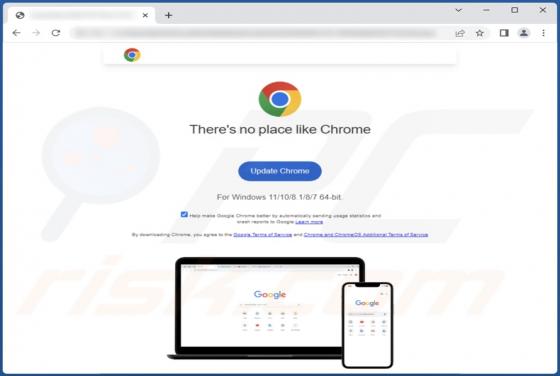
FakeSG Malware
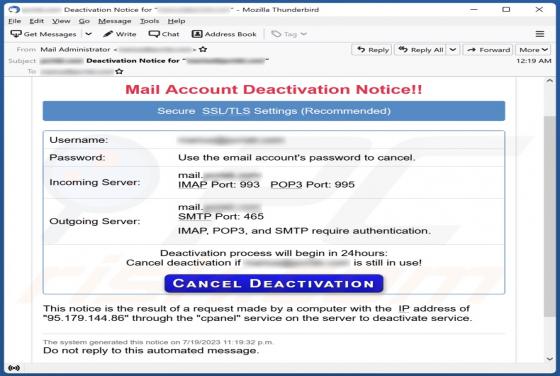
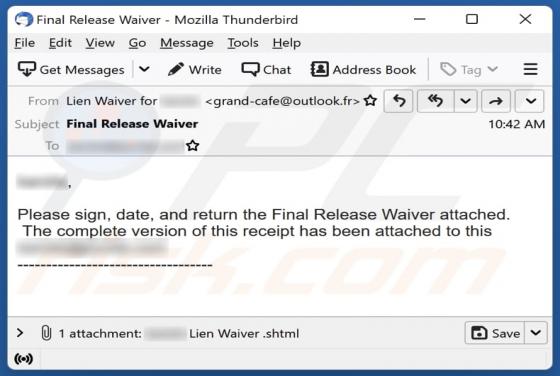
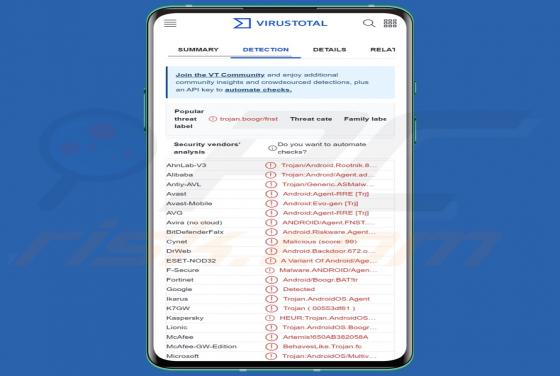
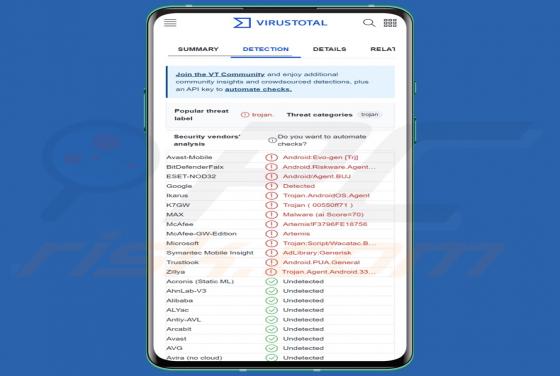
FakeSG is the name of a malware campaign. It involves compromised websites that imitate the potential victim's browser and urge them to update it. However, instead of installing a browser upgrade, the victim inadvertently allows malicious software to infiltrate their device. The observed FakeSG c