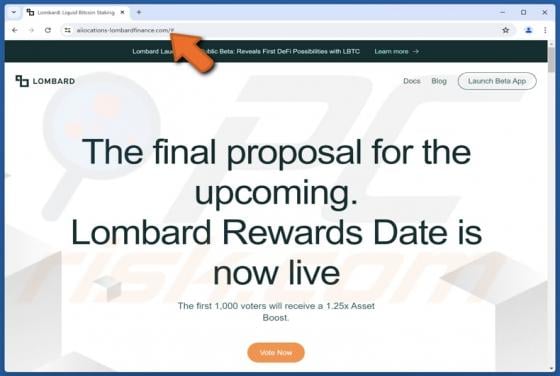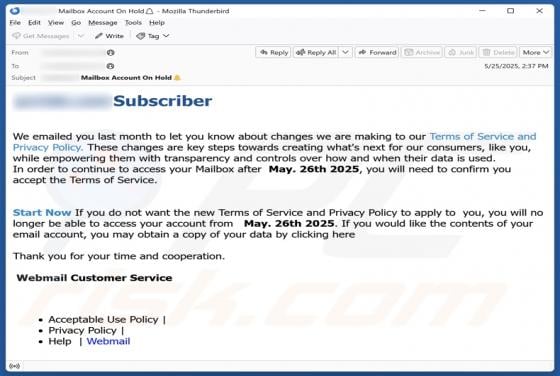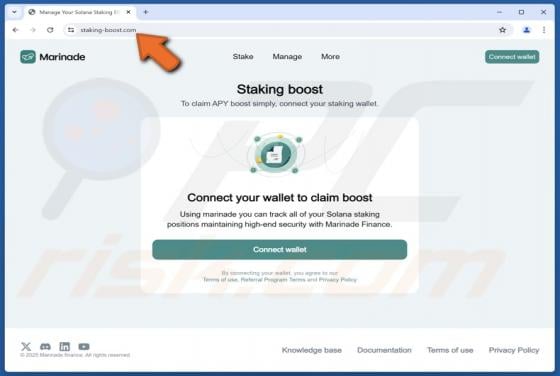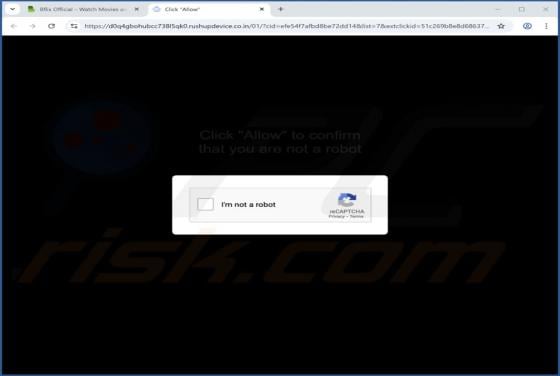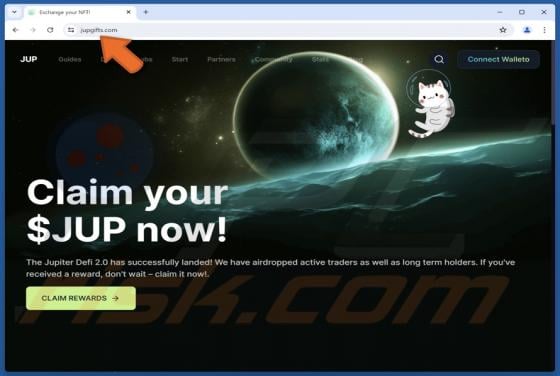
Jupiter (JUP) Rewards Scam
"Jupiter (JUP) Rewards" is a phishing scam we discovered during a routine investigative session. It impersonates the Jupiter (jup.ag) platform and lures victims with a fake reward. The goal is to deceive them into disclosing their wallet log-in credentials. IMPORTANT NOTE: We do not review c