PixBankBot Malware (Android)
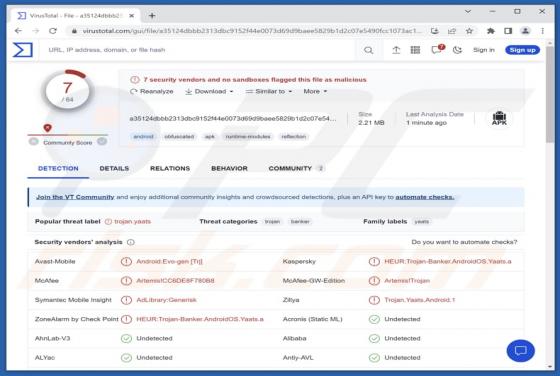
PixBankBot is an Android banking Trojan that exploits the Pix instant payment platform. This Trojan specifically targets Brazilian banks and employs an ATS (Automated Transfer System) framework for its operations. It should be removed from infected devices as soon as possible to avoid potential ha