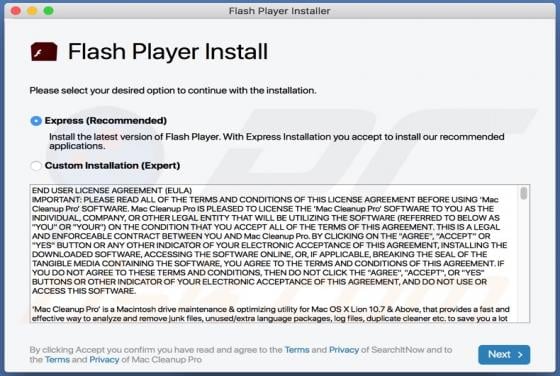
GeneralBoardSearch Adware (Mac)
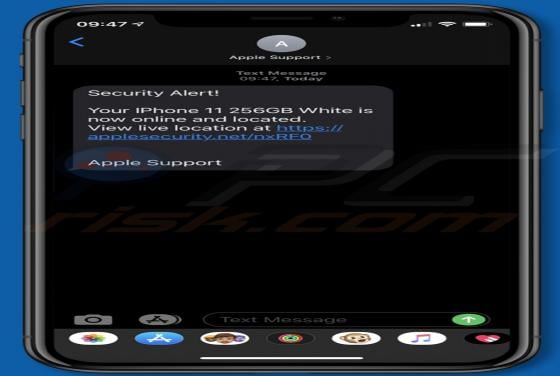
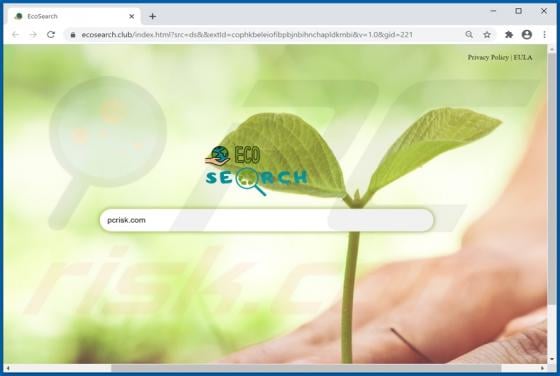
GeneralBoardSearch is designed to display advertisements and promote the address of a fake search engine by modifying certain browser settings. This app is classified as adware and a browser hijacker. In most cases, users download and install apps of this type inadvertently and, for this reason