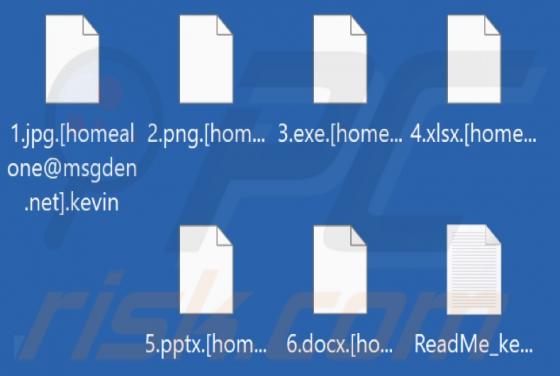
Kevin Ransomware
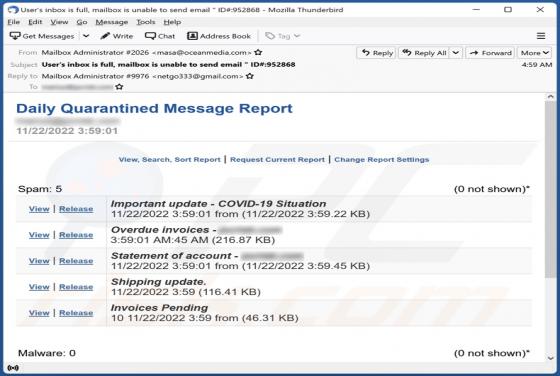
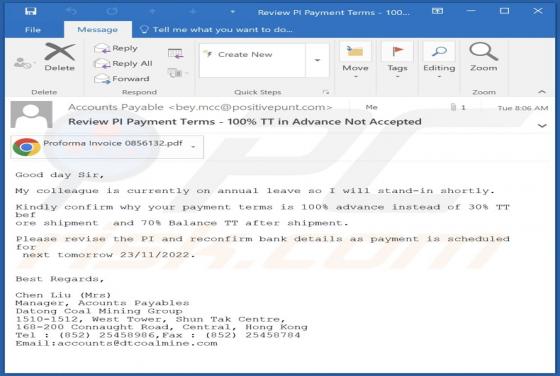
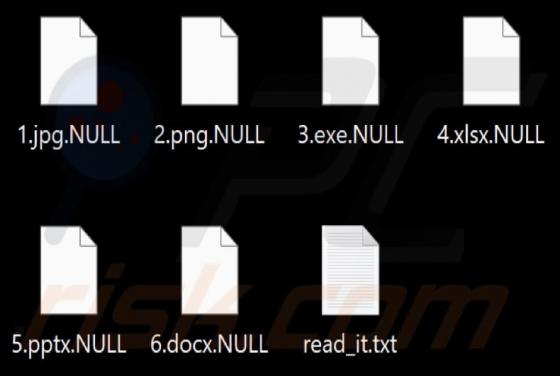
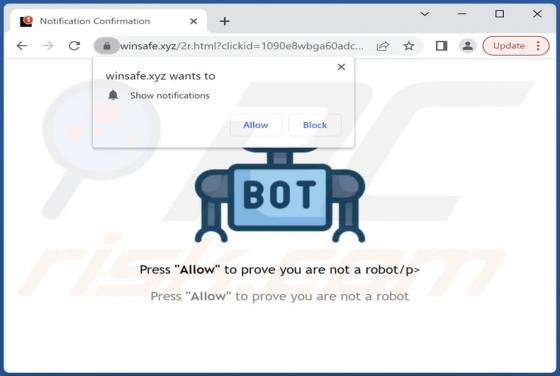
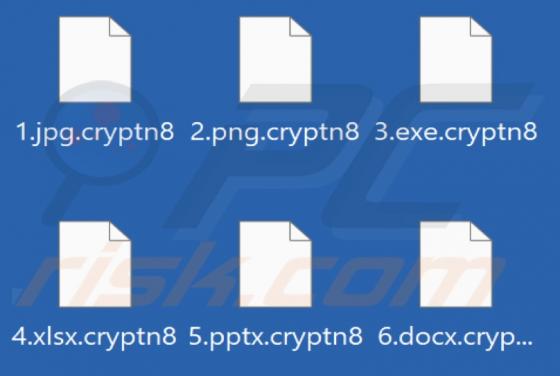
While inspecting new malware submissions to VirusTotal, our research team discovered the Kevin ransomware. Malicious software within this classification operates by encrypting data in order to make ransom demands for the decryption keys/tools. When we executed a sample of Kevin ransomware on our