GoldenEye not Ransomware
The recent variant of Petya, also called GoldenEye or NotPetya, is believed by security researchers globally to be malware type known as a wiper rather than the ransomware originally reported on. For the purposes of this article, the malware will be referred to solely as NotPetya for the remainder of the article in order to keep confusion down to a minimum. While it initially did appear as ransomware by demanding a ransom to decrypt data that had been encrypted as well as leveraging EternalBlue and EternalRomance as if earlier ransomware attack campaigns. Added to this victims were instructed to pay the ransom in the now traditional method of Bitcoin. Once analyzed by numerous researchers in numerous leading security companies, the truth does appear stranger than fiction.
Misdirection
So what did the experts discover that would lead them to this conclusion? In summary, there are a variety of reasons that support this view. Travis Farral, Director of Security Strategy at Anomali had the following to say about the matter:
A number of us in the security community are debating if the Petya attack on 27 June wasn’t a targeted attack on Ukraine, disguised as a ransomware attack on any organization caught up in the method used for infection…There are details that support such a theory. The attackers behind the ransomware haven’t experienced much ROI despite the broad impact of the attack, they set up a weak payment process, launched the attack just prior to Ukraine’s Constitution Day and leveraged a malware family named for the pet name of Ukrainian President, Petro Poroshenko.
Added further to what Farral stated when one considers the original Petya was intended to encrypt the Master Boot Record, then demand a ransom to decrypt it. NotPetya overwrites the Master Boot Record but does not save it elsewhere. This would cause irreversible damage to the drive and would mean that no decryption is possible even if you paid the ransom. Researchers, in turn, noticed that NotPetya was generating random data when to generate an installation ID displayed to the victim. Further emphasizing the point that now decryption can take place.
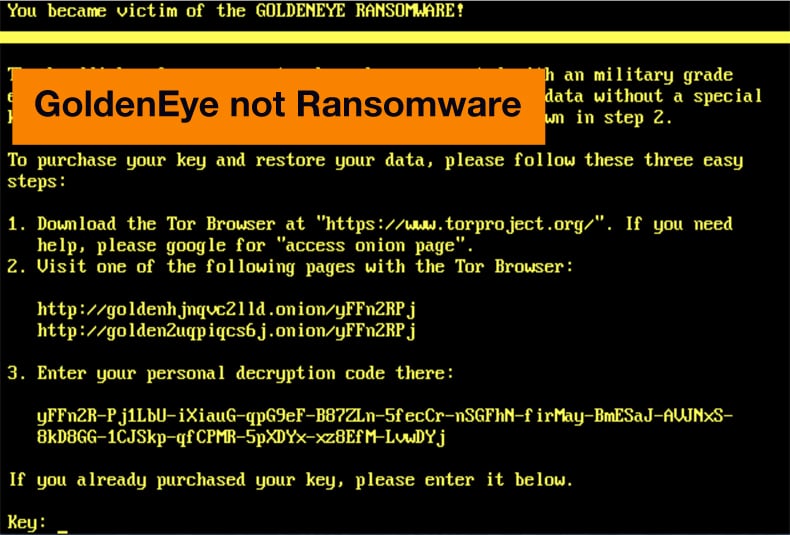
When researchers dug a little deeper into the method the attackers chose to extort payment, more questions arise. Why would they use only one email address, easily shutdown to manage all the payments? All payments would need to be checked manually, while the way the campaign was carried out showed that the attackers were not amateurs or opportunists. When considering the questions raised as well as how the malware wipes the Master Boot Drive rather than encrypt the goals of the attackers can be safely assumed not to be financial. Rather they are destructive.
Links to TeleBots
Given that the attack used Ukrainian accounting software as one of its chosen attack vectors has led many to believe that the attack is linked to TeleBots, the hacking group which is believed to be behind the successful shut down the Ukrainian power grip in 2015 using the malware BlackEnergy and attacked the Ukrainian banking sector a year later. The Ukrainian state security agency SBU has gone on record to state:
The available data, including those obtained in cooperation with international antivirus companies, give us reason to believe that the same hacking groups are involved in the attacks, which in December 2016 attacked the financial system, transport and energy facilities of Ukraine using TeleBots and BlackEnergy…This testifies to the involvement of the special services of Russian Federation in this attack.
While the Ukraine has not been shy at blaming Russian hacking groups believed to be supported by the Russian government, independent companies analyzing the attack discovered similarities between NotPetya and BlackEnergy. Both use the KillDisk wiper. What has also been noted is coding similarities but this is by no means a smoking gun which definitively proves the group's involvement. While there is no definitive proof extensive forensic investigations conducted by FireEye linking Telebots to the Russian government. However, Russia has denied any implication in the NotPetya attack as well previous attacks alleged to be supported by their government.
Evidence is thin at best
While there is no real direct evidence proving TeleBots of being involved, there is circumstantial evidence. That, however, is not enough to prove anything despite the Ukrainian state security agency’s statement. That is not to say that there may not be truth behind the statement it is perhaps unwise to make blanket statements in an age of political uncertainty with cyber-attacks been able to flare up regional disputes with ease.
With the uncertainty as to who perpetrated the act and who the main targets were, there is one piece of evidence that certainly does remain. Much of the world’s media and a fair number of experts were duped into believing the attack was a ransomware attack. This undoubtedly assisted the attackers in achieving their aims whether political or personal. In an age where news stories need to be broken to the public as soon as possible, this would not be the first time, nor the last, that the media will be used as a smokescreen to hide possible intentions and outcomes. In time the public will learn who exactly was behind the attack but given the nefarious and often anonymous nature of cyber-crime, it will take some time.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion