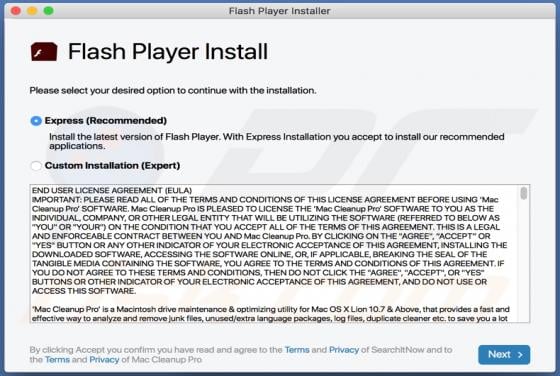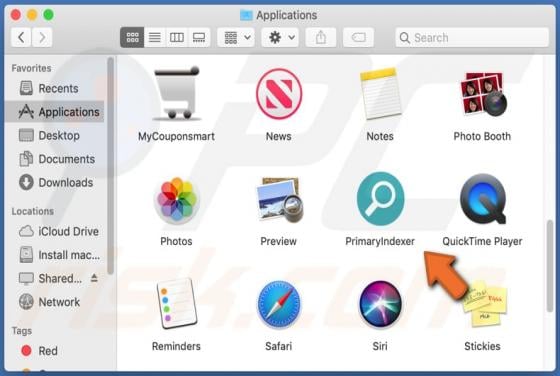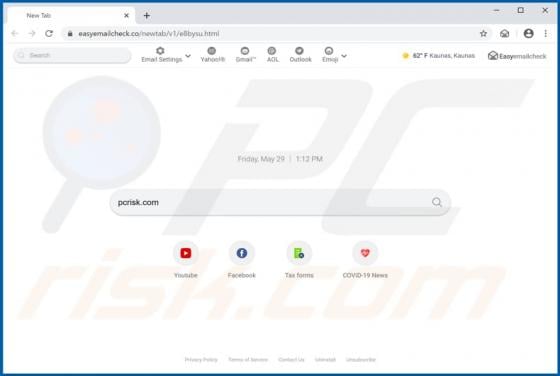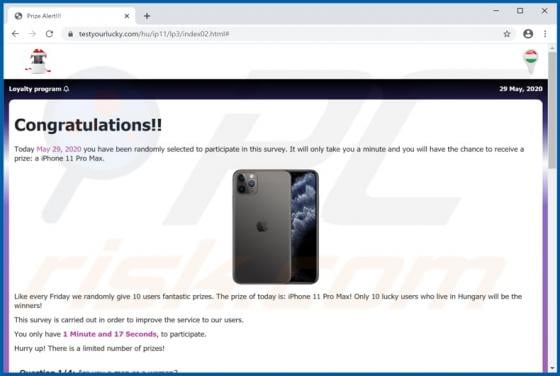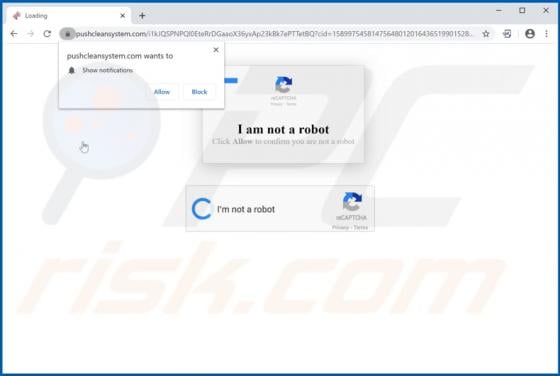
Pushcleansystem.com Ads
pushcleansystem[.]com is a rogue website that promotes (and opens) other bogus websites, or displays dubious content. Some examples of other web pages similar to pushcleansystem[.]com include checkvd[.]com, enerativearea[.]pro and oawhaursaith[.]com. Most users do not visit these web pages intent