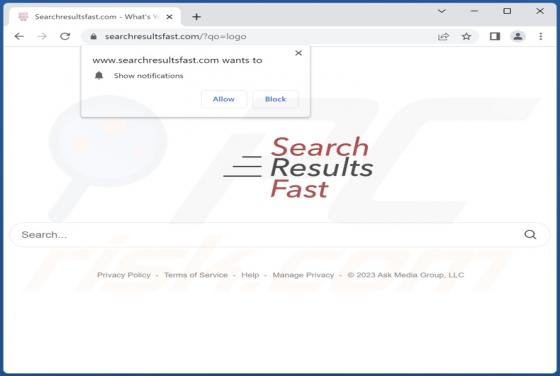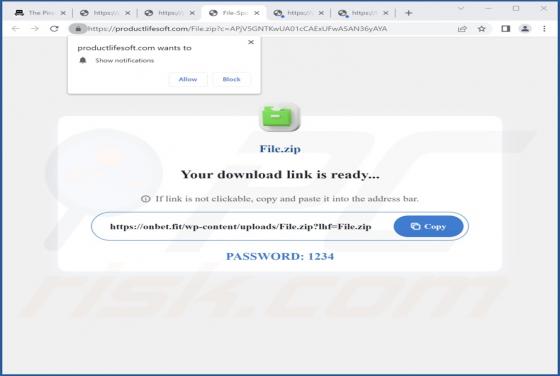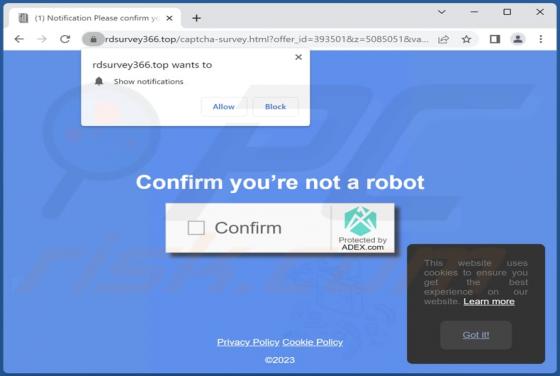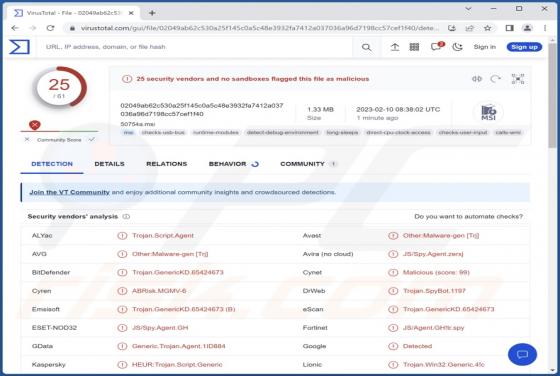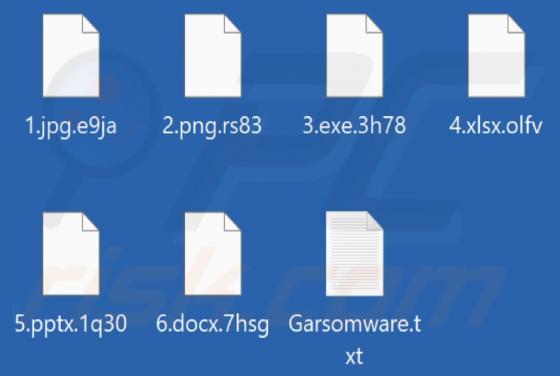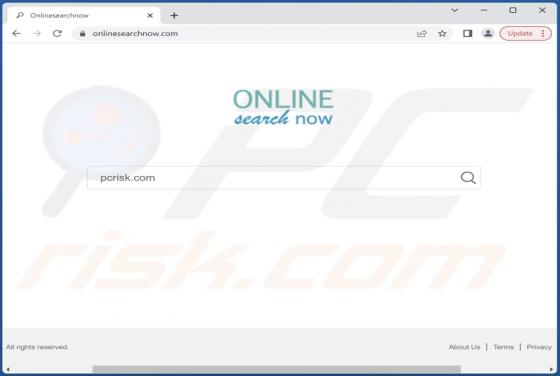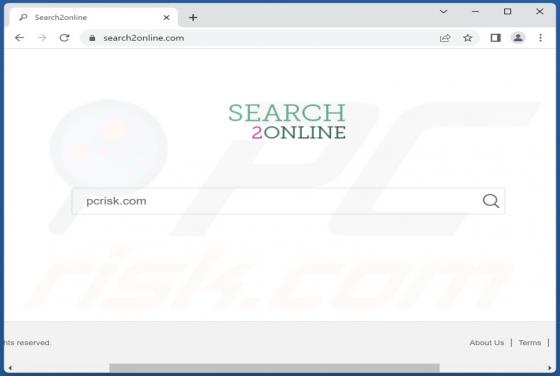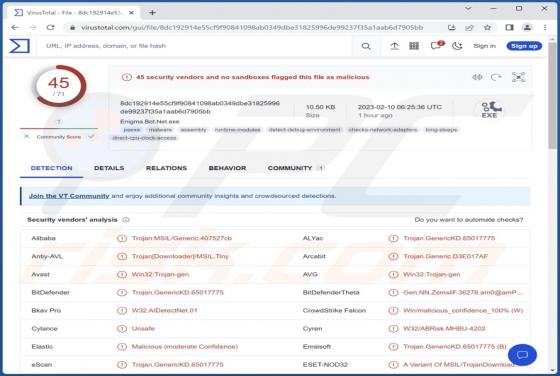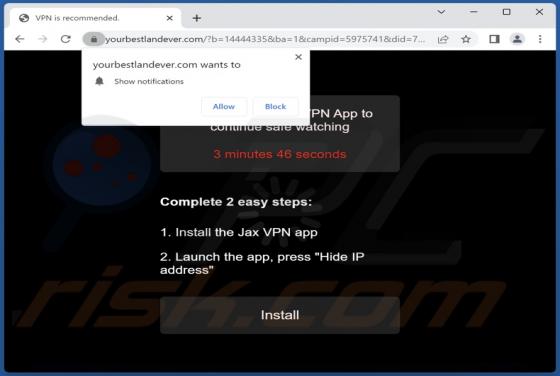
Yourbestlandever.com Ads
Yourbestlandever[.]com is a rogue webpage that we discovered while inspecting untrustworthy websites. This page endorses deceptive content (online scams) and browser notification spam. Furthermore, it can redirect users to other (likely unreliable/dangerous) sites. Most visitors to yourbestlandev