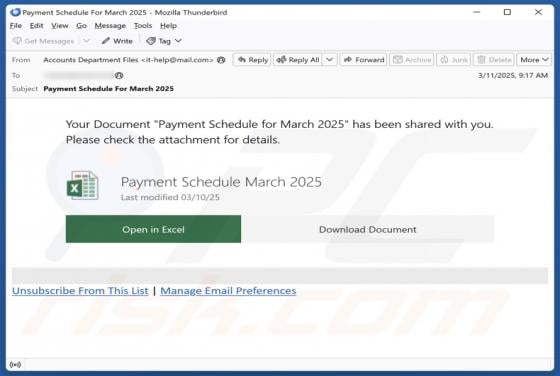
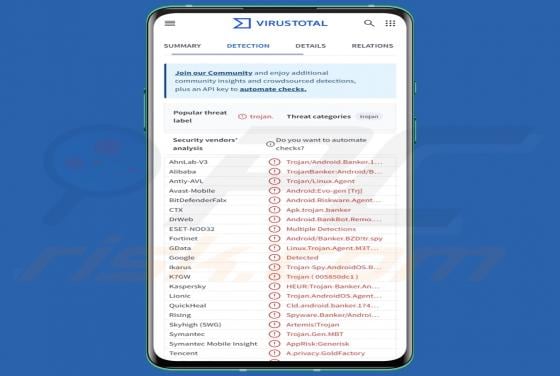
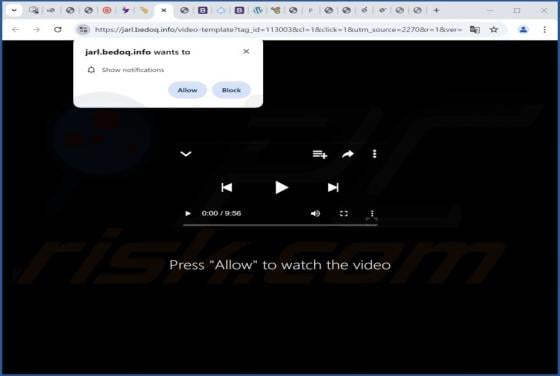
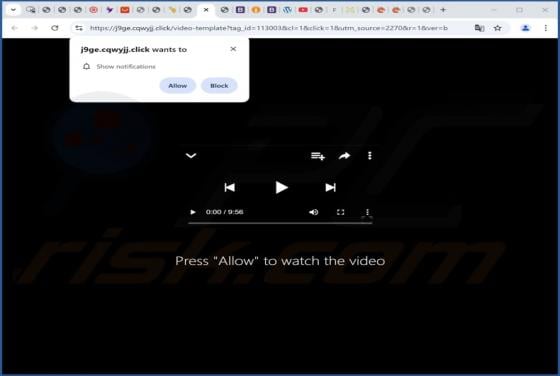
Moroccan Dragon Ransomware
Moroccan Dragon is the name of a ransomware-type program. It is designed to encrypt files and demand payment for the decryption. On our testing system, Moroccan Dragon encrypted files and appended their names with a ".vico" extension. To elaborate, an original filename like "1.jpg" became "1.jpg.