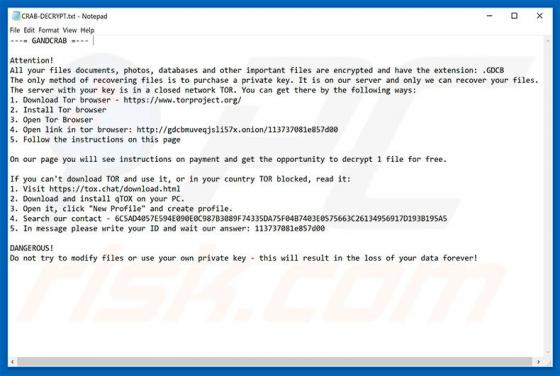
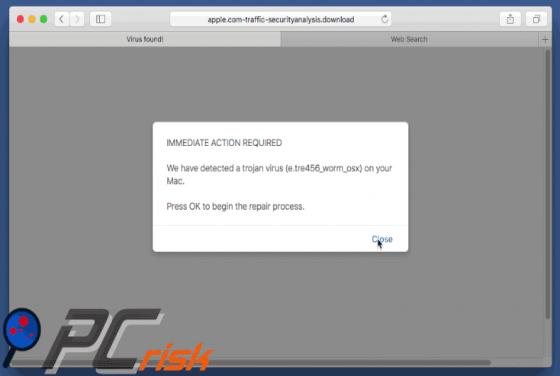
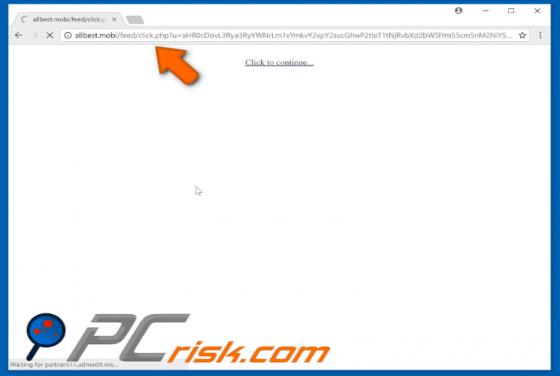
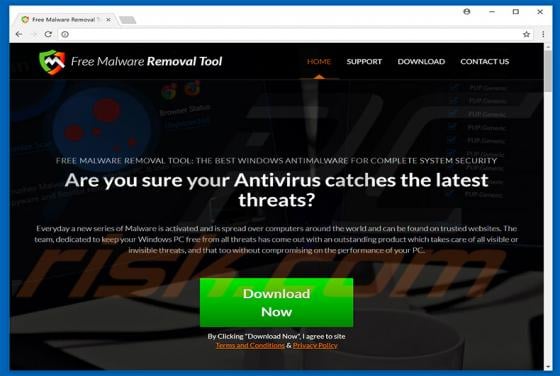
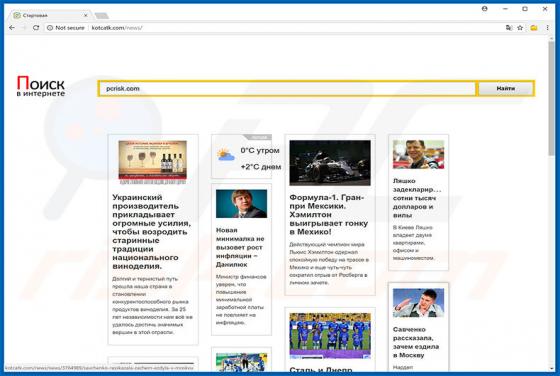
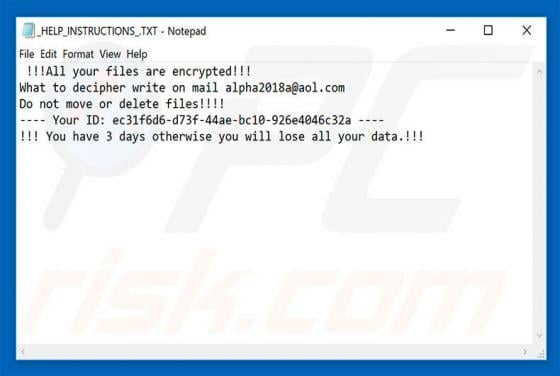
Newtab.pro Redirect
Developers present newtab.pro as a "top quality" web search engine that enhances the browsing experience by generating improved results and providing quick access to various popular websites. Initially, newtab.pro may seem legitimate and useful, however, this site is promoted using browser-hijack