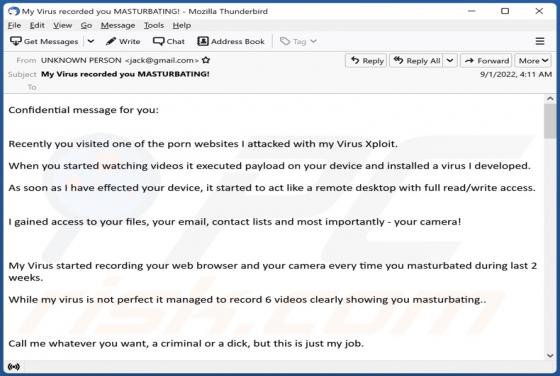
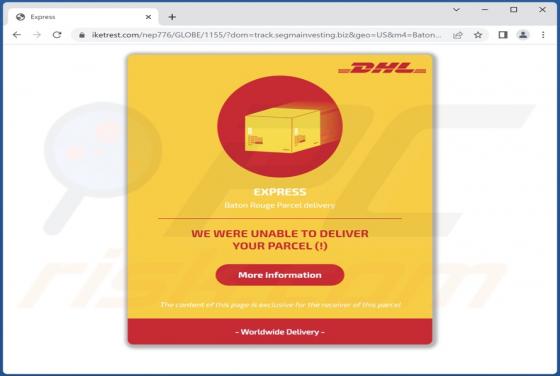
FunctionBlast Adware (Mac)
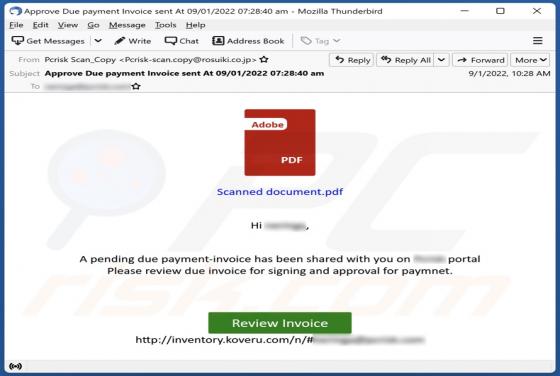
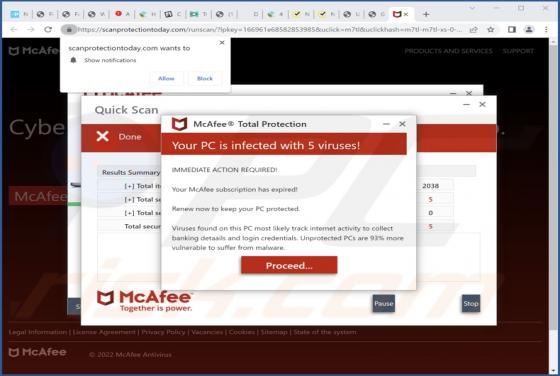
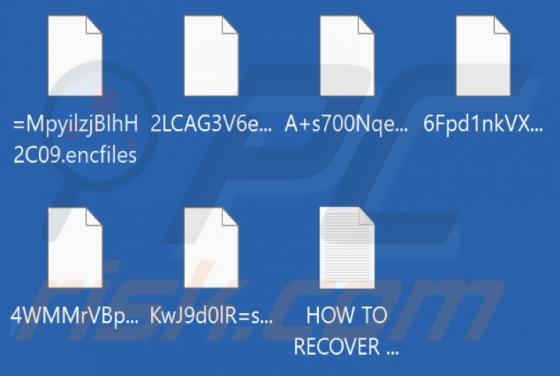
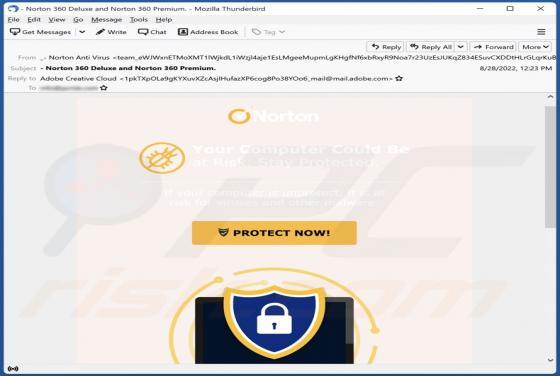
We found the FunctionBlast application while inspecting new submissions to VirusTotal. Our analysis of this piece of software revealed that it is adware belonging to the AdLoad malware family. Adware stands for advertising-supported software. It is designed to run intrusive advertisement