Chrome Tools Adware
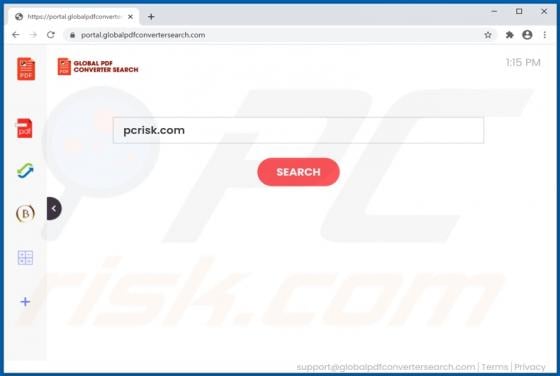
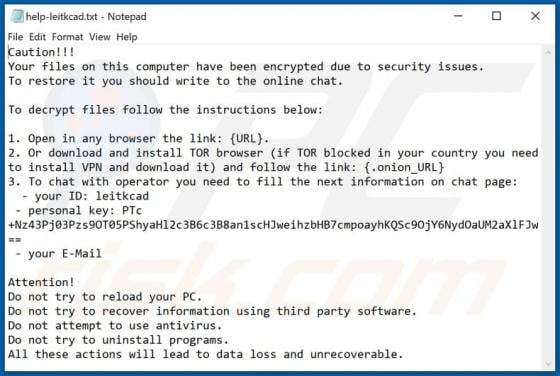
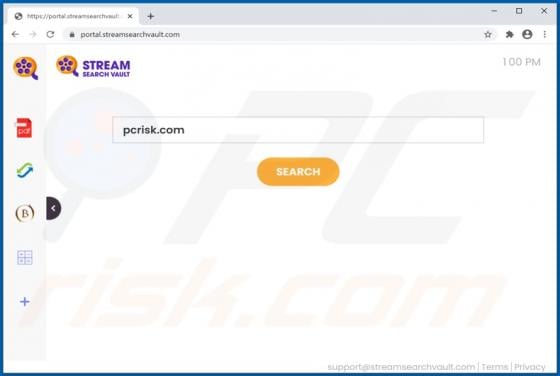
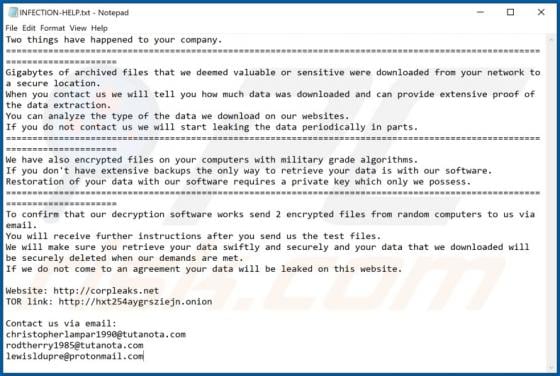
Chrome Tools is rogue software classified as adware. Following successful installation, it operates by running intrusive advertisement campaigns. I.e., Chrome Tools delivers various dubious and harmful ads. Additionally, this adware has data tracking capabilities, which are used to collect browsi