Preventing Ransomware Infections
Table of Contents
Introduction
It has been roughly 10 years since ransomware attacks began. Since then they have become one of, if not, the go to malware for extorting money from victims. In the 10 years they have become increasingly complex and advanced and are most certainly making a greater nuisance of themselves. Ransomware attacks have risen exponentially since their inception and are now part of our modern day lexicon. Recent ransomware attack campaigns such as WannaCry made international headlines, often these headlines and subsequent articles often dealt with the cost and inconvenience caused. Little attention was given to what is ransomware, how it is distributed, and perhaps most importantly how to prevent becoming a victim of such an attack. The intention of this article is to cover in more detail those aspects ignored in short new segments.
What is Ransomware?
To give a basic definition of ransomware it is important to look at what the malicious program seeks to achieve as well as the cyber-criminal deploying the program. Essentially the malicious program looks to encrypt user’s data so they cannot access their files. Often files that are encrypted would be file types essential to business or personal information that can destroy reputations or jeopardize compliance regulations. Once files are encrypted a ransom note is made available to the user that instructs how payment must be made to essentially decrypt the data. In summary, the user’s data is effectively taken from them till they pay a ransom. More often than not payment is to be paid in Bitcoin or another cryptocurrency. These are used as they grant the one demanding the ransomware a certain degree of anonymity.
Ransomware, historically has come in two broad types. One of the first kinds of ransomware released looked to lock the users screen so the user could no longer access their computer at all, often referred to as locker ransomware. The popularity of this type of ransomware appears to be in decline. The second type, more often used, are ransomware variants that encrypt certain files, generally allowing the user limited access to their computer. This limited access is intended to allow the user to make payment easier and hopefully in a timelier manner. These are referred to as crypto-ransomware. Over the years there have been numerous terms to describe ransomware adding further confusion. Terms like crypto-ransomwares, cryptoviruses, and CryptoLockers have been used to describe ransomware. In order not to add to any further confusion the term ransomware is used in this article to describe a malicious program which encrypts, or limits the user’s use of their computer with the intention of extorting a ransom.
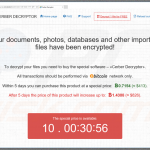
Screenshots of 4 most widely spread ransomware Cerber, Locky, CryptXXX and Jaff:
Summary of the attack
While ransomware attacks are on the rise, data from 2016 shows that such attacks increased by a factor of three in that year, it is essential to know how such an attack is carried out. That is how the malicious program is delivered, deployed, and how the ransom is extorted. How the ransomware is delivered to the system is investigated in greater detail latter on but will be briefly touched on in this section. The reason why delivery is dealt with in greater detail is because if you can stop the delivery of the ransomware you stop its deployment in its tracks. The following can be seen as a summary of the attack:
- Delivery: The ransomware is delivered to the soon to be victims system in one of two ways. Either by email, or by exploit kit attached to a compromised website. (This will be covered in greater detail below.)
- Execution and Encryption: Often the creators of the program will include numerous measures to avoid detection by anti-virus programs. An increasingly popular method is by code injection, which injects the code into authentic services used by the operating system. Once anti-viruses and firewall have been successfully avoided the ransomware will begin searching for files it has been programmed to encrypt. Often these can be .docx .xlxs, or certain types of image files that will be targeted. More advanced ransomware variants can even spread to network drives in an attempt to infect other computers and systems connected to the initial target. Once the files have been found the program will encrypt the encryption process begins. This can take minutes or seconds. The Chimera variant successfully encrypted files in 18 seconds. Often 128 bit encryption protocols are used making decryption exceptionally difficult and virtually impossible for someone without the required knowledge.
- The Ransom: Once the encryption is complete a ransom note or lock screen will be displayed instructing the user that their files have been encrypted and that they have a certain amount of time in order to make payment otherwise their files will be encrypted permanently. In theory once payment is received the cyber-criminal will send the decryption code. There have been instances where payment was made but no code was received in order to decrypt the files. It is important to remember that if you are willing to pay you are often dealing with a criminal enterprise, not people with moral principles guiding their immoral business. As always there is no guarantee that once payment is made you will receive the decryption code. On a side note there are business which develop removal and decryption guides, such as our website, these may help in a case if infected.
Although the above summary is a simplified summary of how the attack occurs in practice it does provided a unique insight into how ransomware is delivered, deployed, and cryptocurrency extorted from the victim. Following this will be a further discussion on how these malicious programs are delivered, or distributed, and then how these attacks can be prevented.
How Ransomware is delivered
As was mentioned above ransomware is delivered via two main method. Those been email or exploit kits. If users are aware of how these malicious programs are delivered it makes prevention a far easier prospect. Each method will be examined in turn:
- Email: Email has become a favored method for distributing ransomware and malware. One of the reasons it is favored is because it can be relied upon, as well as been an easy method of distribution. This method of using emails is often called phishing. An email which looks like a legitimate email which may appear to be from a legitimate company is sent with attachments which contain the ransomware, often with other types of malware as well. Once these attachments are opened the ransomware will automatically install on the users system. The creators of the ransomware can also link compromised websites, rather than using compromised attachments. Phishing has proven to be major successful, it was estimated by Verizon that 30% of phishing emails were opened in 2016. So the hit rate is nearly a third of all emails. It has been adopted by ransomware developers as a major distributing method for that very reason.
- Exploit kits: Basically an exploit kit allows the ransomware developer to upload malicious code to any website they have access to. The code is designed to exploit vulnerabilities in the software the user might be running. In the past Adobe’s Flash Player has been exploited to deliver ransomware and various other forms of malware. Unfortunately, this is not limited to sketchy websites. In order to boost the infection rate the developers will use legitimate and popular websites to distribute ransomware. While this is ominous, it is no reason to stop users from enjoying many of the benefits the Internet provides. The best protection against such attacks is simply keeping your software up to date. Software developers often use updates to erase vulnerabilities in their software, thus limiting the vulnerabilities users are exposed to. As we will see updating software is one of the primary ways to prevent infection.
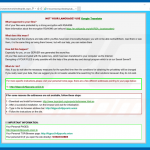
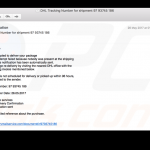
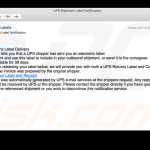
Screenshots of email messages that are used by cyber criminals to spread ransomware:
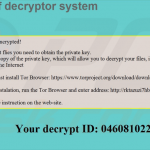
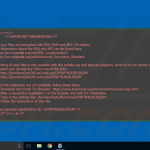
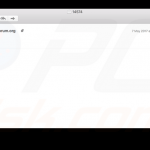
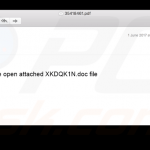
Screenshots of infected email attachments - malicious documents that contain macros that, once enabled install ransomware on victim’s computer:
While all that has been covered so far can seem very disheartening there are ways to prevent infections. As the old adage goes “prevention is better than cure”, the same applies to ransomware and many of the methods of preventing attack are incredibly easy to carry out. Often they require just a little discipline and instituting a process. When one considers that it often costs an average of 500 USD to decrypt already encrypted files, prevention is something your wallet will appreciate.
How to prevent against infection
The following can be seen as a how to guide to increase your security posture in all matter cyber-security. These are easy to implement and often require no capital outlay, rather been aware of the threats you face daily by just using a computer connected to the internet. Here are four methods to assist in preventing ransomware infection:
- Ensuring Software is updated regularly: Software developers are constantly updating software with one of the key aims being to reduce the amount of vulnerabilities that can be exploited by cyber-criminals. Most software will inform you when an update is required, or will auto-update if you do not switch this function off. It can be seen as a pain to constantly update your system and software but when you consider what might go wrong a minor inconvenience is always preferable to a major one. It the recent spate of WannaCry attacks one of the main reasons the attack was so widespread was because people had not download and installed vital security updates. In many cases where people were blaming Microsoft, rather than the cyber-criminals themselves in certain cases, Microsoft had already realized updates to prevent exploitation of the vulnerabilities WannaCry, though the use of DoublePulsar, exploited.
- Installing Antivirus Software: This not only prevents ransomware attacks but also prevents numerous other malware attacks. There are numerous products on the market and will require some market research on your side as to which companies are reputable. The same applies to other software though in that you must keep your antivirus software up to date. This is done so that the software can block the latest malware variants. This method of prevention does require to spend hard earned money but in the long run it may save you from attack and having to spend money funding an organized crime syndicate rather than a company tasked with protecting your computer.
- Take care in opening emails and be suspicious of pop-ups: While there are excellent email filtering products available on the market to further increase your security posture. It is advised to purchase such a product, many variants of ransomware can be prevented by adopting your own filtering process. Firstly, when opening emails look to see if it is being sent by a legitimate source, this can be easily seen when looking at the address of the sender. If it looks suspicious do not opening any of the attachments. In the body of the email quickly scan for obvious spelling mistakes and grammatical typos. It is unlikely that companies will send out email communications containing obvious errors as it reflects badly on the company. Also be aware that banks and other financial institutions will never ask you for sensitive information such as passwords to access Internet Banking via email. Some ransomware variants will require you to click on a pop-up in order to deploy the ransomware. Do not click on the pop-up rather close it safely to prevent infection.
- Get in the habit of creating backups: This does not necessarily relate to prevention but if your system is infected it will allow the user to delete and restore all the data backed up from a previous date. By creating regular backups you can mitigate the potential disastrous outcomes been infected with ransomware can entail. Creating backups is not only advised for combating cyber threats but also in the event that a computer fails. As an extra precaution backups can be made on a removable hard drive which can be unplugged from the computer and stored in a safe place.
Simply by employing these for measures one can successfully defend or prevent against a ransomware attack. Further businesses and large corporations can institute stricter security policies which restrict privileged access to only those educated as to the threats faced by the organization. Policies like contacting the IT department if an employee receives a suspicious email can save the company literally millions of dollars in the event of a malware attack or data breach.
Conclusion
One of the key components in combating cyber-threats has always been education. To that extent it is hoped that this article has shone a light on what ransomware is, how it is distributed and importantly how to defend against attack or preferable how to prevent an attack all together. By employing the methods listed above you will surely increase your security posture and most definitely take great strides in preventing attack. Just by making backups, for example, you have limited the damage done by ransomware attack if infected. It is hoped you have found this article informative and enlightening as to the threats posed by living in the digital age.