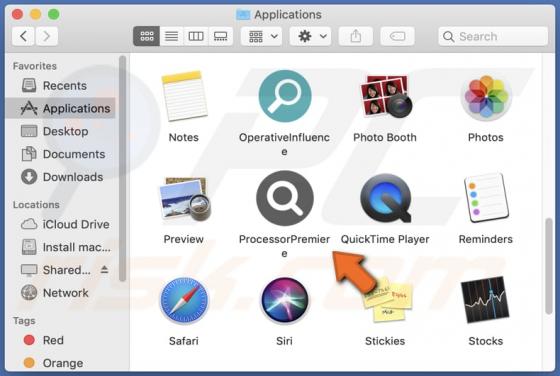
ProcessorPremiere Adware (Mac)
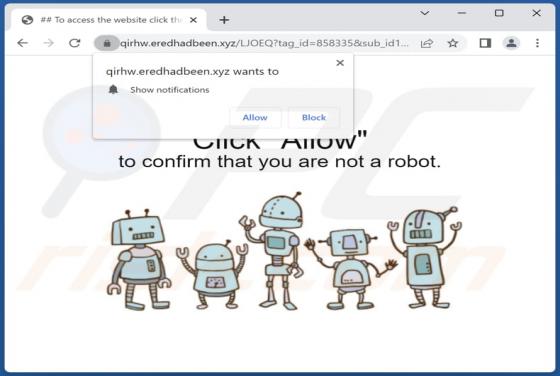
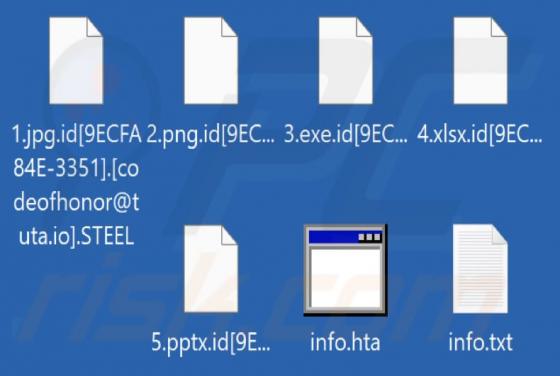
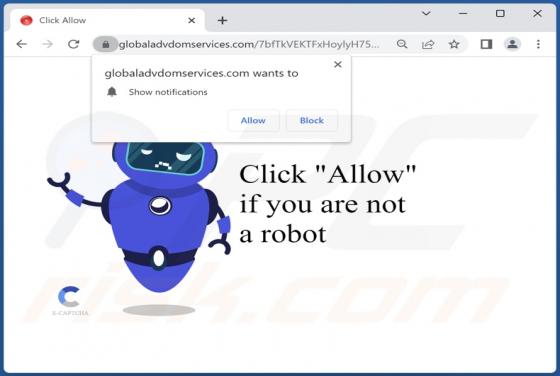
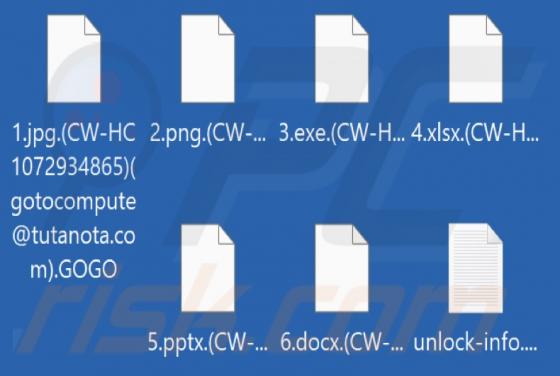
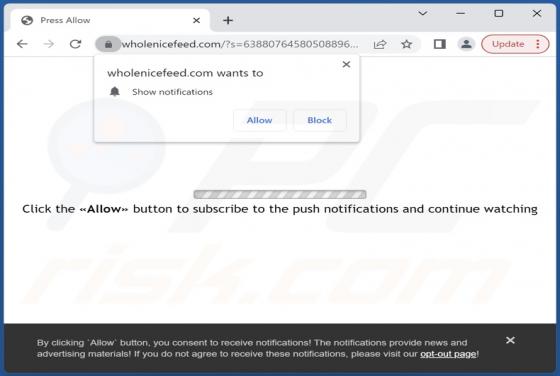
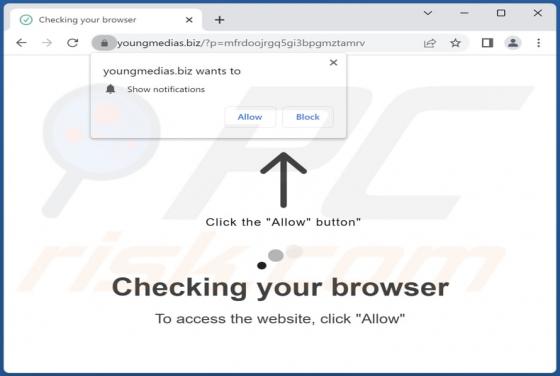
While testing the ProcessorPremiere application, our team noticed that it shows annoying advertisements. Thus, we classified ProcessorPremiere as adware. We also found that ProcessorPremiere can read sensitive information. It is worth mentioning that users rarely download and install adware on p