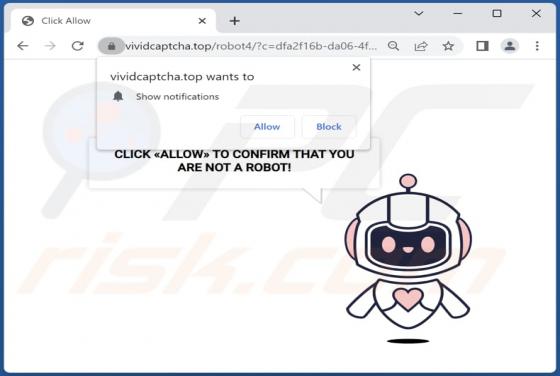
Vividcaptcha.top Ads
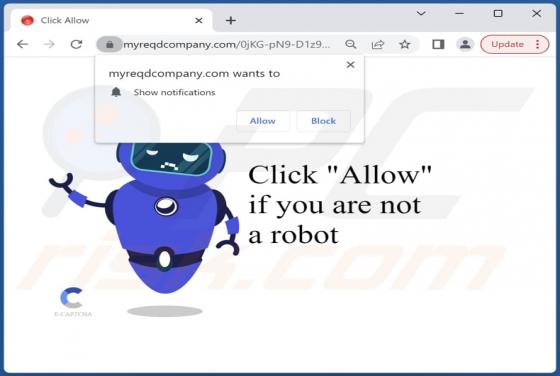
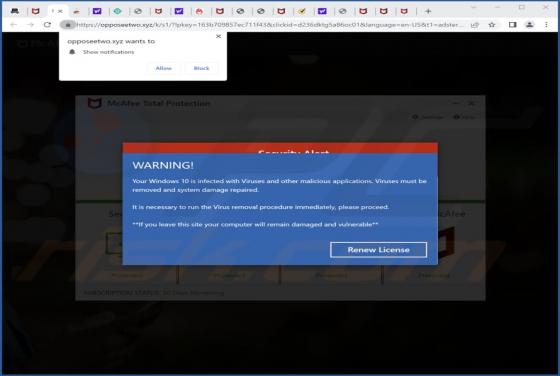
Our team has examined vividcaptcha[.]top and found that it displays a deceptive message to trick visitors into allowing it to show notifications. Also, vividcaptcha[.]top redirects visitors to a scam website. We discovered vividcaptcha[.]top while visiting pages that use rogue advertising networks