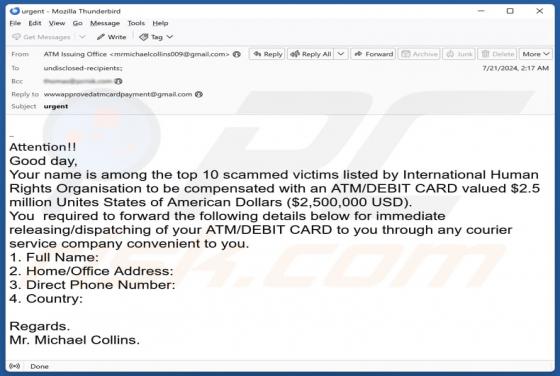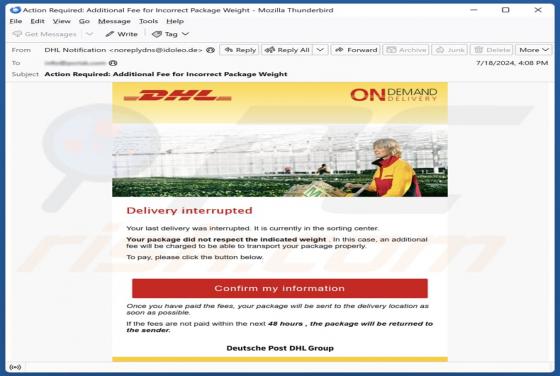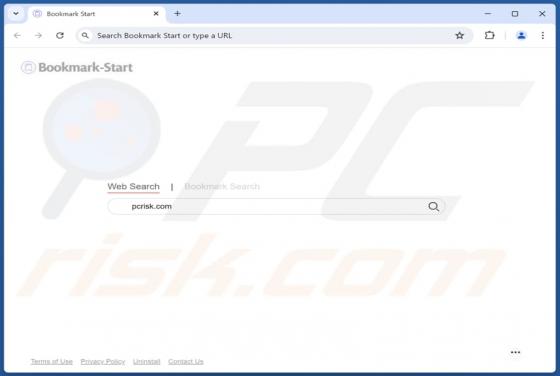
Bookmark Start Browser Hijacker
While inspecting the Bookmark Start extension, we learned that its functionality includes hijacking a web browser. Extensions of this type are known as browser hijackers. Users often unintentionally add such extensions to their browsers. If an extension like Bookmark Start hijacks a browser, users