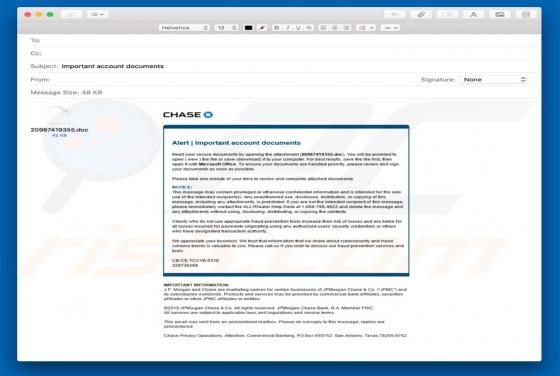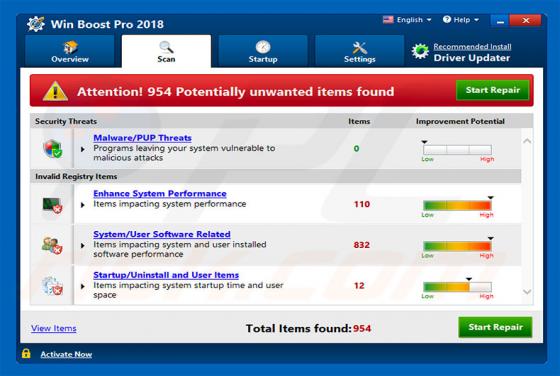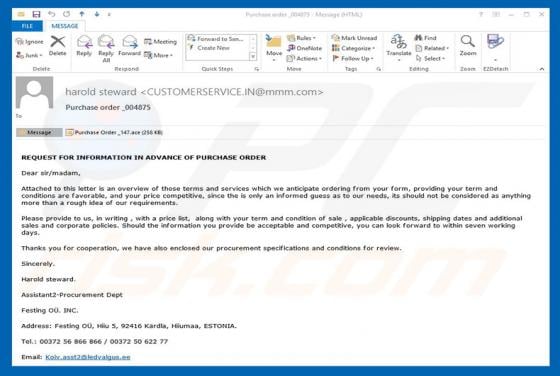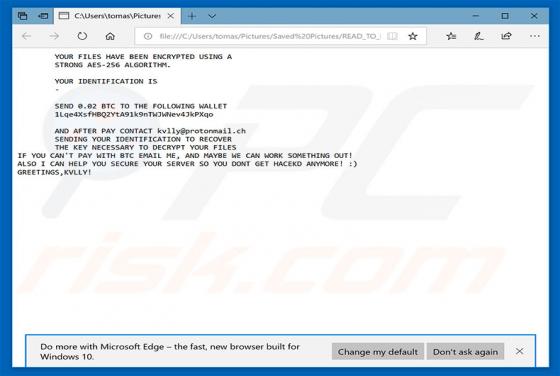
YeaDesktop Adware
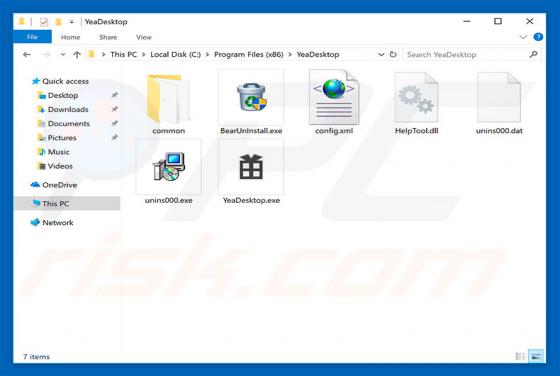
YeaDesktop is a rogue application that typically infiltrates systems without users' consent. Furthermore, it generates intrusive advertisements and collects sensitive information. For these reasons, YeaDesktop is categorized as adware and a potentially unwanted application (PUA). YeaDesktop