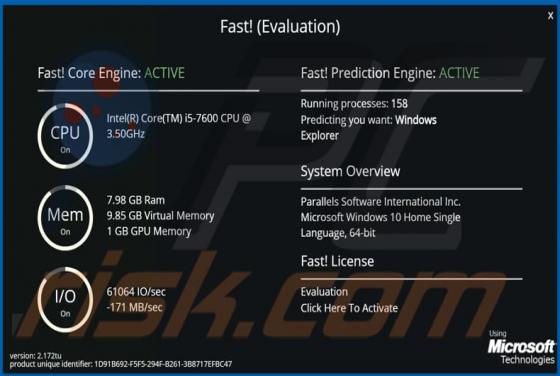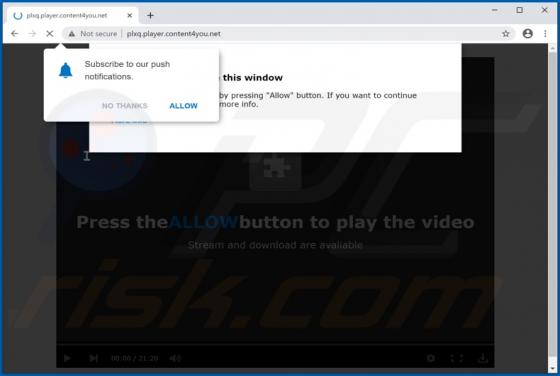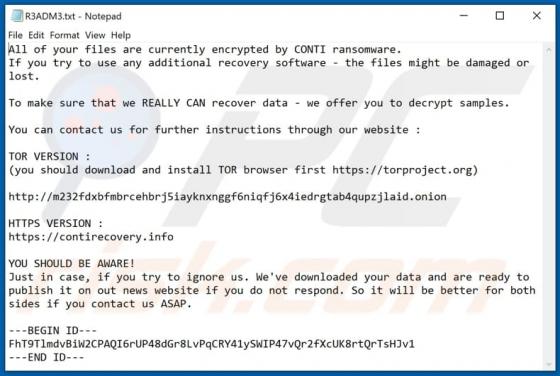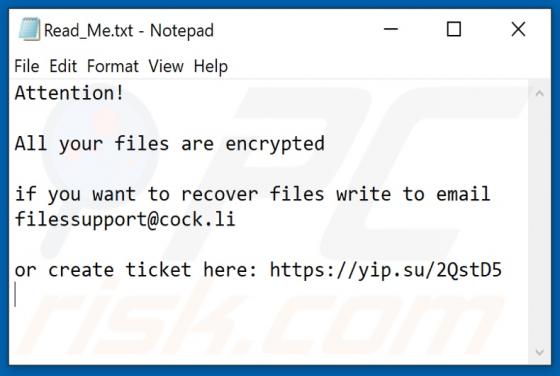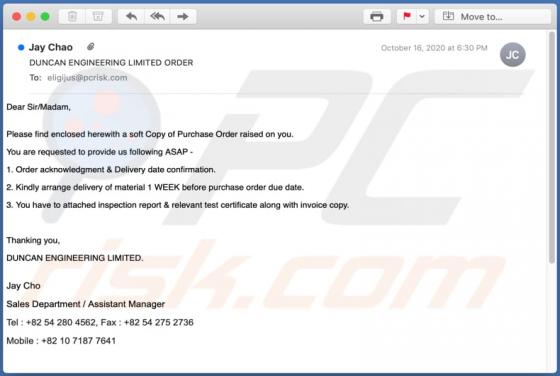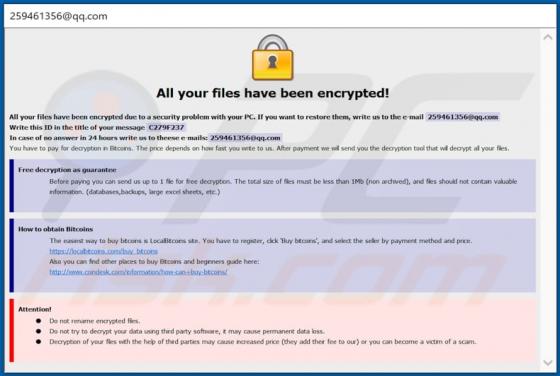
ProgressElemnt Adware (Mac)
ProgressElemnt is adware which serves various advertisements and also operates as as a browser hijacker, promoting the address of a fake search by modifying certain browser settings. Additionally, this app might be designed to collect various data. Note that users often download and install adw