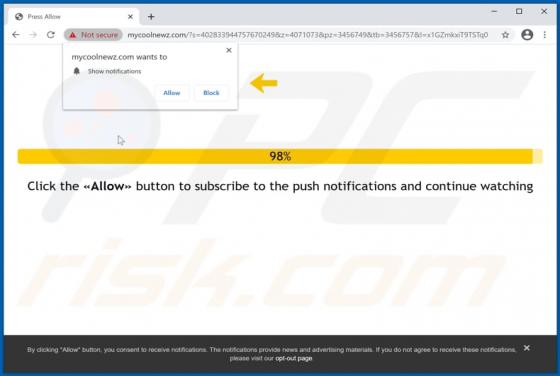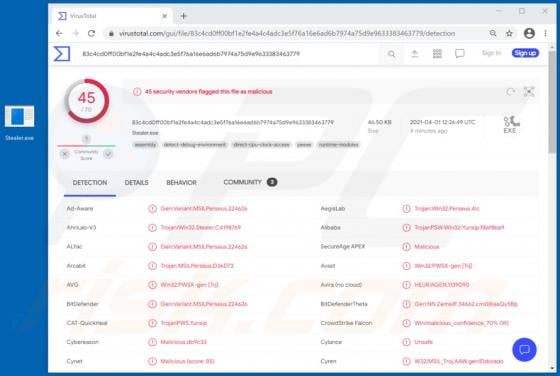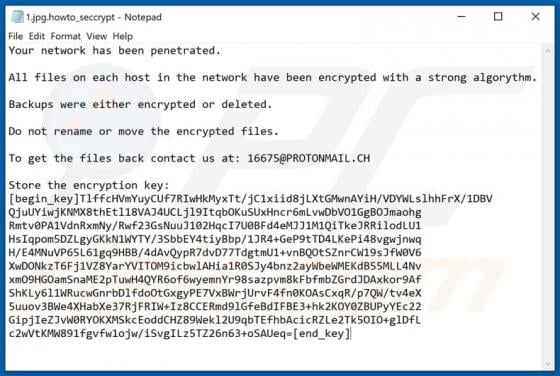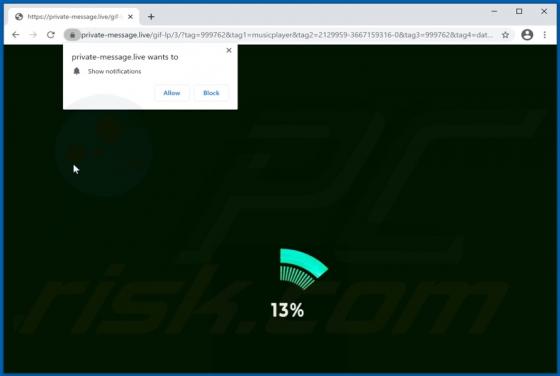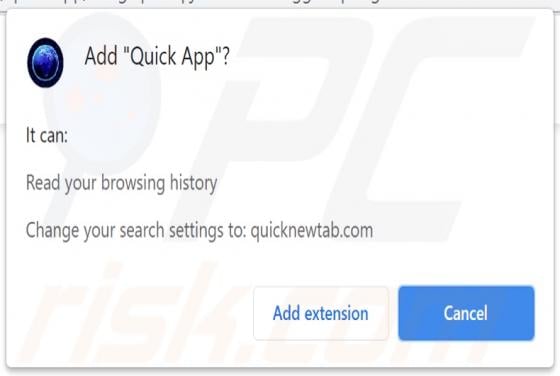
Quick App Browser Hijacker
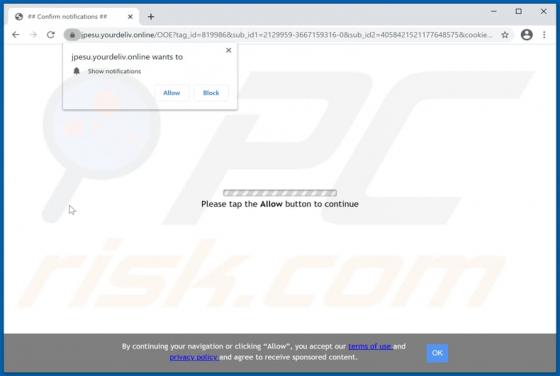
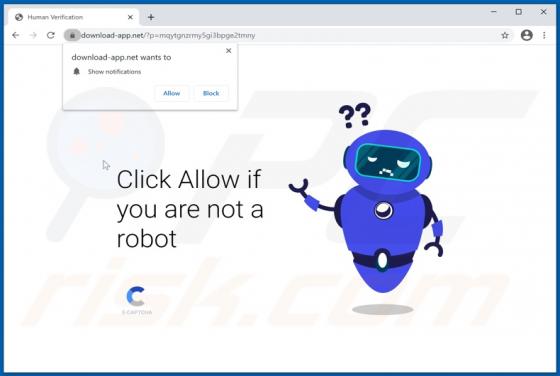
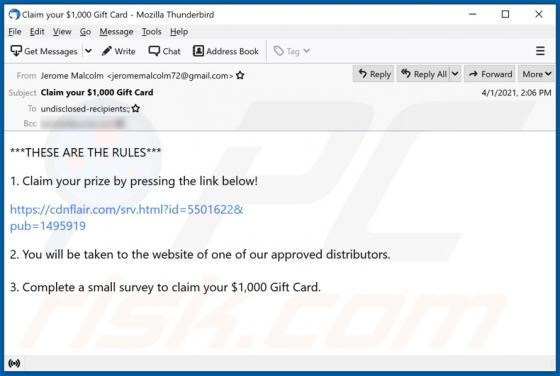
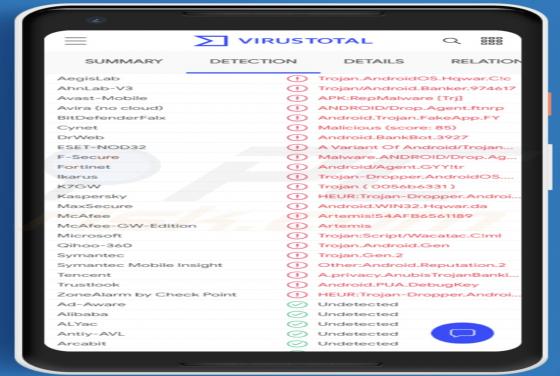
Quick App is dubious software categorized as a browser hijacker. It operates by promoting the quicknewtab.com fake search engine through modification of browser settings. Additionally, Quick App monitors users' browsing habits and collects vulnerable data. Since most users download/install browse