News Archive November 2013
Monthly Cyber Security News Archive: November 2013 Summary
Table of contents:
- Hacked Limo Service Leaks Celebrity Information
- Personal Files Held for Ransom on YOUR Computer
- Is Your Smart TV Too Smart?
- It’s Not Just Your Online Bank Account You Need to Worry About
Hacked Limo Service Leaks Celebrity Information
13.11.13
Last month, this website reported the massive data breach experienced by Adobe. Personal information from millions of Adobe users was compromised following an attack that was exploiting a vulnerability in Adobe’s own product – Cold Fusion. Found on the same server as the compromised Adobe data was information from a company known as CorporateCarOnline. The same group of hackers responsible for these attacks was also implicated in the theft of information from PR Newswire. The Adobe incident has had far-reaching consequences. The popular social media site Facebook was given a copy of the stolen data and compared the username/password combinations to existing Facebook users. Any users that were using the same combinations for both Facebook and Adobe products were forced to change their Facebook login information and answer additional security questions to prove their identity before logging into the site.
CorporateCarOnline is a Kirkwood, Missouri-based company that claims to be the premier provider of software management solutions for limousine services around the country. Although the company has acknowledged the data breach, a spokesperson was unwilling to comment on the issue. The problem is that the data stored on the remote server contained plain text format files detailing the specifics of customers using limousine services relying on CorporateCarOnline software.
Stolen data included the specific comments left for drivers regarding celebrity clients and even more alarming, the unencrypted credit card information of many of these same celebrities.
Many of the credit card numbers recovered from this breach were American Express cards that had no limit.

These cards, commonly referred to as Black Cards, have no credit limit and are reserved for super-rich celebrities. It is a status symbol simply to own one of these cards so it goes without saying that these cards command a ridiculous value in the hacking and credit card fraud underworld. Although CorporateCarOnline is not a household name, the company provides a service used by the elite in America. Hackers cleverly discovered how much valuable information was stored by a company that very few people have even heard of. Due to the same Cold Fusion vulnerability that affected Adobe, hackers were able to steal this information and potentially profit from it prior to the scam being uncovered by security experts.
This scam once again demonstrates that even PC users that are good at protecting their computers from online threats may still fall victim to hacking attacks through no fault of their own.
In this case, celebrities who value their privacy more than anything were exposed. Not only was credit card data compromised, but in many cases, home addresses of these celebrities were also stolen by this group of hackers that has successfully eluded authorities despite these three significant scams being uncovered. The only defense from this type of scam is to regularly check your bank and credit card statements for any discrepancies that could indicate your information has been compromised.
Personal Files Held for Ransom on YOUR Computer
17.11.13
Windows users have a new threat to worry about. This malware infection is capable of holding your personal files (including music, pictures and documents) until a ransom is paid to the hackers who created the scam. Known as CryptoLocker, this new version of malware is a simply a new version of an old scam; however, it has been highly effective so far. Once downloaded, the program immediately encrypts all personal files on the compromised machine. The encryption algorithm is rock-solid and nearly impossible to crack. A countdown timer informs victims that they have 72 hours to pay a ransom ranging from $100 to $300. This ransom is only payable in Bitcoins or MoneyPak. This is a unique twist on the old ransom scam for a couple reasons.
First, the scam actually encrypts the files on the infected hard drive. Older ransom malware scams continually alerted the victim about paying to remove the malware but files were still accessible. Literally, if a user does not pay – the files cannot be recovered. Also, this malware variant actually unlocks the files once the ransom has been paid. In older versions of this scam, a user could pay only to find that there credit card information had been stolen AND they still had a malware infection.
It appears that these hackers have a conscience as they quickly decrypt affected files following payment.
Also, the hackers require payment via methods that are not susceptible to identity theft scams making it a safer (although certainly undesirable) option for victims. Once infected, a computer may show no outward signs of infection for hours. This is because the complex encryption algorithm can take a long time to completely encrypt the victim’s hard drive.
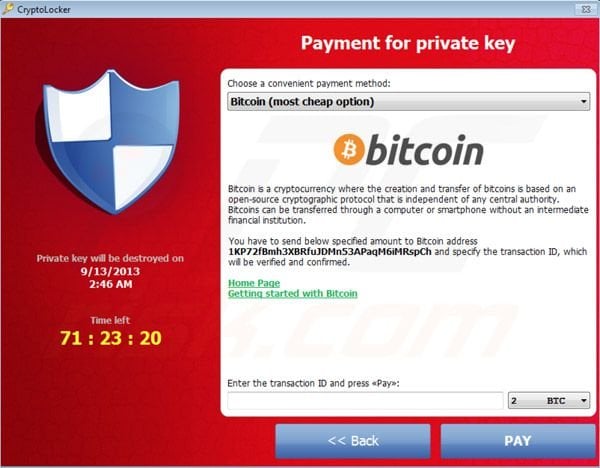
Obviously, the more files on the computer, the longer it takes to encrypt. However, once the encryption process is complete, victims are warned that if payment is not made within 72 hours, all data will be lost.
This scam has been extremely successful and the hackers behind this attack have even extended the deadline so victims have more time to pay.
Unfortunately, many victims do not even know what a Bitcoin is or how to procure them. Once the hackers realized they were leaving money on the table they extended the deadline to “accommodate” their victims. Once infection has occurred, removing the CryptoLocker program is relatively easy. The problem is that even with the malware removed, the affected files remain encrypted with no way to access them.
Unfortunately, the only way victims get access to their files again is by paying the ransom.
There are some free tools available that prevent the CryptoLocker infection from attacking files. In fact, there is an administrative toolkit available designed for system administrators that sets group policies that block CryptoLocker. There is also a personal version freely available that protects your PC from this devastating attack.
Updated antivirus software does not help prevent against this attack because the malware is not detected until your personal files are already encrypted.
The only protection from CryptoLocker is to only download files you are completely sure are safe.
Is Your Smart TV Too Smart?
23.11.13
This website has reported on the possibility of Smart TV web cameras potentially being hacked in the future. Although the web camera preinstalled on many new TVs is not at fault in this case, your smart TV could be invading your privacy right now. It appears that many of the new smart TVs being offered by LG have tracking software built-in that track and report the usage of smart TVs and collect files names associated with the USB drive of the TV. This alarming behavior was first detected by a UK-based developer known as DoctorBeet. Although LG has publicly denied any such privacy violation, it’s clear that this information is being collected as part of LG’s Smart Ad campaign. Like many other smart TV manufacturers, this technology is designed to display advertisements tailored specifically to the interests of the household where the TV is installed.
Namely, Samsung has a very similar program with one major difference – users can opt-out of the Samsung campaign. Unfortunately, customers currently using one of LG’s smart TV products have no way to opt-out of this blatant privacy violation.
DoctorBeet noticed that every time the channel was changed on these TVs, a unique TV identifier along with the channel were transmitted to an outside URL.
He also noted that all information associated with attached devices (specifically USB flash drives) were collected and sent to the same URL using the same unique TV identifier. Although this may seem disturbing enough, it gets worse. The information is being transmitted to LG completely unencrypted. This means that a potential identity thief could intercept this information and use it to target specific scam campaigns at these victims based on the information obtained from this covert LG program.
At the time of this writing, the URL where the information is being sent is not active; however, LG could activate this URL at any time and begin collecting data without the explicit consent of its customers.
The real problem is that there is no way for users to stop this collection process other than to purchase a different TV. There is an opt-out option within the TV settings menu; however, DoctorBeet reports that even after opting-out, his information was still being sent to the LG URL.
![]()
Since many of these smart TVs also have web cameras installed, is it possible that this is yet another feature that LG plans on activating in the near future? Samsung already uses the web camera on its line of smart TVs to provide custom programming and advertising recommendations to whoever happens to be sitting in front of the TV at that time.
The question becomes: How far are manufacturers willing to go before consumers fight back against these privacy violations?
At this time, the only way to determine the specific privacy policies of your TV model is to carefully read through any material that came with the appliance and research a new product before making a purchase decision.
Of course, leaving your TV disconnected from the Internet whenever possible also helps, but this often presents a big inconvenience to most users.
As usual, the need for new technology as created new privacy concerns for consumers and at this point, there doesn’t seem to be an end in sight.
It’s Not Just Your Online Bank Account You Need to Worry About
26.11.13
Two young brothers were taken into custody in Northern California late last month after authorities allege that they have been responsible for millions of dollars in wire fraud over the last couple of years. Although some of the fraudulent activity traces its roots back to traditional online banking fraud, most of the brothers’ income came from hijacked online brokerage accounts in the United States. Basically, Adrian and Gheorghe Baltaga (aged 25 and 26) have been charged with stealing login credentials from online brokerage powerhouse Fidelity Investments. Once an account was successfully compromised, the Baltaga’s would set up fake Automated Clearing House (ACH) links between the compromised accounts and prepaid debit card accounts controlled by the hackers.
Once the stolen money was on the prepaid debit cards (which are increasingly relied on for all types of fraudulent activity including the Social Security scam this website covered last month), the hackers purchased MoneyGram and US Postal Service money orders that could be deposited into regular checking accounts in Northern California banks. The funds were then withdrawn from various ATMs in the Fresno, California area at the discretion of the hackers.
This wide-reaching and profitable scam has been going on for at least a couple of years. In 2012, a Maryland title company was robbed of almost $1.7 million as a direct result of a compromised investment account at Fidelity that was hacked by the Baltaga brothers.
In this case, the brothers has installed a copy of the Zeus banking trojan on an employee’s computer at the Maryland company. In case you are unfamiliar, Zeus is designed to log keystrokes on infected computers. With this software installed, it was relatively easy for the Baltagas to hijack the brokerage account at Fidelity and begin moving money through seemingly legitimate ACH transactions. Since being charged, the government has seized the 5 bedroom, $800,000 Fresno home purchased by the brothers last year.

At this time, the lawyer representing these hackers is unavailable for comment. The problem is that although online banking fraud is relatively commonplace these days, hijacking online investment accounts is a new take on an old trick.
Unfortunately, many brokerage houses are not held to the same security standards as modern banks and this leaves the door wide open for hackers.
Coupled with the fact that many investment accounts have more money available than the victim’s respective bank account, you have a seriously tempting scam for would-be hackers. Also, businesses are often not given the same protections under financial law afforded to consumers.
This means that companies affected by this scam – including the Maryland title company – have a serious uphill battle ahead of them when it comes to reclaiming lost funds.
Most of the hijacked accounts in this scam come as a result of the Zeus banking trojan. Although this malware is notoriously difficult to detect, most updated antivirus software is capable of stopping the software from causing excessive damage. Make sure your antivirus and OS are properly updated to help protect against financial-targeting malware such as Zeus and Citadel.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion