News Archive July 2014
Monthly Cyber Security News Archive: July 2014 Summary
Table of contents:
- Users of the Tor Network Being Watched by the NSA
- The World Cup Isn’t the Only Thing Happening in Brazil
- The ‘LOL’ Facebook Scam
- Emotet Banking Trojan Discovered
Users of the Tor Network Being Watched by the NSA
03.07.14
Last summer, Edward Snowden made headlines by leaking classified documents pertaining to illegal surveillance activities being performed by U.S. government agencies including the NSA. One of the secret programs revealed in these documents is known as X-Keyscore; a program whereby the NSA was secretly spying on nearly all Internet traffic around the world without consent or a legal right to do so. A recent analysis of the X-Keyscore source code reveals that the program was specifically designed to add anyone using popular Internet privacy tools including the Tor Network to NSA surveillance lists.
The source code also revealed that the program had specifically targeted a German student currently operating a Tor node. The Tor Network was originally designed by the United States as a way to secure private Web browsing sessions using a series of anonymous nodes to route IP addresses around the world before landing at the intended machine. The Tor Network is often used by activists and reporters to ensure anonymity but it is also associated with black market operations like the Silk Road (which was shut down last year) and by illicit pornographic websites.
Records indicate that the X-Keyscore program allows NSA employees to obtain phone numbers and email addresses, view email content and even observe the Internet activity of people under surveillance without a warrant.
Even more alarming is another code snippet found within X-Keyscore’s source code which is designed to keep track of all visitors to torproject.org; whether they ultimately end up using the service or not.

Despite this disturbing news, the Electronic Frontier Foundation (EFF) urges people to continue using the Tor Network and similar services such as Tails (a variant of the Linux operating system that can be launched from a USB drive and includes tools with pre-configured privacy settings.
A spokesperson for the EFF said “the more ordinary people use Tor and Tails, the harder it is for the NSA to make the case that reading about or using these tools is de facto suspicious.”
Also interesting is the fact that a security expert interviewed following the leak of the X-Keyscore source code hinted at the possibility that this latest leak is not from Edward Snowden. Although this has not been confirmed at the time of this writing, the existence of a potential second source infers that Snowden may have inspired others working for the NSA. Ultimately, this means even more information could come to light about these clandestine projects in the near future. Although there is a chance the NSA is already watching everything you do online, using the Tor Network (or even visiting the Tor Network website) is a guaranteed way to get put onto a government watch list – whether you are doing anything illegal or not.
The World Cup Isn’t the Only Thing Happening in Brazil
12.07.14
Researchers from RSA recently discovered a botnet crime ring responsible for stealing nearly $4 billion (USD) over the last two years in Brazil. The botnet is being referred to as “Boleto malware” because it specifically targets the Boleto Bancário – the second most common payment method in Brazil (only credit card payments are more common). The boleto is similar to a money order and is used by consumers and for most business-to-business payments in the country. Brazilians can use boletos to complete online purchases using an online banking interface and much like Bitcoins and other electronic payment methods there are no chargebacks or dispute resolution procedures one expects from a credit card company. RSA estimates that in the two years this malware botnet has been active, nearly 500,000 boleto transactions have been compromised.
Currently, the malware affects 34 different banks within Brazil. The botnet works by infecting web browsers in what is commonly referred to as a “man in the browser” (MITB) attack. Once the malware is successfully installed on a victim’s computer it intercepts and modifies the boleto payment information between the customer, bank and merchant. Ultimately, the payment is redirected to an account belonging to the botnet operators without the knowledge of the customer or the bank. Since there is no dispute resolution or fraud protection inherent to this payment method, customers have little possibility of recovering the stolen funds.
The criminals behind the malware appear to target small transactions as they are less likely to raise a red flag for the victim. The current version of the botnet targets Windows machines running Windows XP, Windows 7 and Windows 8.
It operates within all popular web browsers including Internet Explorer, Chrome and Firefox and is estimated to have control of over 192,000 PCs at this time (based on unique IP addresses). In addition to being extremely dangerous, the malware is hard to detect or reverse engineer because it uses an obfuscated AutoIt script packed with UPX. The malware also copies itself to the Application Data folder and adds a registry key to run at startup.

Once injected into the web browser, Boleto malware searches for specific, bank-issued security plugins installed on the client-side for creating and securing Boleto transactions. Once located, the shared libraries for these plugins are modified in real-time to neutralize their functions. Although the security plugins appear to be functioning properly, they are simply giving victims a false sense of security as the plugins leave the transaction wide-open for modification by the cybercriminals behind the botnet. As with so many other recent malware outbreaks, Boleto malware is spread using email.
The botnet is also capable of harvesting email credentials from infecting machines; a tactic it uses to continue spreading the botnet through compromised email accounts. Although this attack appears limited to Brazil for now, the same (or similar) malware could be used to intercept electronic payments in other countries in the future.
This is especially true as more people turn to crypto currencies like Bitcoin when making online purchases. Security experts say it is nearly impossible to detect the presence of this botnet as many popular antivirus solutions are still working to generate a definition for the malware. Until this malware has been properly identified and can be blocked by antivirus solutions, avoid opening any unsolicited email attachments regardless of where the message originated.
The ‘LOL’ Facebook Scam
19.07.14
As text messaging and instant messaging via services like Facebook, Skype and others redefine the American dictionary, hackers are catching on. A new scam has popped up on Facebook that can already claim hundreds of thousands of victims – and the numbers continue to climb. This scam is actually a Trojan designed to steal Facebook login credentials and spread itself like wildfire through the most popular social media platform to date. According to Malwarebytes (a computer security firm responsible for developing a free malware removal tool), the Trojan has other purposes as well.
Unfortunately, the other purposes have not been defined as of this writing but what is known is that the Trojan injects itself into multiple legitimate processes on the victim’s computer. Like previous Facebook scams, the LOL Trojan is spread via Facebook’s Messenger service by leveraging compromised accounts to send messages to friends.
The Trojan gets its name because the message simply says “LOL” with an attachment usually named IMG or PHOTO. The attachment is a ZIP file which contains the Java necessary to launch the Trojan.
Additional files needed for operation are downloaded from an anonymous Drop Box account. What’s unique about this particular malware variant is that it seems to incorporate all previous successful tactics used for social media scams into one package. The first tactic is use of the Messaging service. Just about every previous Facebook scam has also used this service.
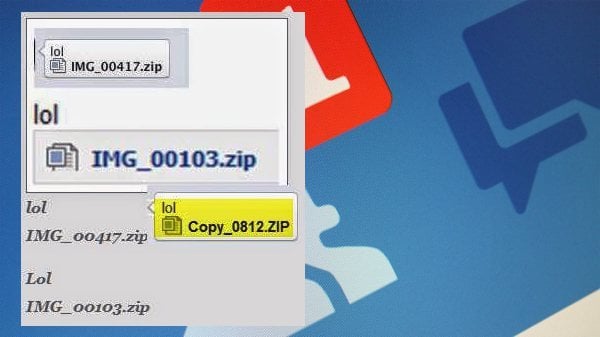
It is also the preferred method for sending malicious files via Skype, MSN and Yahoo (among others). Second is the use of ‘LOL’ which is used simply as an attention grabber. Similar scams have used terms including “OMG, is this you?” and “I can’t believe someone posted this.” In all three cases the idea is simply to grab the users’ attention using common messaging slang. The third tactic is the use of the ZIP format which is designed to hide the malicious contents of the download until it’s too late. Finally, this Trojan makes use of the JAR (Java Archive).
While Java is typically used to exploit vulnerabilities in ‘drive-by download’ attacks, the criminals behind this scam are using JAR files to download the contents of the Trojan.
In other words, the ZIP itself does not contain malicious code. Instead, it downloads malicious code once installed. This makes it much more difficult to detect by most antivirus software on the market. Security experts investigating this threat have been unable to determine who is behind this latest threat but states that the person responsible for coding the Trojan is likely Greek based on some of the text found within the Java file. To protect yourself from this threat, do not download any messages with ‘LOL” as the only text (even if sent from a friend) and never download and execute a ZIP file from within a Facebook message.
Emotet Banking Trojan Discovered
21.07.14
It seems like one of the newest and most effective trends in banking Trojans is spam email regarding a bank transfer or an invoice. Although many PC users have become wary of these email scams, a new banking Trojan designed to steal personal financial information is still a worthy foe. Named Emotet by security researchers from Trend Micro, this new malware variant takes a slightly different path when attempting to steal your personal information. Most banking Trojans steal information by injecting rogue forms into Web browsing sessions.
Emotet, on the other hand, uses browser network APIs to sniff outgoing traffic. Like other banking Trojans before it, Emotet is primarily spread using spam emails masquerading as bank transfer notifications or invoices – anything that is likely to get attention in a typical email inbox. Once installed on a victim’s computer, Emotet downloads additional components from a C&C server. It also downloads a configuration file containing the URLs the malware should search for and target within network traffic.
According to Trend Micro, the Trojan was originally designed to target German banking websites although a quick change to the configuration file is all that’s necessary to target any banking session in the world.
The main component of Emotet is responsible for downloading a Dynamic Link Library (DLL) file which is injected into all processes running on the PC (including Web browsers). This DLL has the ability to monitor all outgoing network traffic as it searches for URLs or strings specified in the configuration file. Once a match is found, Emotet assembles the URL and the data sent. Essentially, the malware saves the entire content of the visited website. All data sent is saved and sent to the hackers responsible for this banking Trojan.

The malware is also capable of sniffing data from encrypted browsing sessions. This is because Emotet hooks directly into the network APIs used by Web browsers when communicating across the Internet. What makes this Trojan so dangerous is that it is extremely difficult to detect compared to “traditional” banking Trojans relying on phishing or rogue form fields injected into Web pages. Emotet attempts to avoid detection even further by encrypting stolen data and storing it within the infected system’s registry. Since it doesn’t create files on the system, many antivirus solutions are unable to detect the malicious purpose of Emotet until it’s too late.
Although this Trojan was first detected in Germany, it has also been found on systems located in North America and Asia. This reinforces the fact that a simple change to the configuration file means that Emotet is capable of stealing banking information anywhere in the world.
At this time, it is unclear whether Emotet is being controlled by a single cybercrime ring or if it is being “rented out” to other criminals in a manner similar to the Gameover botnet and other banking Trojans based off the leaked Zeus source code. If you receive an email from your bank about a pending transfer, do not open the email. Instead, call the bank directly and confirm that a correspondence was sent because opening the email could infect your machine with an Emotet variant that is undetectable by your current antivirus solution.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion