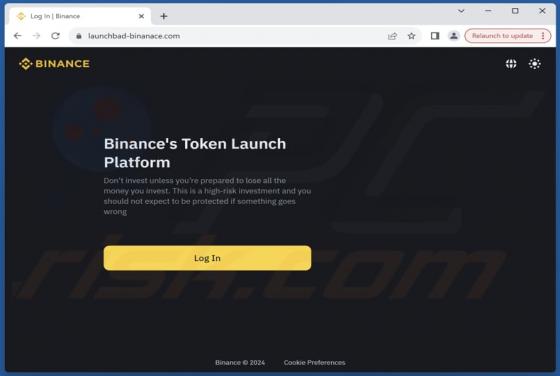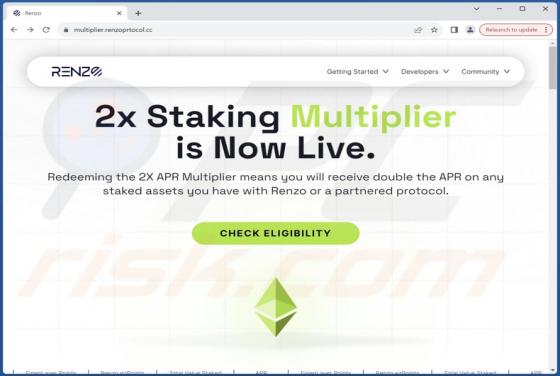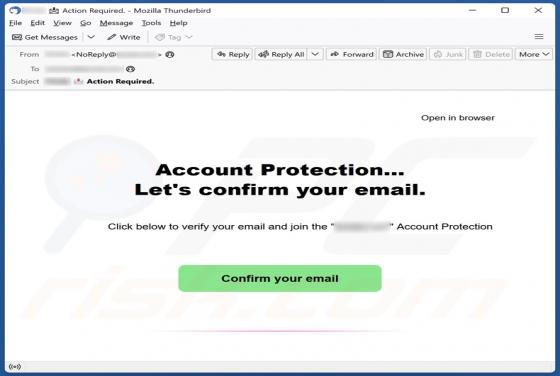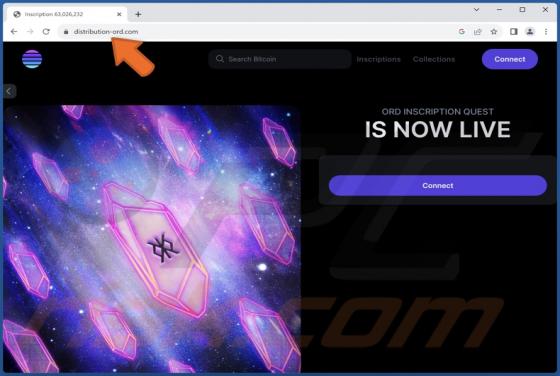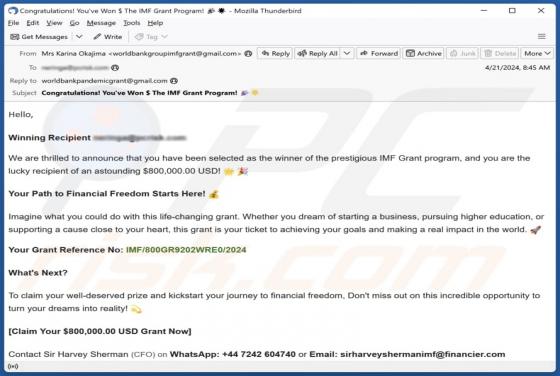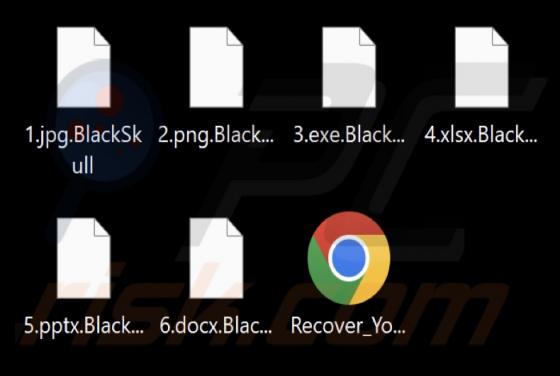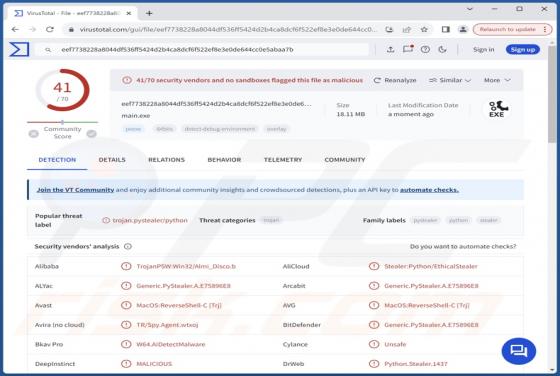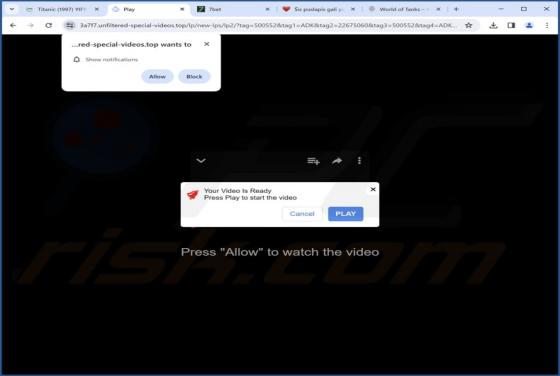
Unfiltered-special-videos.top Ads
After examining unfiltered-special-videos[.]top, we concluded that it is not reliable. The site employs clickbait tactics to entice visitors to permit it to send notifications. Additionally, unfiltered-special-videos[.]top might redirect users to other shady web pages. Unfiltered-special-v