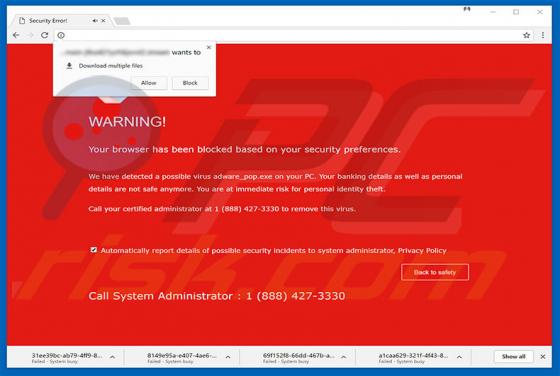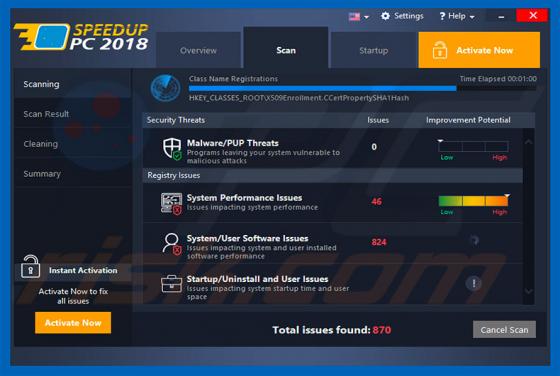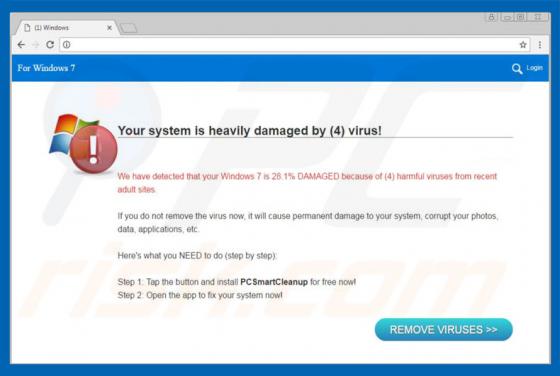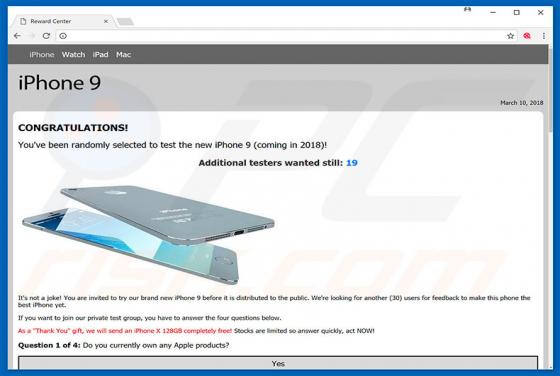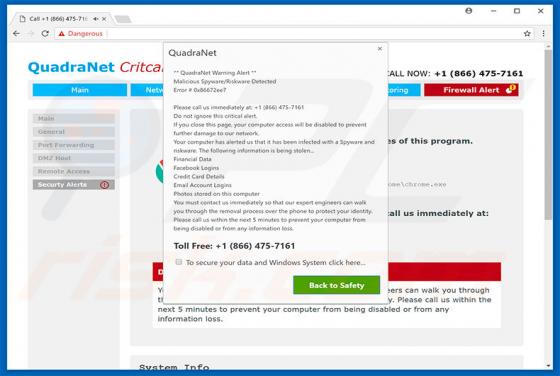
Comcast Cable Warning Alert Scam
"Comcast Cable Warning Alert" is another fake error similar to Do Not Ignore This Windows Alert, Code 055BCCAC9FEC, Microsoft Warning Alert, and many others. This error is displayed by malicious sites that users often visit inadvertently - they are redirected by intrusive advertisements (displayed