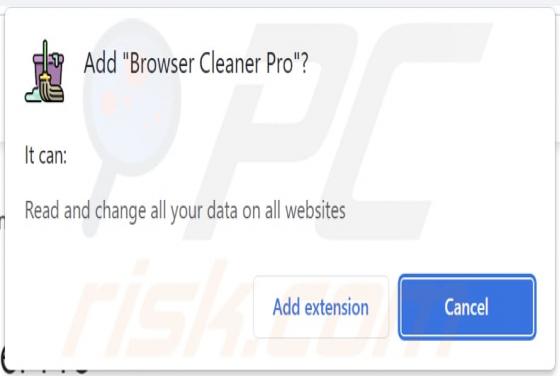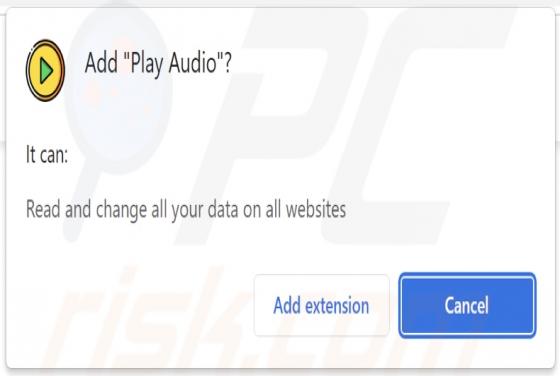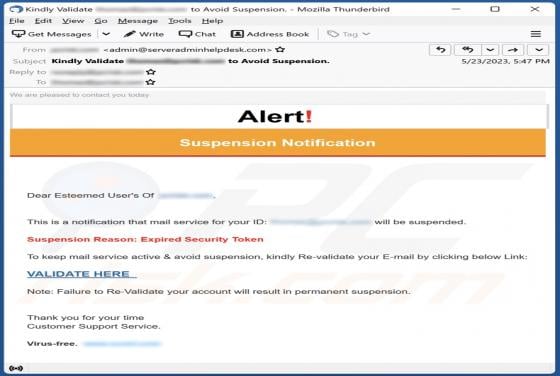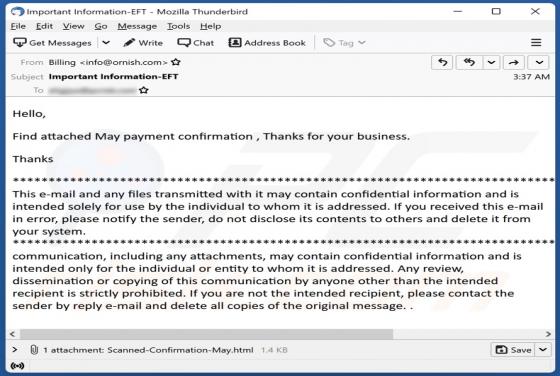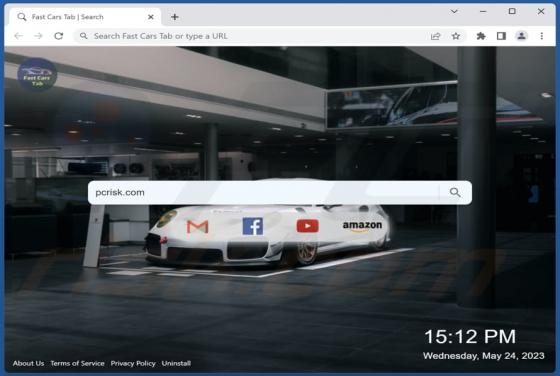
Fast Cars Tab Browser Hijacker
During our investigation of the Fast Cars Tab extension, we discovered that it seizes control of web browsers by making changes to their settings. The primary objective of this browser-hijacking extension is to endorse a deceptive search engine known as fastcarstab.com. Furthermore, there is a pos