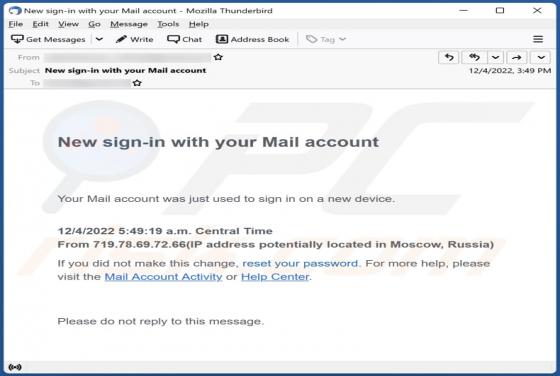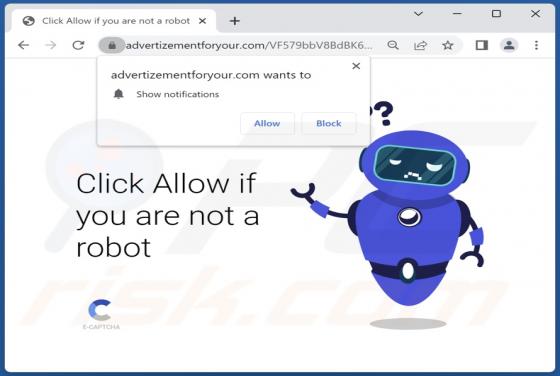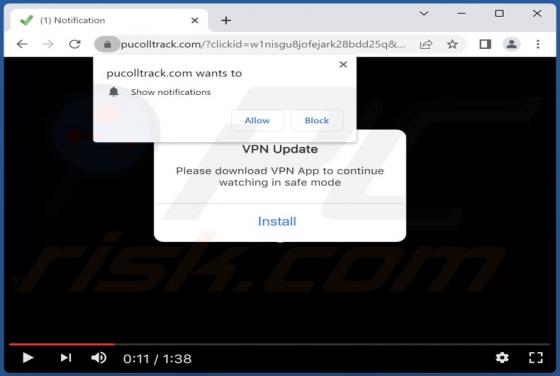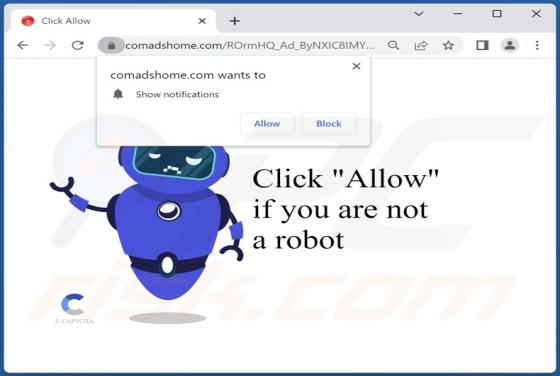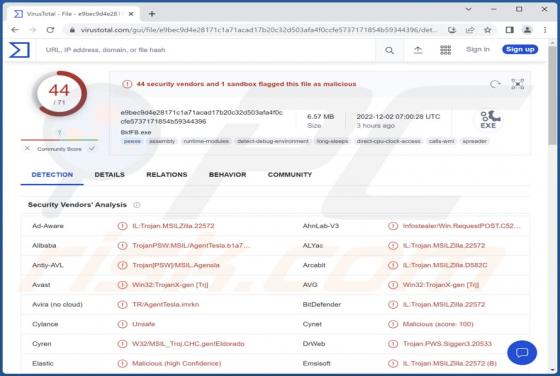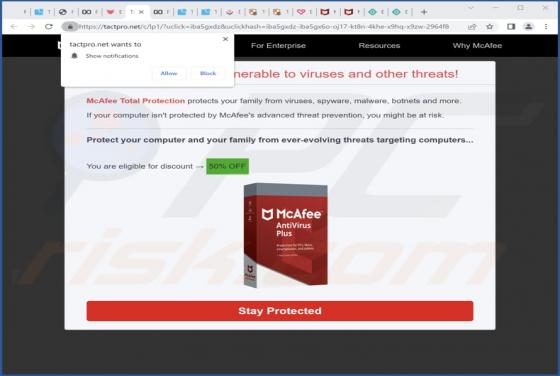
Tactpro.net Ads
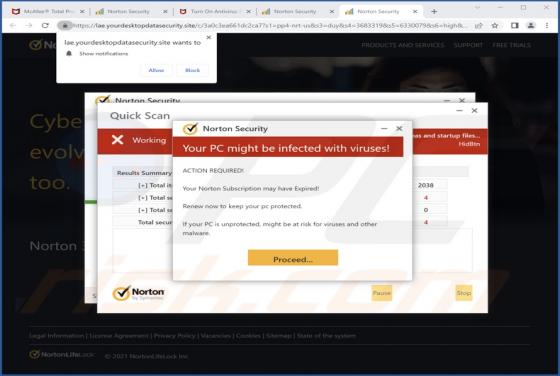
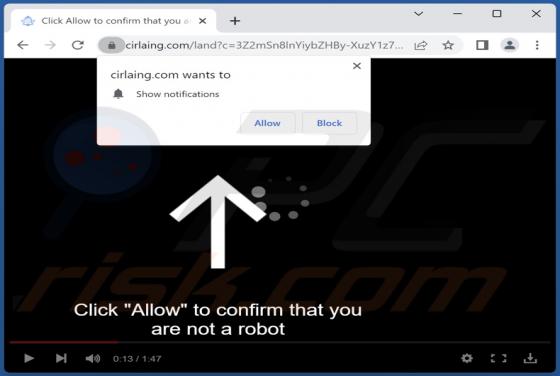
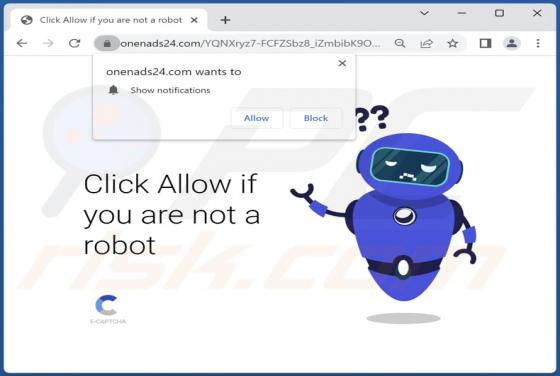
While examining tactpro[.]net, we found that it offers visitors to protect their computers (promotes antivirus software) and asks for permission to show notifications. Our team discovered tactpro[.]net while inspecting websites that use rogue advertising networks (illegal movie streaming pages, to