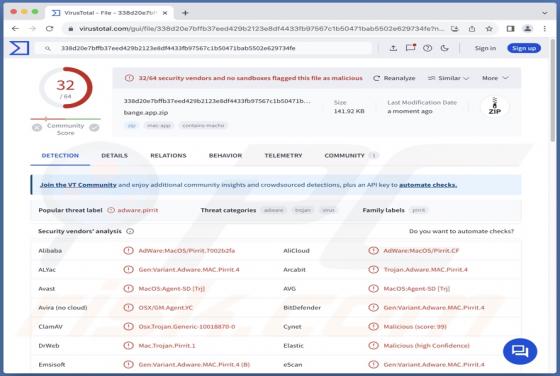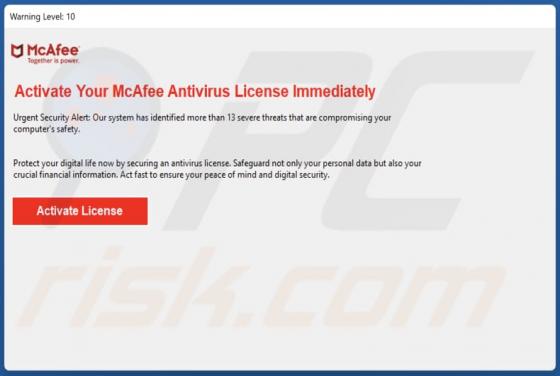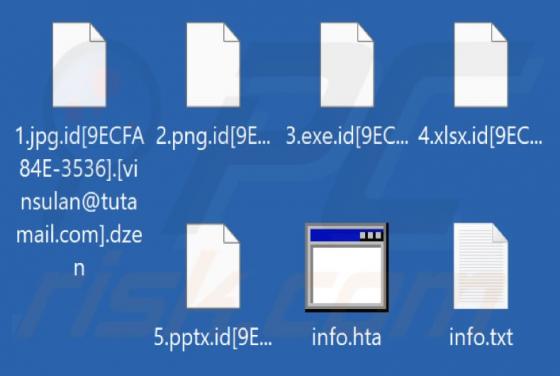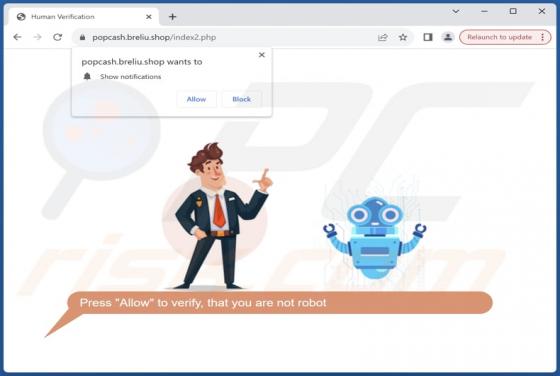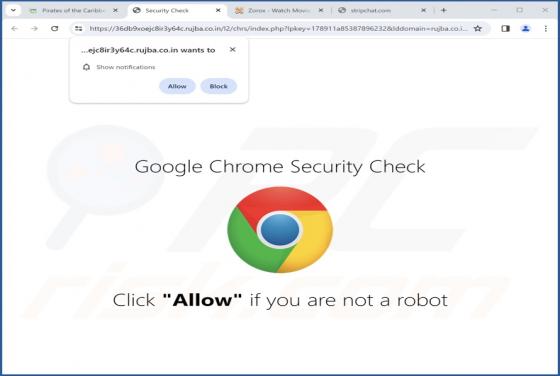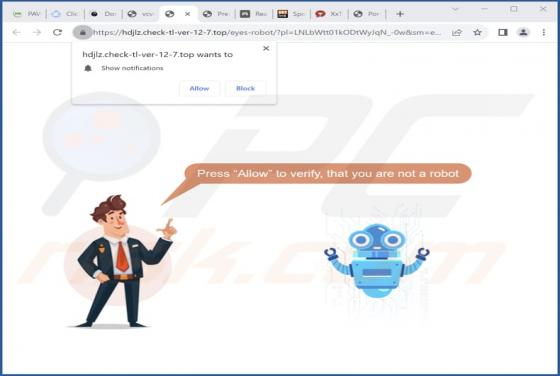
Check-tl-ver-12-7.top Ads
During our examination of the website, we discovered that check-tl-ver-12-7[.]top is one of many deceptive pages using clickbait tactics to obtain visitors' permission to send notifications. Additionally, check-tl-ver-12-7[.]top may redirect visitors to similar websites. Therefore, it is advisable