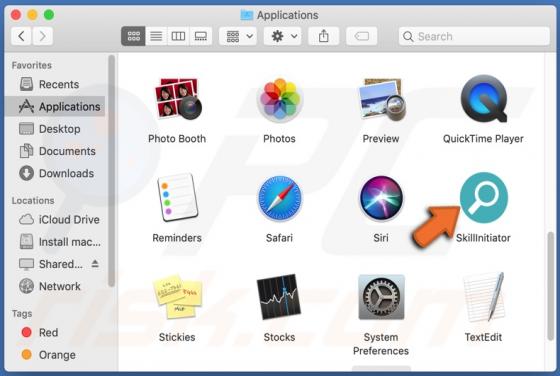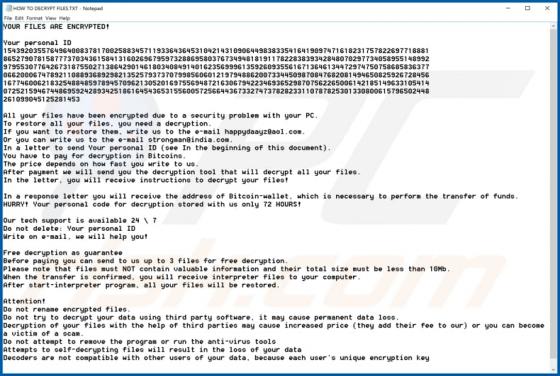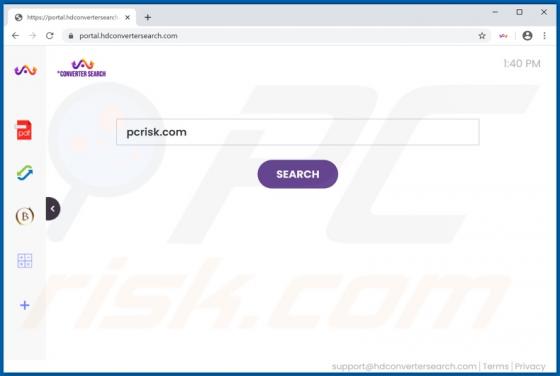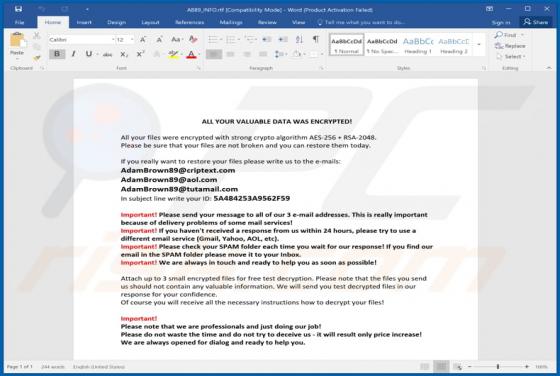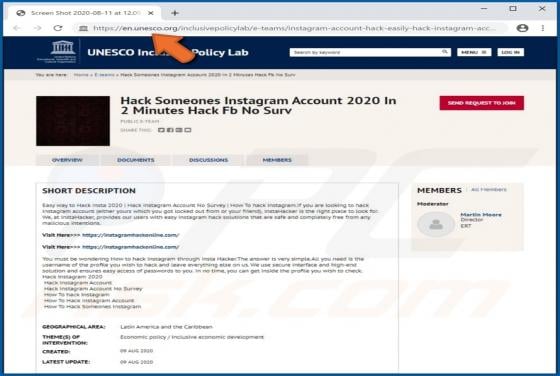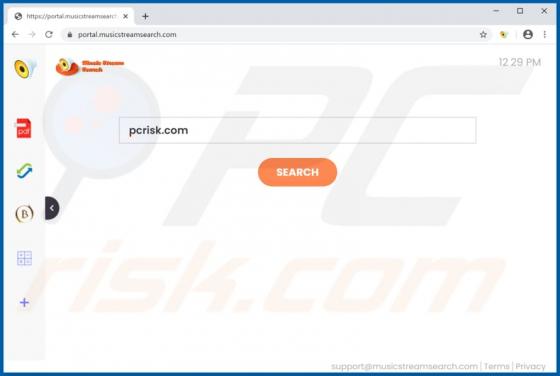
MusicStreamSearch Browser Hijacker
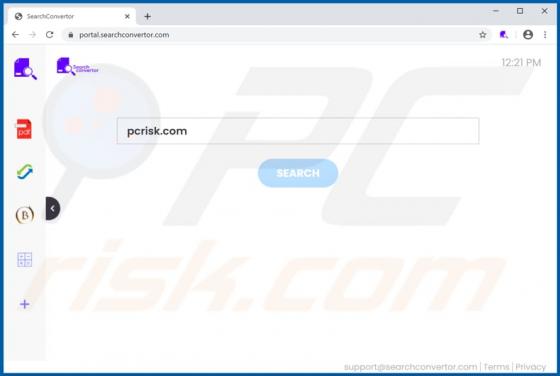
MusicStreamSearch is a potentially unwanted application (PUA), a browser hijacker which changes certain browser settings to the address of a fake search engine - in this case, feed.musicstreamsearch.com or portal.musicstreamsearch.com. These apps often gather details relating to users' browsing h