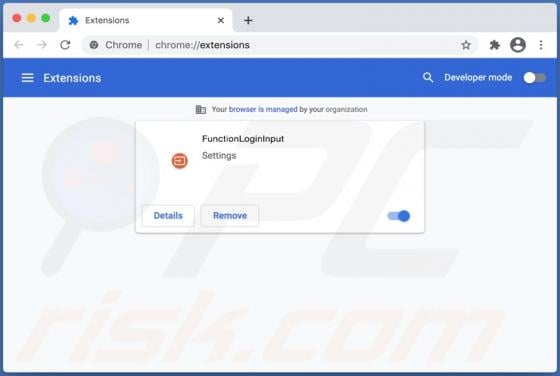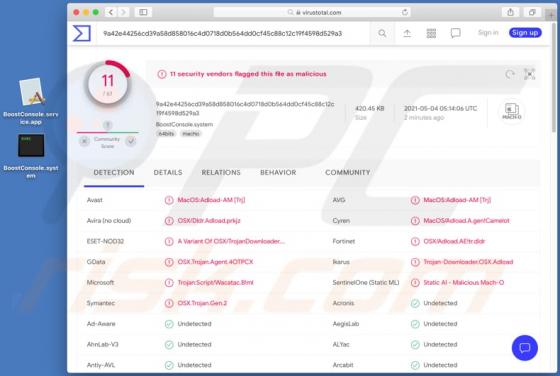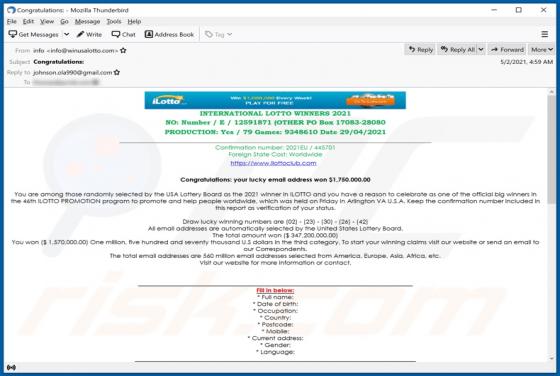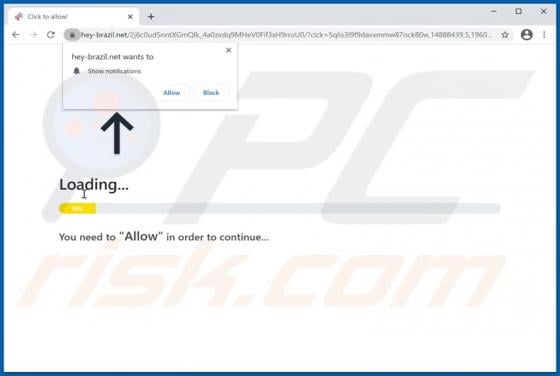
Hey-brazil.net Ads
Hey-brazil[.]net is a website designed to load deceptive content and promote various untrustworthy websites. It is important to mention that users do not visit pages like hey-brazil[.]net intentionally. More precisely, these pages get opened when users click some shady advertisements, visit other