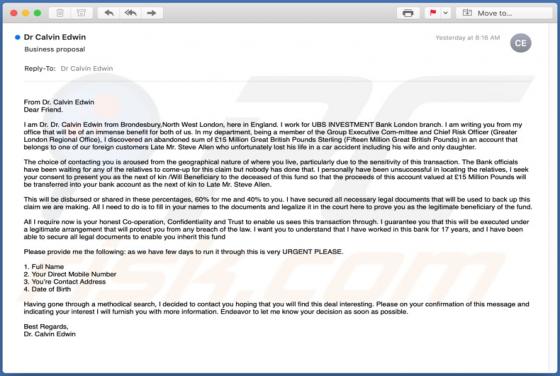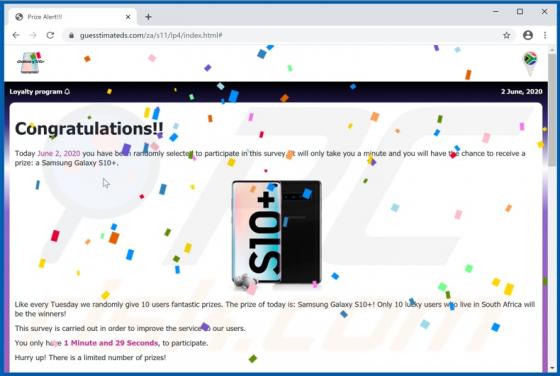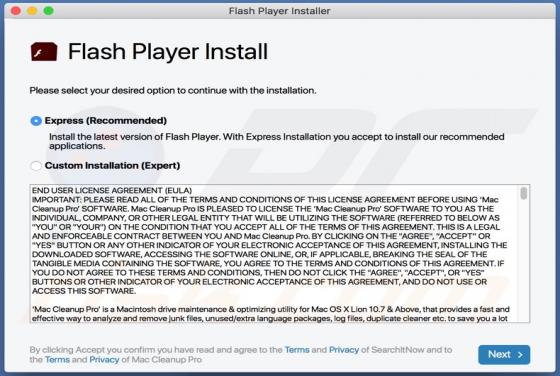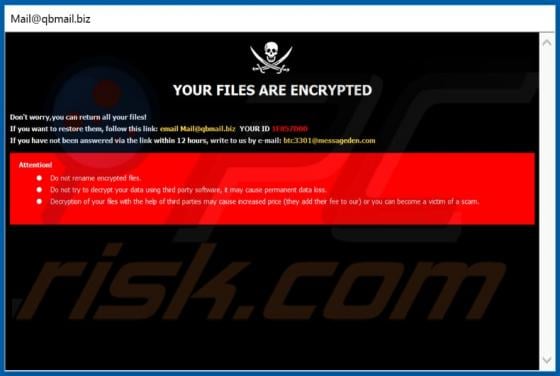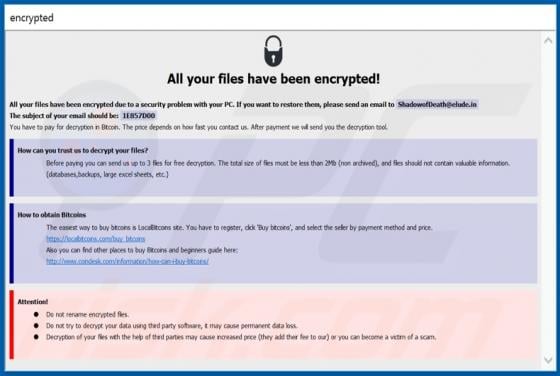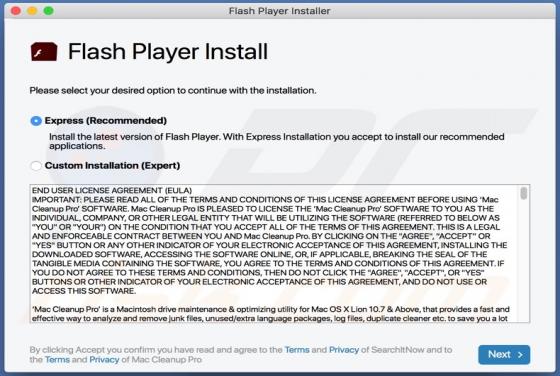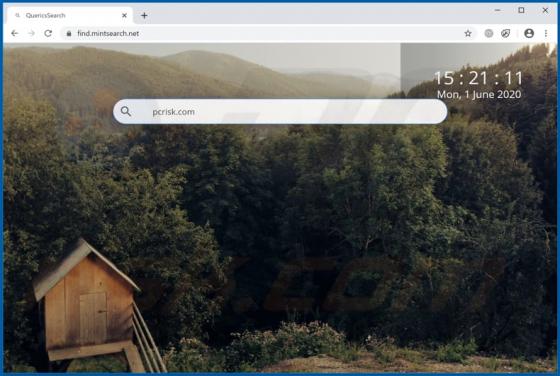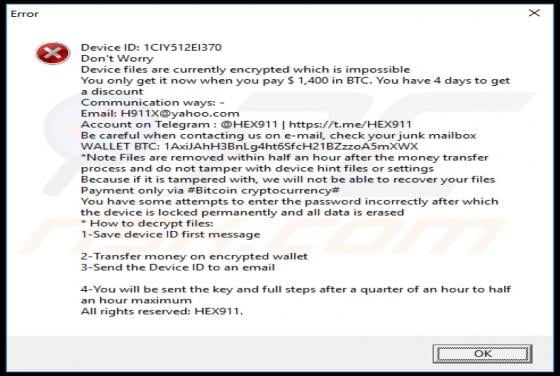
Dupzom Trojan
Dupzom is a Trojan which operates as a malware downloader. It causes chain infections by downloading and executing malicious files that infect computers with additional malware. Dupzom can cause installation of ransomware, remote administration/access Trojans (RATs), cryptocurrency miners, and oth