Web Video Player Adware
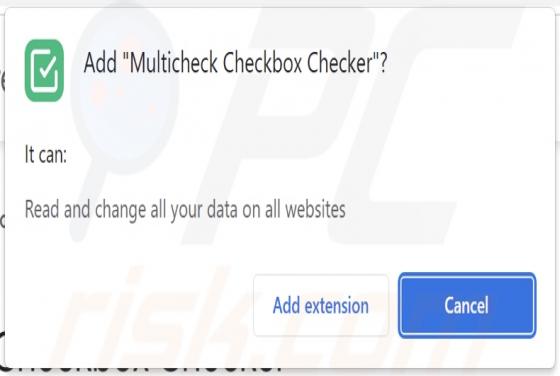
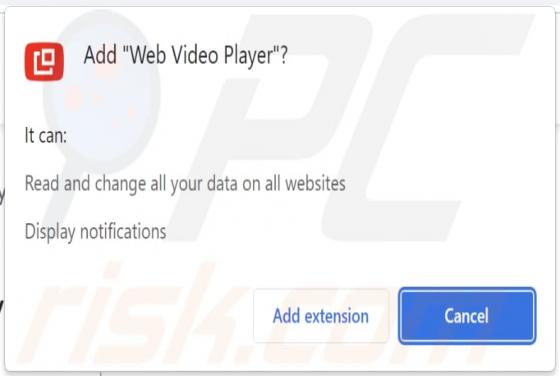
While testing the Web Video Player browser extension, we found that it shows intrusive advertisements, can read and change data on all websites, and display notifications. We discovered Web Video Player on a deceptive website. Since this app shows ads, we classified it as adware. Web Video