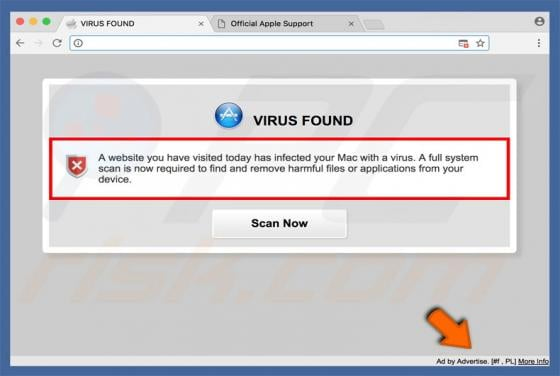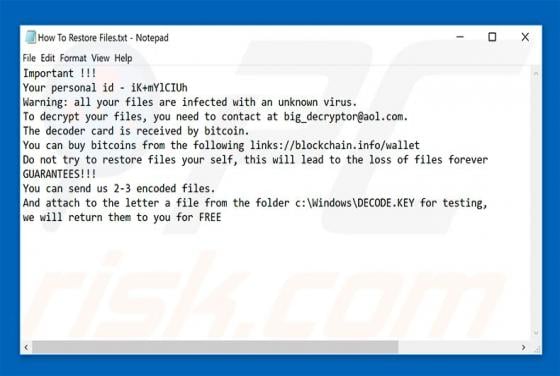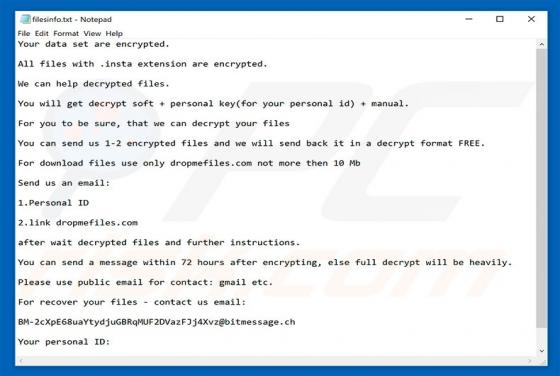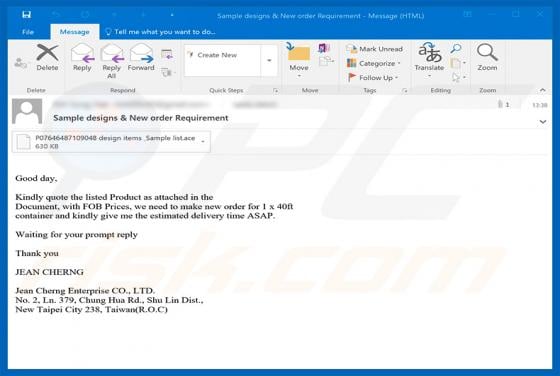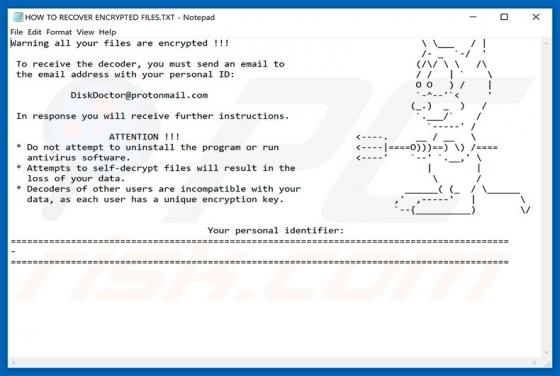
RedEye Ransomware
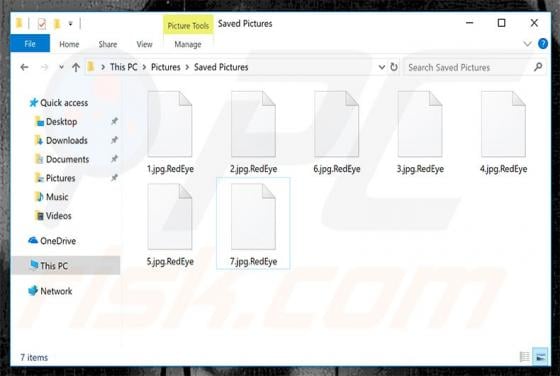
RedEye is a ransomware-type virus designed by the creator of ANNABELLE and Jigsaw viruses. Once infiltrated, RedEye supposedly encrypts data using the AES-256 encryption algorithm and appends filenames with the ".RedEye" extension (e.g., "sample.jpg" is renamed to "sample.jpg.RedEye"). As well as