How Hackers Cash Out Their Stolen Cryptocurrency
With the arrest of Alexander Vinnick, a 38-year-old Russian who was believed to be one the creators and operators of BTC-e on money laundering charges. The total believed to be laundered through the platform totals over 4 Billion USD. The laundered funds are believed to be in conjunction with cyber-attacks, tax fraud, and drug trafficking. The man was arrested by Greek police at the request of US law enforcement agencies.
The arrest will hopefully further shine a light on how cyber-criminals, once they have either stolen or extorted cryptocurrencies are able to launder that money in order to be used legitimately.
How the criminals are able to cash out
Whether it is from ransomware campaigns or direct theft from legitimates user's cryptocurrency wallets, it is very difficult to survive solely on the cryptocurrencies. What is then needed is someone willing to launder the money in a similar vein to how it is done in other illicit trades and black market operations.
In recent news Ethereum, one of the most popular cryptocurrencies which have seen explosive growth in the market has been hit by a spate of thefts from Ethereum wallet accounts. One hack totaled 32 million USD worth of the crypto currency. While another totaled 8,4 million USD. If we take this real life instances as examples, how then does the hacker convert the cryptocurrency to a form of currency they can use legitimately?
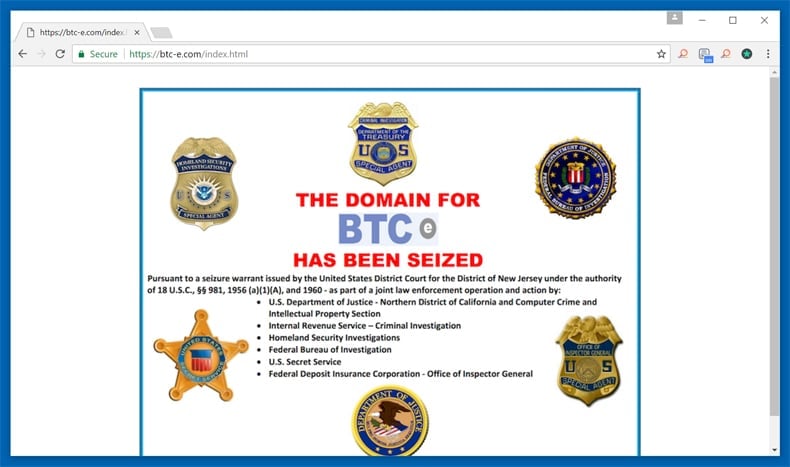
That is where exchanges like BTC-e come in. Exchanges like the one mentioned will allow hackers and other criminal organizations to cash out their cryptocurrency anonymously. According to Google researchers, researching the viability of ransomware and its effect on users, 95% of traced ransoms were cashed out via BTC-e. Although on paper this sounds relatively easy tracking anonymous payments is anything but. Researchers like Luca Invernizzi, Kylie McRoberts, and Elie Bursztein have to “…uncover the cash-out points, tracking how the money exits the Bitcoin network, enabling the authorities to pick up the money trail using conventional financial tracing means,”
In order to do that the researchers had to follow the money trail step by step. Not only did this show how illegal payments were being cashed out but how certain ransomware families had evolved over the given period since 2014. This step by step analysis revealed some interesting trends. The first being that Locky and Cerber were the two ransomware families that managed to extort the most Bitcoin from victims with both families raking in millions of dollars’ worth of Bitcoin. Ransomware as a service (RaaS) is also drastically on the rise as result of ransomware perceived economic viability.
High-risk high reward
For hackers as well as those willing to launder the ill-gotten gains the payoff can be considerable. However, if caught the risky nature of the business is all too apparent. In Alexander Vinnick’s case he faces the following jail time if convicted of the following crimes he will have to stand trial for:
| Violation | Statute | Maximum Penalty |
| operation of an unlicensed money service business | 18 U.S.C. § 1960 | 5 years of imprisonment |
| conspiracy to commit money laundering | 18 U.S.C. § 1956(h) | 20 years of imprisonment and a $500,000 fine or twice the value of the property involved in the transaction |
| money laundering | 18 U.S.C. § 1956(a)(1) | 20 years of imprisonment and a $500,000 fine or twice the value of the property involved in the transaction (each count) |
| engaging in unlawful monetary transactions | 18 U.S.C. § 1957 | 10 years of imprisonment and a $500,000 fine or twice the value of the property involved in the transaction (each count) |
In a statement made by the Acting Director of Financial Crimes Enforcement Network (FinCEN):
We will hold accountable foreign-located money transmitters, including virtual currency exchangers, that do business in the United States when they willfully violate U.S. anti-money laundering laws…This action should be a strong deterrent to anyone who thinks that they can facilitate ransomware, dark net drug sales, or conduct other illicit activity using encrypted virtual currency. Treasury’s FinCEN team and our law enforcement partners will work with foreign counterparts across the globe to appropriately oversee virtual currency exchangers and administrators who attempt to subvert U.S. law and avoid complying with U.S. AML safeguards.

Photograph: Giannis Papanikos/AP
As to why the US agency felt it had the jurisdiction to go after Vinnick it provided the following rationale:
BTC-e has conducted over $296 million in transactions of bitcoin alone and tens of thousands of transactions in other convertible virtual currencies. The transactions included funds sent from customers located within the United States to recipients who were also located within the United States. BTC-e also concealed its geographic location and its ownership. Regardless of its ownership or location, the company was required to comply with U.S. AML laws and regulations as a foreign-located MSB including AML program, MSB registration, suspicious activity reporting, and recordkeeping requirements. This is the second supervisory enforcement action FinCEN has taken against a business that operates as an exchanger of virtual currency, and the first it has taken against a foreign-located MSB doing business in the United States.
Thus believing Vinnick and the other people behind BTC-e broke US Anti-Money Laundering laws.
In the wake of this arrest, it will be far harder for hackers to be able to cash out and a stepping up of international law enforcement agencies targeting criminals often where it hurts most. That is always inevitably the wallet. This arrest as well as the recent arrest of a US citizen, Kamyar Jahanrakhshan, in Canada accused of committing numerous DDoS extortions, sends out a strong message to law enforcement agencies.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion