FuxSocy ENCRYPTOR Ransomware
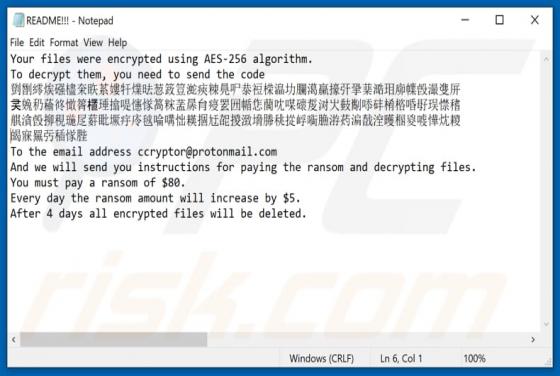
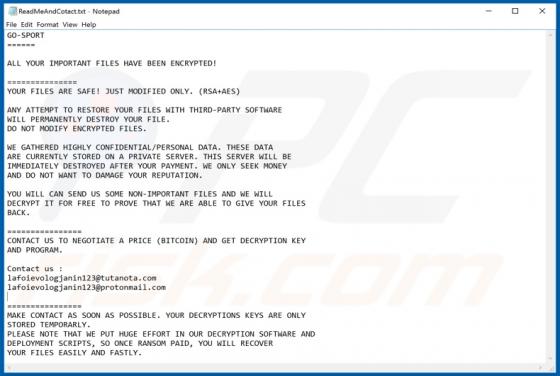
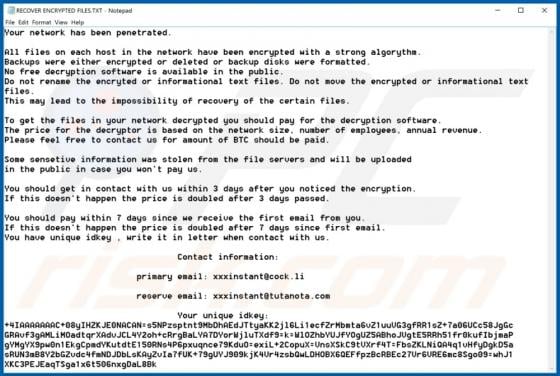
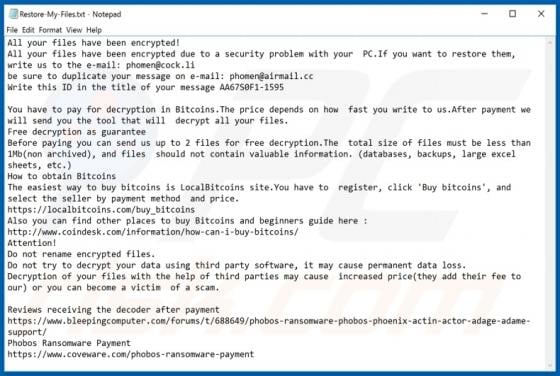
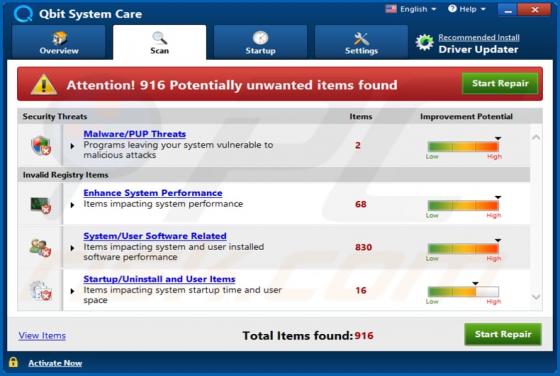
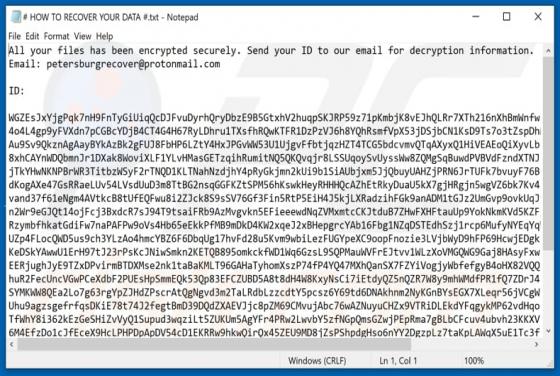
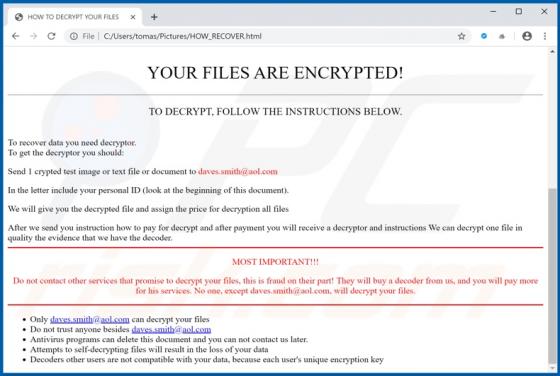
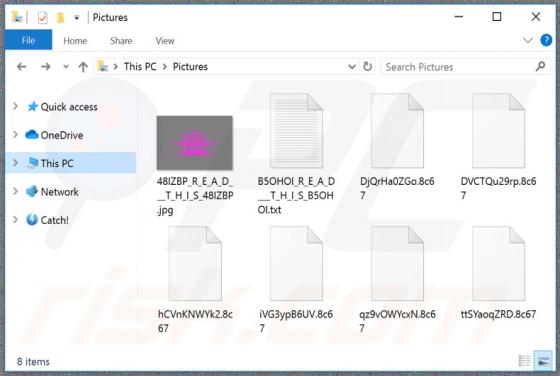
Discovered by Vitali Kremez, FuxSocy ENCRYPTOR is malicious software, classified as ransomware. This malware emulates Cerber ransomware. It operates by encrypting data and demanding ransom payments for decryption. During FuxSocy ENCRYPTOR encryption, each file is renamed with a randomized filename