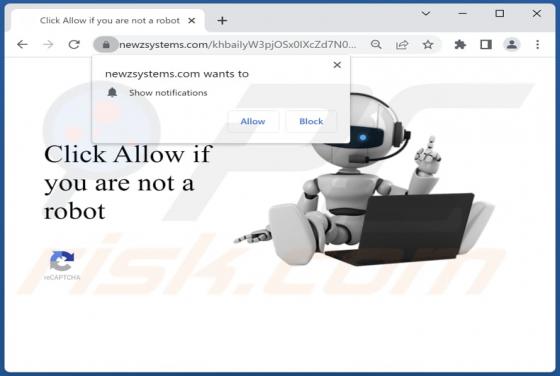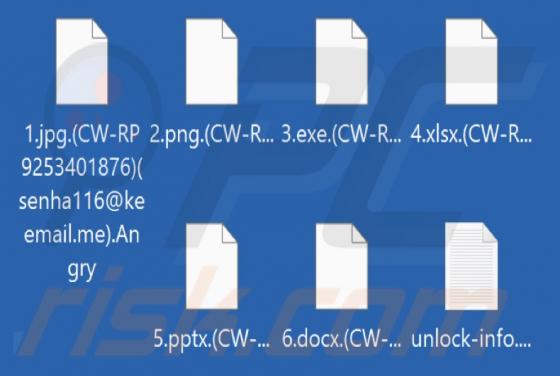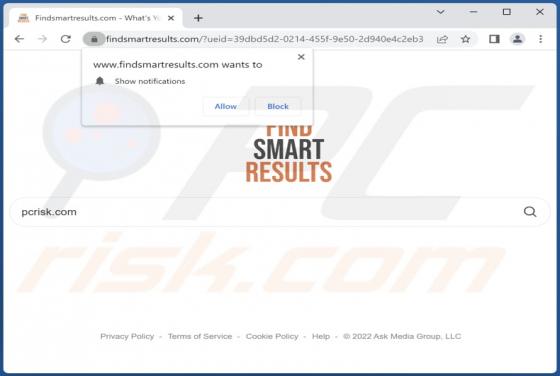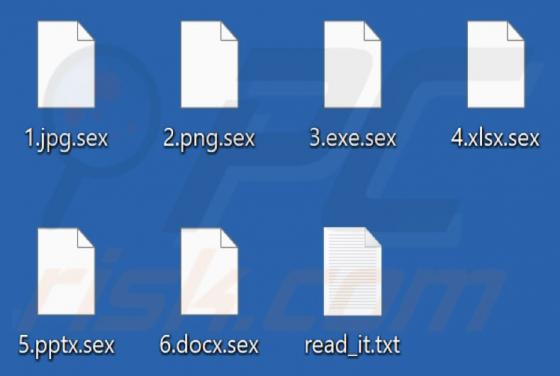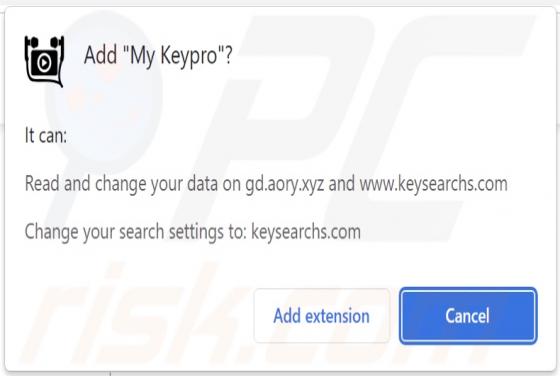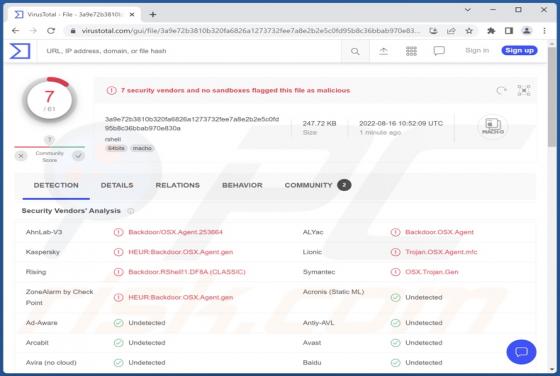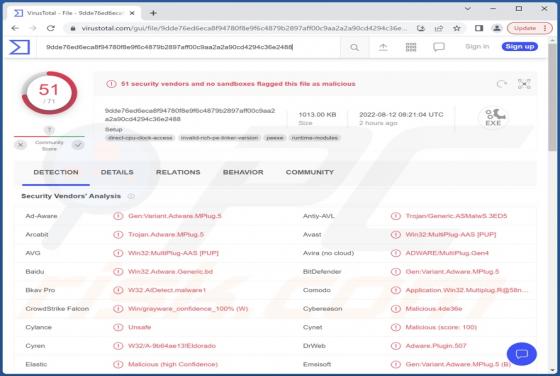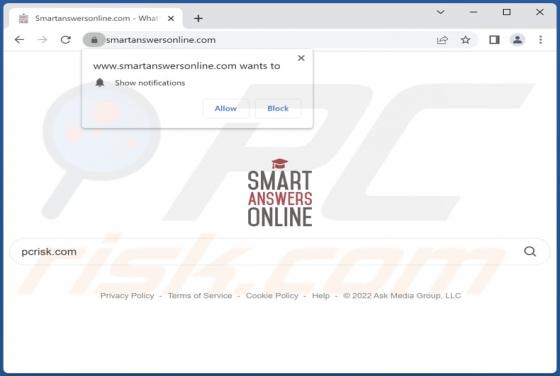
Lumma Stealer
Lumma is a piece of malicious software categorized as a stealer. Malware within this category is designed to steal sensitive data. These programs are capable of exfiltrating data from infected systems and the applications installed onto them. The threats posed by stealers can be extensive and depe