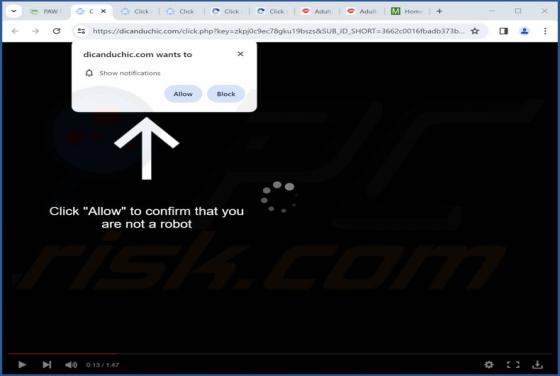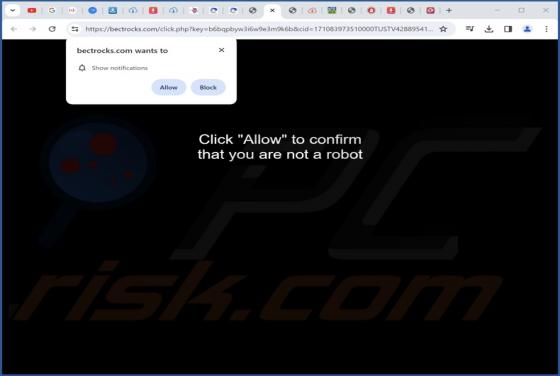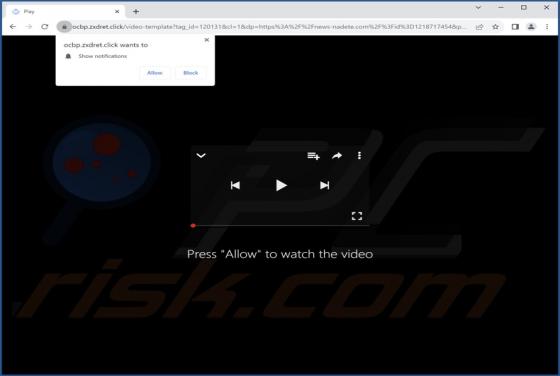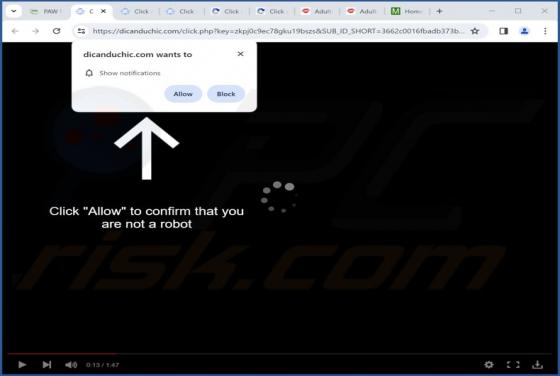
Dicanduchic.com Ads
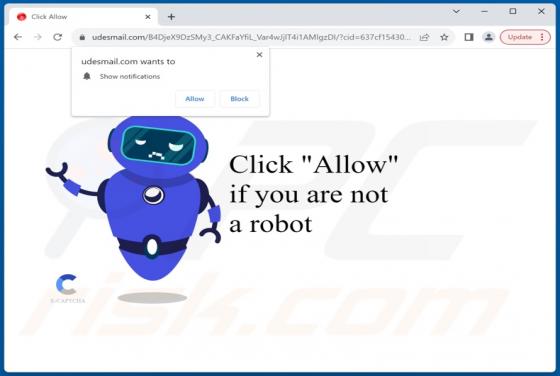
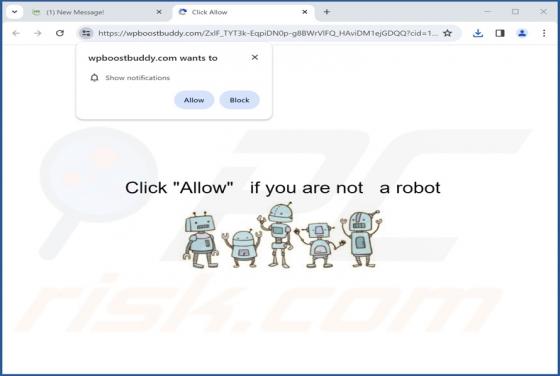
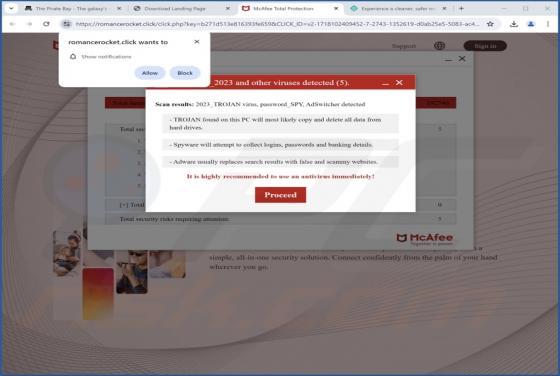
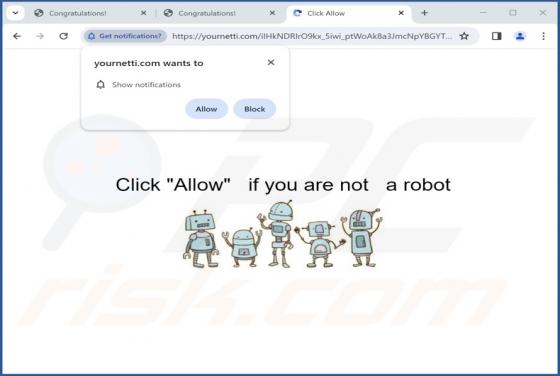
After reviewing dicanduchic[.]com, we have discovered that it employs a deceptive tactic to persuade visitors to grant notification permissions. Web pages like dicanduchic[.]com should not be allowed to display notifications. It is also worth mentioning that users typically do not visit such pages