SHRUG Ransomware
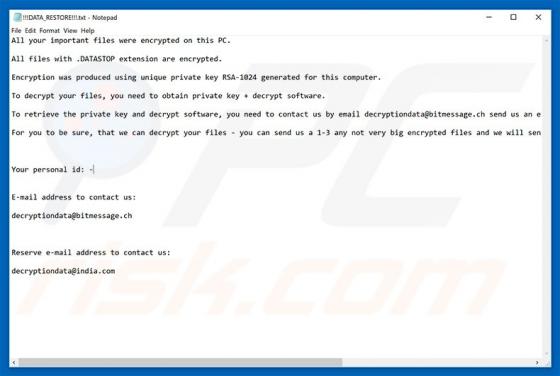
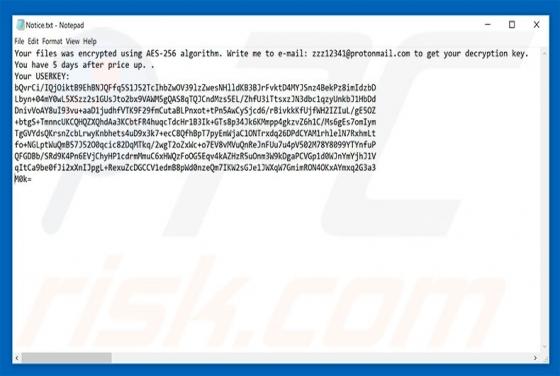
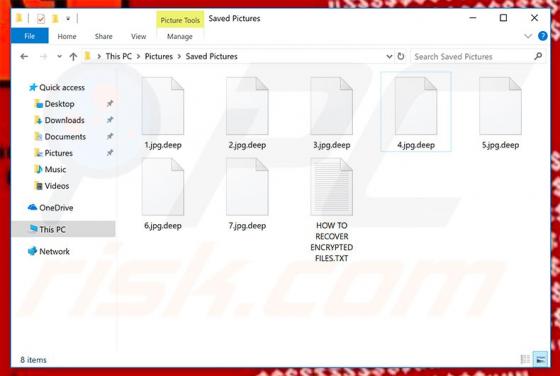
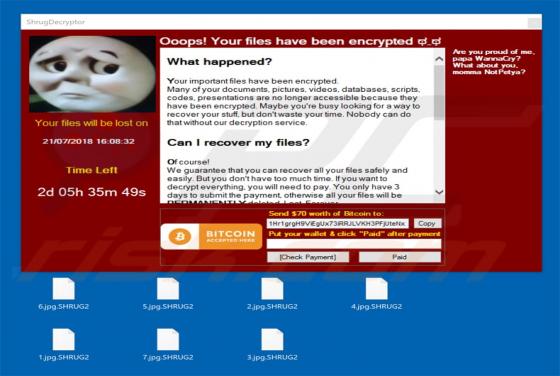
Discovered by MalwareHunterTeam, SHRUG is a ransomware-type virus that stealthily infiltrates the system and encrypts most stored data. In doing so, this malware appends filenames with the ".SHRUG" extension (e.g., "sample.jpg" is renamed to "sample.jpg.SHRUG"). Encrypted data immediately becomes