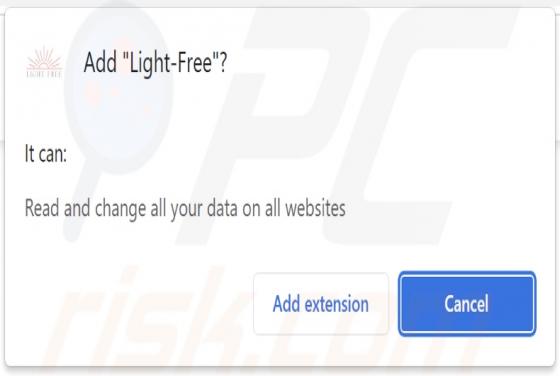
No-Light Adware
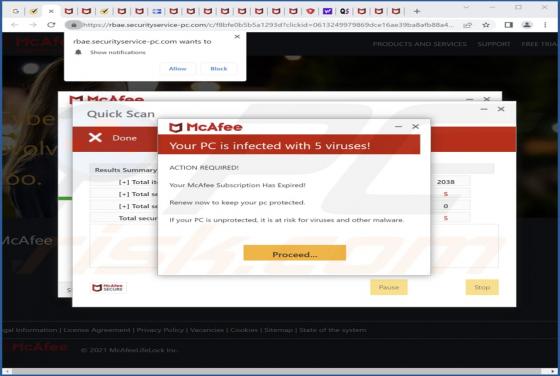
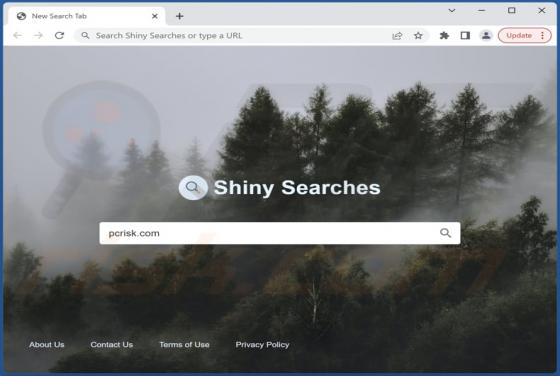
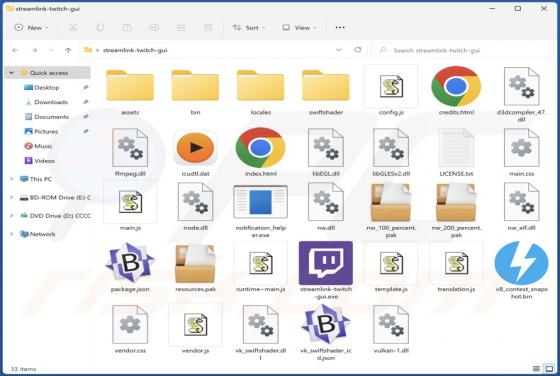
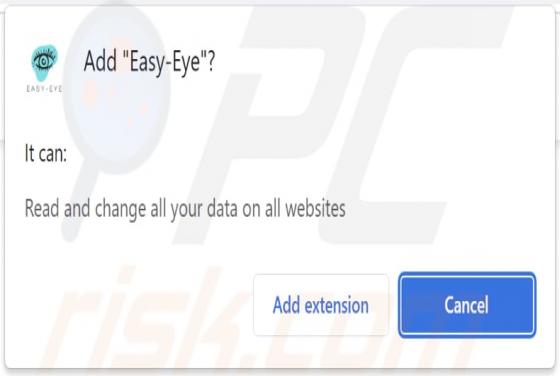
While inspecting deceptive software-promoting websites, we discovered the No-Light browser extension. This piece of software is presented as a tool capable of creating a dark mode for simple design websites. However, our analysis revealed that No-Light operates as advertising-supported software (a