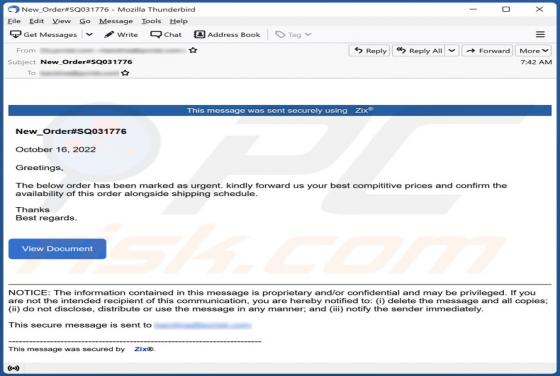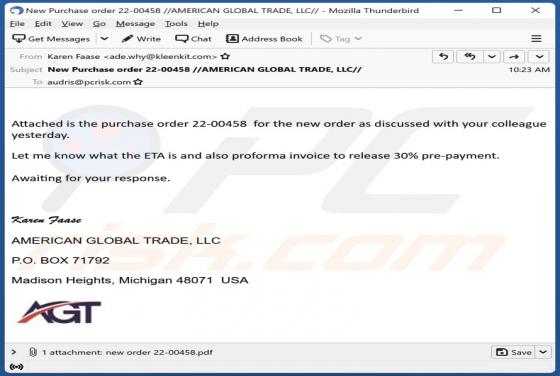
AMERICAN GLOBAL TRADE Email Scam
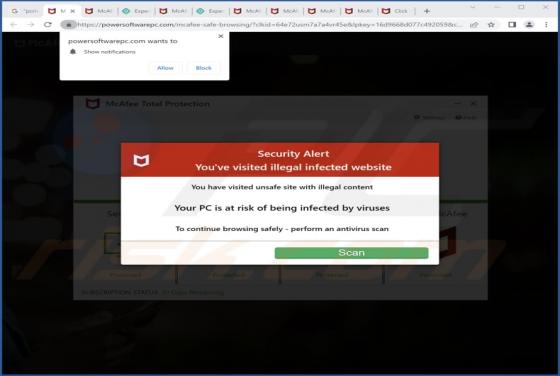
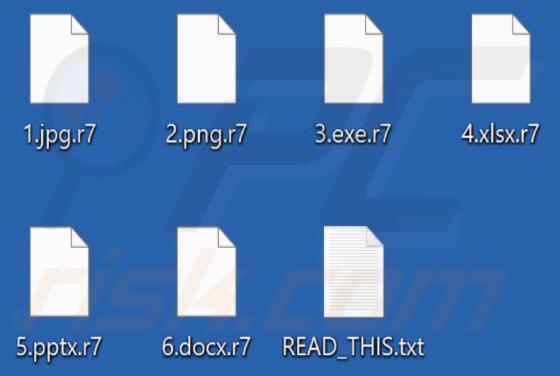
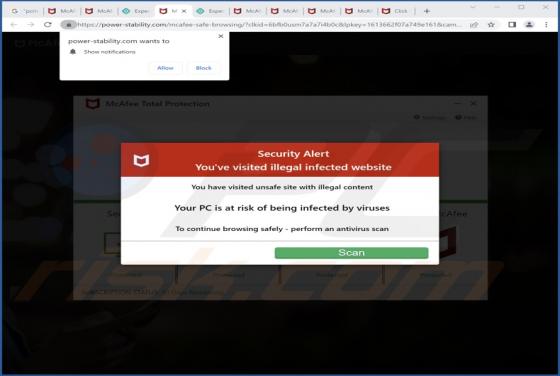
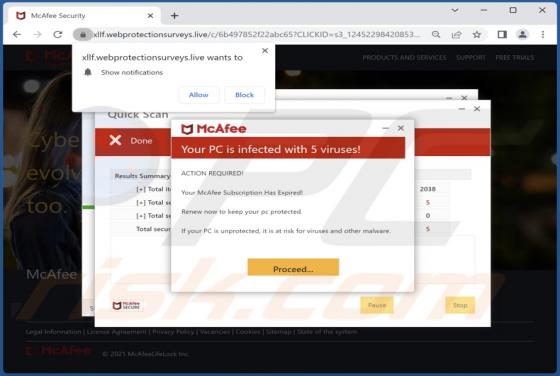
While investigating this email, we found that it is a scam email written by scammers who aim to lure unsuspecting recipients into opening the attached file. Scammers disguised this email as a letter from a company called AMERICAN GLOBAL TRADE regarding a new purchase order. It is strongly recommen