Starvardsee.xyz Ads
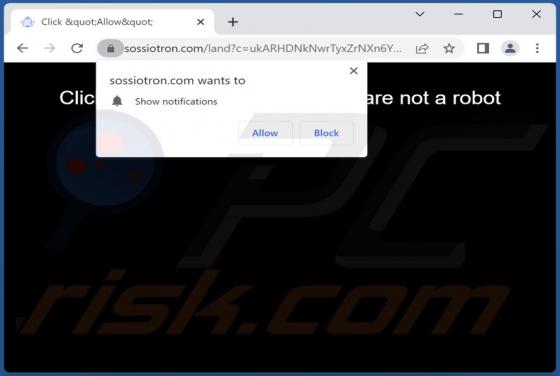
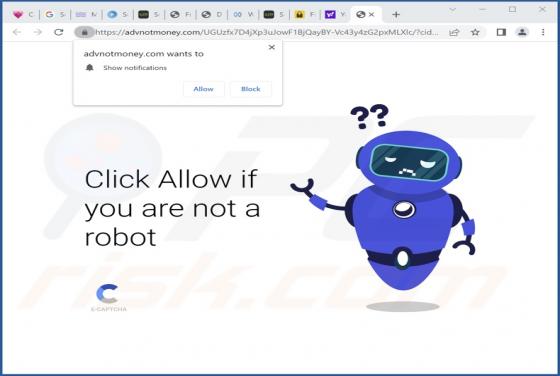
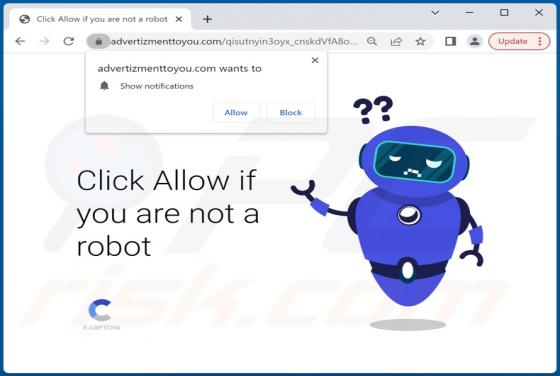
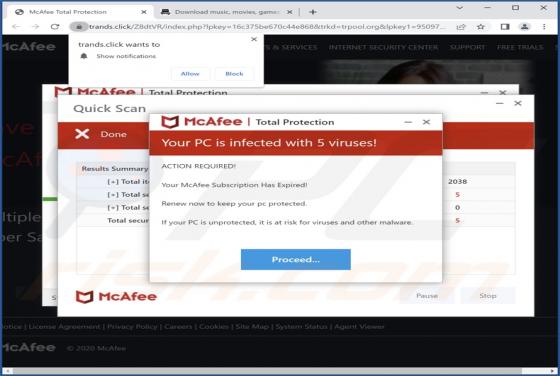
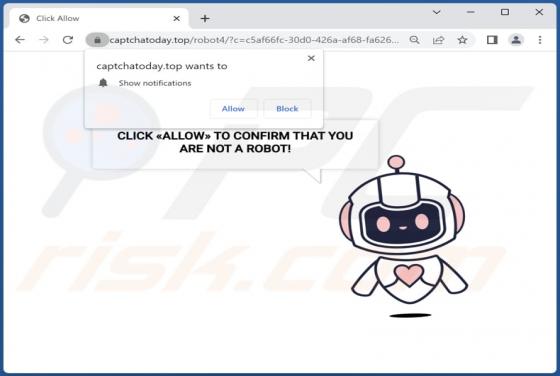
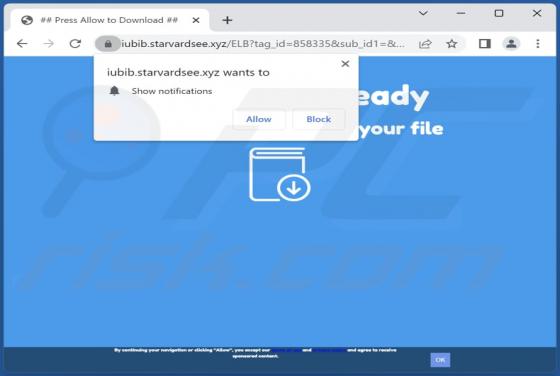
We discovered starvardsee[.]xyz while examining websites that use rogue advertising networks. After analyzing starvardsee[.]xyz, we determined that it displays misleading content to gain permission to show questionable notifications and redirects users to other untrustworthy pages. Starvar