Bad Rabbit Ransomware Hitting Russia and Ukraine
News broke on October 24 of a new ransomware variant targeting Russian and Ukrainian systems. The ransomware infected both personal computers and company servers. Among the affected organizations are Kiev’s metro system, Russian media organization Interfax and Odessa airport. Interfax was forced to publish to its Facebook page during the outage since its servers were taken offline for a number of hours.
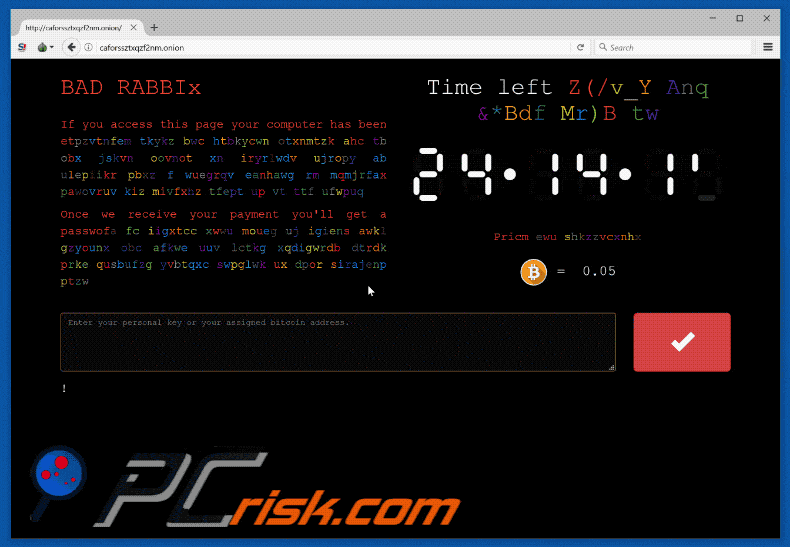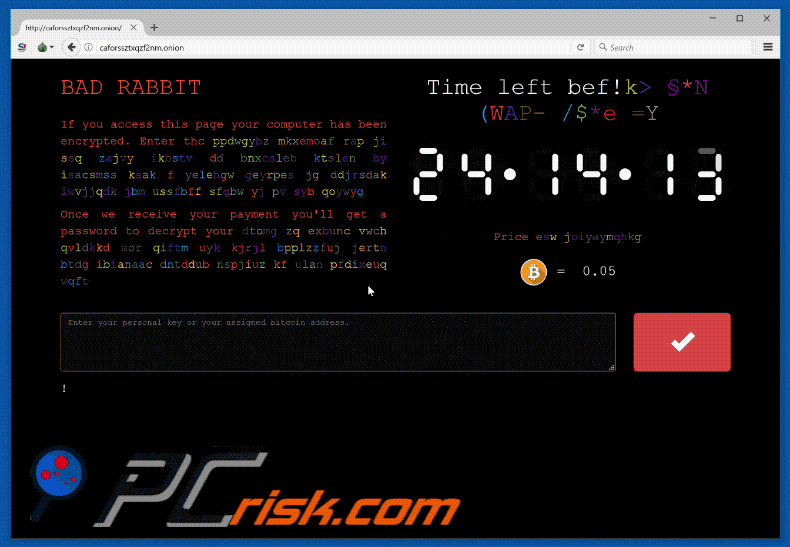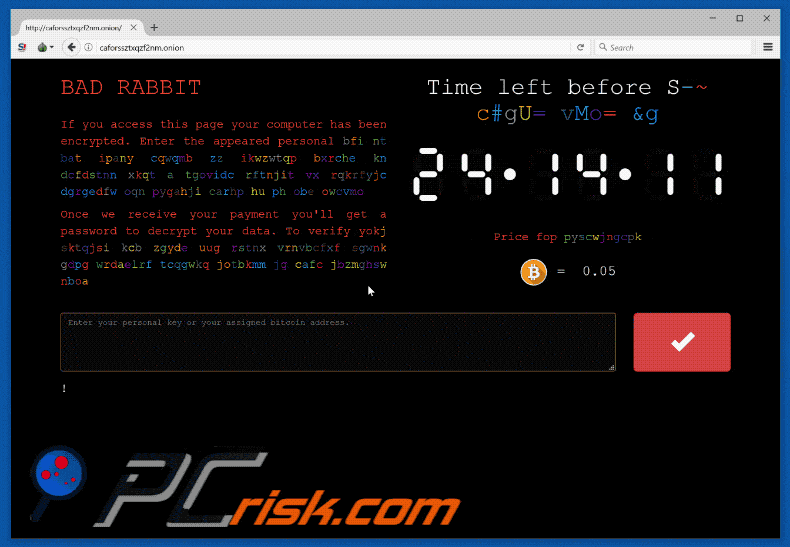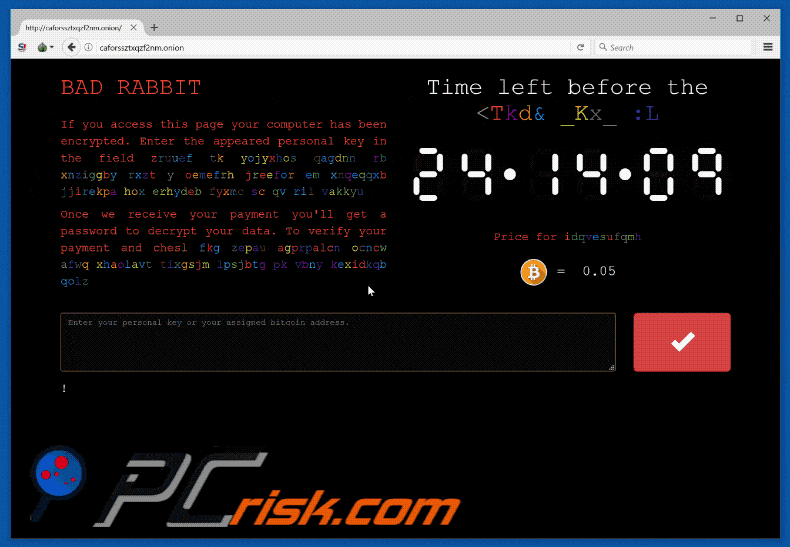
The ransom demanded is 0.05 Bitcoin ($287.65 at the time of writing) and is conveyed in the now customary method of a ransom note. The malware code is unusual in the sense that it is laced with pop culture references pertaining to the hit show Game of Thrones, whose holding company HBO has its own battles with cybercrime. The ransomware also tries a list of passwords while attempting to spread which include “love”, “sex”, “god” and “secret”, which were dubbed the “four most common passwords” by the 1995 movie Hackers. In fact, the four most common passwords are 123456, 123456789, qwerty, and 12345678.
Similarities between Bad Rabbit and NotPetya
Researchers at Kaspersky Labs have been monitoring and analyzing the ransomware since its detection earlier this week. In their analysis, they have noticed similarities between Bad Rabbit and NotPetya, the wiper masquerading as ransomware which caused billions of dollars’ worth of damage in July this year. The first similarity comes down to the text used in the ransom note been phrased similarly. The attack vectors used are also similar. Bad Rabbit targeted legitimate websites by utilizing a malware dropper downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. Neither is the first time Adobe Flash player has been abused to spread malware. Kaspersky discovered that many news and media websites were compromised throughout the campaign. The NotPetya outbreak began through the release of a compromised version of a popular Ukrainian accounting program, spreading automatically throughout corporate networks.
However, the strongest link between the two malware types is based on the web servers which were used to distribute the initial software. Costin Raiu, a researcher at Kaspersky told Forbes that a network of hacked sites initially linked to NotPetya in July was now being used to host secondary distribution channels for Bad Rabbit.

Differences between Bad Rabbit and NotPetya
While there are important similarities to consider the two are different enough to be considered different malware types. Where NotPetya was targeted at Ukraine, Bad Rabbit appears to have primarily hit Russian businesses. Bad Rabbit has been detected in other Eastern European countries including Poland and has been detected in Germany. Another key difference is that Bad Rabbit did not the EternalBlue exploit believed to have been developed by the NSA before being stolen by a hacking group known as The Shadow Brokers, to spread within corporate networks. That decision may have limited the dispersal of the outbreak.
The biggest difference is perhaps that Bad Rabbit is not a wiper as NotPetya was suspected to be. NotPetya was basically impossible to remove, even for users who attempted to actually pay the ransom, leading to suspicions it had been created more to cause damage and destruction than raise revenue for its developers. Bad Rabbit, however, does decrypt the hard drive on entry of the correct password.
Bad Rabbit likely the work of TeleBots APT
Many security firms have released reports analyzing the possible link between TeleBots and Bad Rabbit. Companies like Bitdefender, Cisco Talos, ESET, Group IB, Intezer Labs, Kaspersky Lab, and Malwarebytes, have all published articles on Bad Rabbit, with most of them emphasizing the similarities in source code between Bad Rabbit and NotPetya attributed to TeleBots. It was ESET that tied TeleBots to NotPetya back in June who became infamous when they attacked Ukraine’s power grid in December 2015 and a year later in the same month. The group behind has been active since 2007 and is tracked under different names, such as Sandworm, BlackEnergy, and most recently as TeleBots, while other lesser known names include Electrum, TEMP.Noble, and Quedagh.
Many suspect the group operates out of Russia and is under the control of Russian authorities because hackers refocused operations to Ukrainian targets right after Russia invaded the Crimean Peninsula, a former Ukrainian territory. However, Bad Rabbit did not exclusively target Ukrainian interests. In fact, approximately 70% of the targets were Russian. While this is most certainly the case, the fact that both share the same infrastructure, as reported by researchers at Kaspersky and RiskIQ is telling. It appears as if the infrastructure could have been developed as early as 2016. It is normally only state-sponsored advanced persistent threats who can afford to take their time in developing the infrastructure necessary to conduct operations attributed to TeleBots.
Bad Rabbit may be a ruse
If TeleBots is indeed behind Bad Rabbit it may be a ruse, similar to how NotPetya presenting itself as ransomware but turned out to be a wiper. This would most certainly be in line with the group’s current operations model. Some experts have suggested that while many security firms are focussed on treating Bad Rabbit as ransomware it could be quietly siphoning off data from sensitive targets. That is one option, another may be to deploy the ransomware as a way to destroy evidence of previous undetected intrusions.
Deploying ransomware as a cover may seem like a novel idea but one we are witnessing in reality. It is believed that hackers operating out of North Korea deployed the Hermes ransomware variant as cover for the hack on the Far Eastern International Bank (FEIB) in Taiwan. Investigators discovered that fraudulent attempts to wire as much as $60 million to foreign banks located in Sri Lanka, Cambodia, and the United States occurred. This hack was attributed to the Lazarus Group, an advanced persistent threat known for committing bank heists using SWIFT accounts.
It seems such advanced attacks will increasingly become the norm. Carl Leonard, a principal analyst at Forcepoint, believes:
We will continue to see massive attacks with economic, employee and public safety ramifications. And the methods will continue to evolve, including the evasive methods to hide their activity as well as their true intent. The trick will be to better understand the human points in these attacks. The intent or motivations of the attackers can range broadly including financial gain, revenge, political or hacktivism. Understanding these intentions can help shape our security strategies.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion